Every cyber geek know this fact that 2020 has been the most promising year for bad actors. The number of cyberattacks have increased drastically this year if we compare from any other year in the last decade or century. In cybersecurity industry, we all see the largest DDOS attacks ranging upto 809 million packets per second recorded by Akamai. Also there are lots of other cyberattacks which took place, some due to vulnerabilities in systems, and some due to social engineering.
There are lots of data dumps, breaches and security bypass in this outbreak. The cost of data breaches is one of the most significant factors why most organizations, corporates and startups are not able to grow in this cyberera. The security of an infrastructure is absolutely dependent upon how much they invest in hardwares, softwares and IT team. Many tech giants have created resources that are cost efficient and manages all the above three parameters making it easy for anyone to follow their passion and startups in just matter of minutes. But still there are many who manages all the resources on their own.
Researchers from Sensecy- A Cybersecurity Intelligence company have conducted a research on ransomware attacks took place this year and analyzed 180 ransomware incidents from different industries.
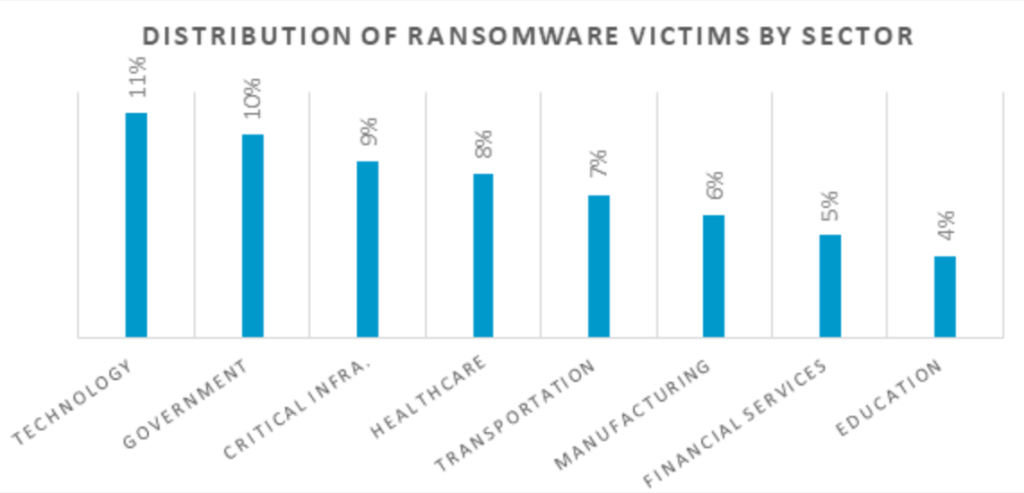
According to their research, all their analyzed incidents are caused mainly by 4 vulnerabilities. Let’s see what these vulnerabilities are:
THE VULNERABILITIES
1. CVE-2019-19781
This vulnerability was discovered in 2019 and was assigned to vulnerable Citrix Application Delivery Controller (ADC) to which after post exploitation, attacker can execute arbitrary code on the remote system. This vulnerability has been assigned a CVSS score of 9.8 which comes into the category of Critical vulnerabilities. The products which were affected due to this vulnerability:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds before 13.0.47.24
- NetScaler ADC and NetScaler Gateway version 12.1 all supported builds before 12.1.55.18
- NetScaler ADC and NetScaler Gateway version 12.0 all supported builds before 12.0.63.13
- NetScaler ADC and NetScaler Gateway version 11.1 all supported builds before 11.1.63.15
- NetScaler ADC and NetScaler Gateway version 10.5 all supported builds before 10.5.70.12
- Citrix SD-WAN WANOP appliance models 4000-WO, 4100-WO, 5000-WO, and 5100-WO all supported software release builds before 10.2.6b and 11.0.3b
According to researchers, the following ransomware attacks took place due to this vulnerability:
- Ransomware attack on Gedia Automative Group in January took place due to vulnerable Citrix products. The operators behind this incident were the REvil, also known as Sodinokibi group.
- DopplePaymer gang attacked on Bretange Telecom company in February 2020 by leveraging this vulnerability.
- Insurance company, Chubb suffered a cyberattack at the end of March due to this vulnerability. The cybercriminals behind this attack was the Maze Group.
- In June, Maze group again discover this vulnerability in servers of Coduent, IT services giant and exploit it to launch cyberattack on the giant. The June’s biggest attack on Indian finance giant, Indiabulls, later on investigation, later on investigation reported that the compay used vulnerable Citrix NetScaler ADC VPN Gateway.
Later on after one month of its discovery, the company released the patch and suggested its customer to update it soon.
2. CVE-2019-11510
This vulnerability was assigned to vulnerable Pulse Secure VPN which allows an attacker to take over the whole network and bypass the security infrastructure which is deployed into that network. This vulnerability has been assigned a CVSS score of 10 which is considered to be the most critical. According to researchers, some of the famous ransomware incidents that are caused due to this vulnerability:
- REvil group attacked the Travelex, a foreign exchange company using this vulnerability. They exploited this vulnerability in company’s VPN to gain domain admin privileges and used an open-source remote access software, VNC, to perform lateral movement on the targeted network.
- This vulnerability also helped attackers to gain access to IT infrastructed of healthcare and Black Kingdom had attempted to exploit this vulnerability to launch cyberattack.
On April 24, the company released a security patch for the same vulnerability.
3. CVE-2018-8453
This vulnerability was assigned to vulnerable windows component, win32k.sys. This vulnerability results in poor handling of objects inside the memory. This vulnerability has been assigned a CVSS score of 7.8 which makes its severity level as high. As this vulnerability resides in a component of OS, successful exploitation of this vulnerability allows an attacker to run arbitrary code in kernel mode, install programs; view, change, or delete data; or create new accounts with full user rights. Some of the famous ransomware incidents which were detected exploiting this vulnerability by the researchers:
- REvil ransomware operators exploited this vulnerability against Brazilian-based electrical energy company Light S.A. The group have previously used this vulnerability to launch attack in Asia-Pacific region.
Later in February 2019, Microsoft released the patch against this vulnerability.
4. CVE-2012-0158
This vulnerability was assigned to vulnerable Microsoft products which includes Microsoft Office suites and components, Microsoft SQL Server, Microsoft BizTalk Server and Microsoft Commerce Server. This vulnerability was on of the most exploited vulnerability in this decade and comes in everyone’s list of most exploited vulnerability. This vulnerability has been assigned a CVSS score of 9.3 which is close to critical. Successful exploitation of this vulnerability allows the attacker to remotely execute code on the victim’s computer through a specially crafted website, Office or .rtf document. Some of the incidents which were reported exploiting this vulnerability:
- This vulnerability was exploited against medical and academic organizations in Canada.
- This vulnerability has been used by HiddenTear ransomware family to spread the reign of terror.
Later on April 26 2020, Microsoft released the patch for all products against this vulnerability.
CONCLUSION
As we can see all the vulnerabilities are not new and organizations can easily have control over cyberattacks that are taking place through this vulnerability. We suggest, all the organizations, individuals who operate their own network to patch these vulnerabilities as soon as patches are already out so that they have a strong guard against the cyberattacks.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






