In this growing age of technology, humans are trying to automate each and every daily task. With each electrical appliance in your house is now been called by a word “smart appliance”, for a technology geek, he identifies it as Internet of Things(IOT). In simple words if we want to explain the IOT gadgets, then it can be just explained with this phrase: “gadgets with ability of networking” or more simply as the name is revealing itself the gadgets which are the part of internet. In order to communicate with other devices across the internet, these gadgets are discoverable by anyone, either they are good or they are bad actors.
There are wider range of gadgets across the internet. Some several low energy gadgets too exists in this wider pool that communicate via Bluetooth because they don’t operate on much power to transmit data over a wider range of network i.e. internet. For these low energy gadgets, they are several restriction on range of discoverability and the data transmission rate. If we see the technology around 10 years ago where the data packs are expensive and these advance apps were not introduced, for a middlemen, Bluetooth was the only way to transmit data. Though there are too several apps nowadays that operate the Bluetooth technology.
So coming across the evergreen technology Bluetooth, some researchers from Purdue University combined together and found out a security flaw in Bluetooth’s architecture that can make it vulnerable to spoofed attack such as Man in the Middle attack. Let’s have a deeper look about this flaw.
SECURITY FLAW IN BLUETOOTH’S ARCHITECTURE THAT EXPOSED MILLIONS OF DEVICES
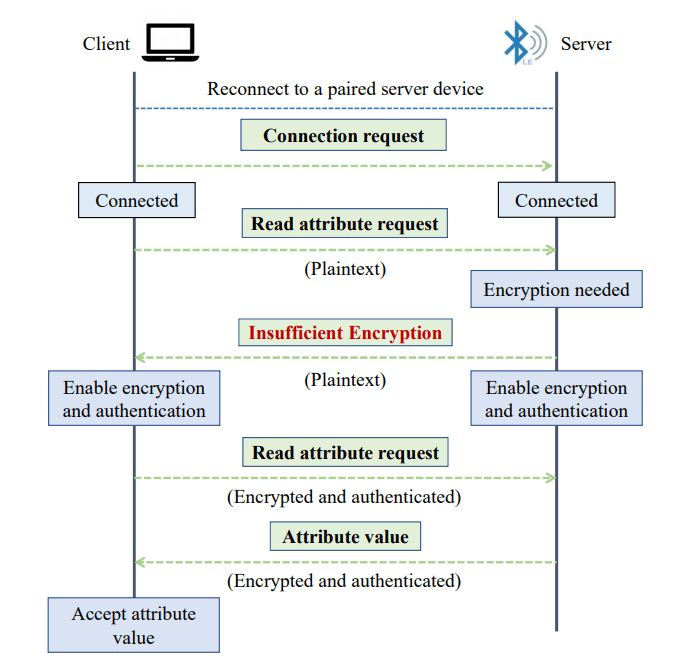
To understand the vulnerability, we first need to understand some basics about Bluetooth technology. At the core level, just as networking model, this technology too operates on the server-client model. The client requests the server for a connection and then upon exchanging information about some parameters, they exchange the require media or data.
