One of the most popular Operating systems around the internet, Microsoft Windows, is know well known among developers, security researchers, attackers to test, build and execute their strategies. The most sophisticated reason for this is that, for over 2 decades, Microsoft has billions of users from tech as well as non tech background. The company has worked well on its vulnerabilities, loopholes and provide timely updates to its users that helps them to be in sync with the internet and has protected them from greater damages.
When it comes to security of windows operating system, it has a well known feature named Windows Defender. There is no doubt on the fact that windows blocks any malicious downloads from the internet. In the absence of explicit antivirus, this feature detects the unusual behavior of the installed application in your system. But somehow it has some restriction on dynamic behavior of the application and thus sometimes only updated antivirus or Intrusion detection system that can detect the malicious behavior through some advanced techniques are only able to provide protection on its users.
Great Deal: Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
Recently in the 4.18.2007.9 or 4.18.2009.9 version of the Microsoft Defender application, they introduced a feature of allowing its users to download any file from the internet through command line tools. As it is the feature of Windows Defender, it should protect the system from any harmful application but here seems that it does not. To explore this fact, let’s move to the next section.
DEFENDER COULD NOT ABLE TO DETECT MALWARE
As said above, these versions of the Microsoft Defender application allow users to download any file from the internet with a script MpCmdRun.exe, using a syntax like:
MpCmdRun.exe -DownloadFile -url [url] -path [path_to_save_file]
The MpCmd stands for Microsoft Malware Protection Command Line. The above command will enable the user cmd to start cloning or downloading files from the specified URL. Now as we all know, windows stop or restricts malicious content, its CLI utility should also do the same.
Recently, Askar, a security researcher, has found out that using this CLI utility, he can download any files that can be malicious also. Below is the screenshot of his POC:
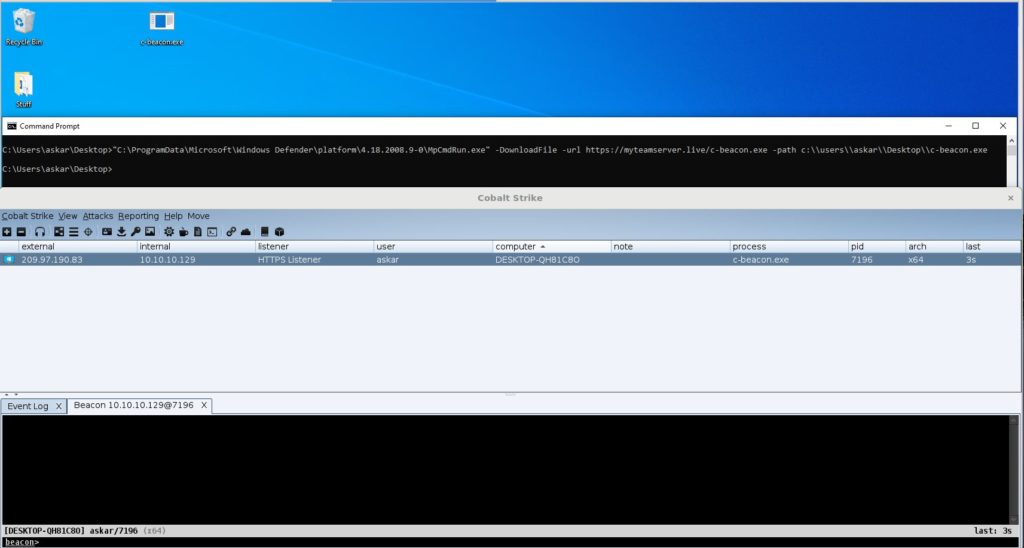
As can be seen above, he downloaded Cobalt Stike’s Beacon malware payload (one of the most famous cloud based service used by aggressive pentesters. Thus, allowing an attacker to launch the Living Off The Land attack. An attack where antivirus or intrusion detection systems becomes unable to scan or detect the files downloaded in the system.
CONCLUSION
From all above argument , it can be said that Microsoft’s MpCmd full form Microsoft Malware Protection Command line is ironical to its functioning. This proves the fact that not every product is designed to do the same function which it claims to do. This is a very critical vulnerability and it should be patched by Microsoft as soon as possible. Recently, we presented a similar article which allows user to download the malicious package request instead of requests from the official site of Pypi just by making a spelling mistake on the command line while cloning. Therefore, until Microsoft not release the patch of this vulnerability, we suggest our readers to not use or rely on this utility.
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.