Recently, there were many controversies on Facebook, Whatsapp, Google related to data security in the market. These all big giants even claimed that they follow end to end encryption policy which basically runs under an algorithm of asymmetric cryptography. To prove that they are committed to our security, some of them signed the Confidential Computing Consortium. Last year, Google along with Microsoft including 8 other companies(Intel, Microsoft, IBM, Intel, Alibaba, ARM, Red Hat, Swisscom and Tencent) signed this consortium.
We believe that while data is transmit across the internet, CIA rule- Confidentiality, Integration and Authentication is being followed . To maintain all these factors, companies need to invest millions of dollars on their servers but many firms fail to do so and thus the end customer’s data gets compromised .
Another factor leading to failure in the security of the data is outdated software that are running on the company servers. Outdated software generally have many vulnerabilities and thus are not compatible with the running environment thus putting the data security of its users on risk. This allows attackers to steal the customer’s data which violates the Confidentiality, Integrity and Authentication rule of that data. So let’s see if this consortium is able to fulfill all the requirements that are required and committed for data security.
WHAT IS THIS CONSORTIUM?
The Confidential Computing Consortium is developed and backed up by the Linux Foundation. This consortium is introduced to define Confidential Computing. It enables services, software, hardware vendors and cloud providers to come together and work on the development of encrypting their customer’s data from one end to the another end. This means that any entity that signs this consortium will strictly follow some foundational services and frameworks that are confidential ,aware and minimize the need for trust so that customer can rely upon their services and can trust on the fact that data which is currently in use, was done keeping in mind that the confidentiality of data which is being transmitted and data which is at rest still remains confidential.
Enterprise that signs this consortium are committed to make latest technologies to enable easy development and management of enterprise-grade confidential applications and enable big enterprises to support an ecosystem of open sources technical projects that are focused on Confidential Computing as open source projects suffer lack of funding that ultimately affects their aim of providing end to end encryption of their customer’s data. One of the example for open source projects is Linux.
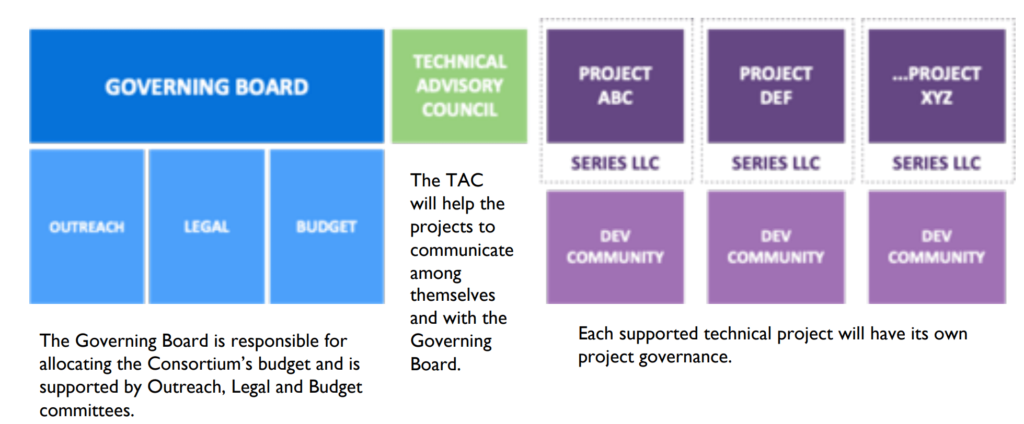
This consortium has membership level that defines the funding for the open sources. Memberships levels are defined as the Premier and General. As the name suggests, Premier member are responsible to appoint a representative to the Governing Board and Technical Advisory Council with annual membership fee of $60,000 while General member elect one representive to the governing board for every 10 general members with annual membership of $30,000. All the funds collected from these members are spent supporting these open source organization. This diagram explain all this in a better way:
CONCLUSION
Many organizations in the last few months have started signing this consortium. There is no doubt that this consortium ensures that every piece of data shared, is now confidential across the internet. It is better if this consortium is being signed by every organization who writes protection of their customer’s data in privacy and policy section. We have seen that some organizations in the past have played with privacy of their customers. At the end, it absolutely depends on the organization to follow instructions to what they are committed and ensures discrepancy of data shared between their severs and customer’s device.