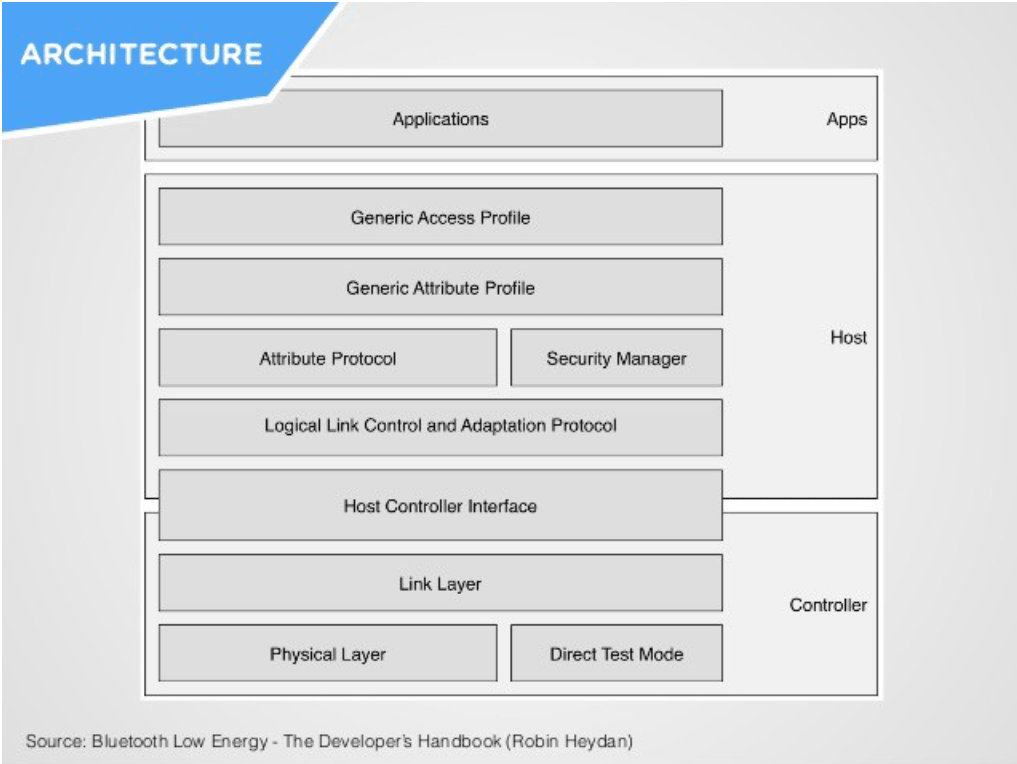
As you can see in the above diagram, this technology operates on Physical and Link layer which means that two parties communicate using MAC address. The server (device which the client wants to connect to) publicly broadcasts its information so that clients in its range can connect to it.
Now, the big question come here is, what’s the security? Does anyone can connect to it? Is there any encryption involved? Obviously yes, the security is very well maintained across the whole transmission. The word security here implies to Confidentiality, Integrity and Authentication of the users as well as the data exchanged.
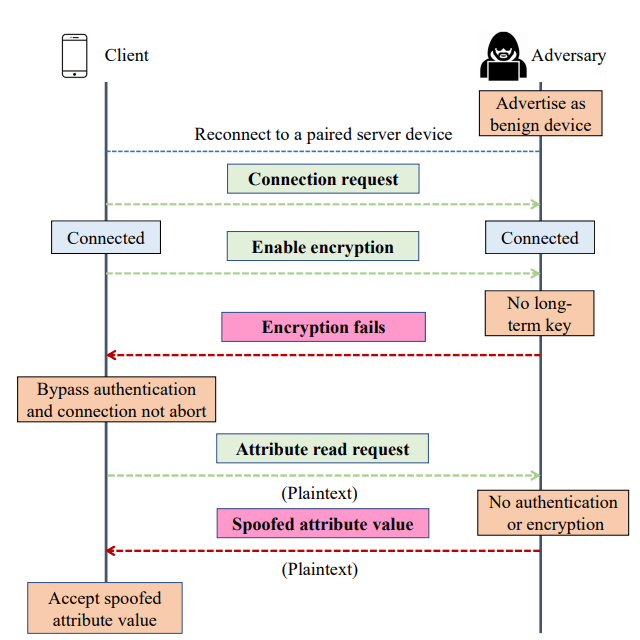
But as we all know due to its low range, the most common issue that everyone has come acrossed “Disconnected as the device is undiscoverable or low battery”. Again on coming in the range of server, the client again itself tries to connect to the server. But is the same security design followed again in the reconnection? Let’s have a look at the process of reconnecting with the same paired device.
As you can see the proposed model requires to enable encryption from both ends, it states upon failing to authenticate encryption, the client should either retry or abort the connection. But it is found that this model is not properly followed. Researchers found that when the encryption is not followed, the connection is not dropped rather data continues to be exchanged.
Their research shows that any attacker who is intercepting the communication between client and server can impersonate as the server as the whole communication is in plain text and can potentially cause damage to the client’s device. Upon requesting for the encryption, the attacker either denies it or send incorrect key that would terminate the encryption.
Researchers also demonstrated a video about their successful experiment on bypassing the authentication and encryption.
CONCLUSION
Several Bluetooth apparels and IOS and Android devices were found vulnerable against this vulnerability and researchers have already informed about this to the concerned authorities to improve their design. At the end, we at Ethical Debuggers suggest our readers to not rely more on this technology until further improvements and if you are, then try to reduce your reconnection attempts as much as possible.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.