In this pandemic, the startups have excessively grown across the world due to millions of people losing their jobs across the world. Individuals having small amount of investment with them have put it all in their new startups thinking that they can make something big. There are no doubts that future of a startup is totally dependent upon the type of idea. Every idea is not big but sometimes resources provided to that idea make it a super hit. Tech giants like Google, Microsoft, Alibaba support many startups financially but their investment to startups totally depend upon what idea does an individual have? How much knowledge does he/she have about that idea? Thus many individuals could not make up to mark and thus miss that opportunity.
In the last decade, we have seen how the affiliate marketing have taken a surge. The affiliate marketing is a great concept which makes profit for both the individual as well as an organization. An advanced version of this marketing which many organizations are running is by providing all resources to setup a business and earning a particular amount of commission on each sale from the individuals, thus can be referred to as Software as a Service. From this concept, both the organization as well as individuals make the profit:
- For individuals, they have their business established with zero investment.
- For organization, they make commission on each sale made by that individual.
A similar concept has been observed to be run by Smaug ransomware operators, as observed by researchers from Anomali Threat Research.
The researchers revealed that the one of the members from the team, Corinda, of Smaug ransomware operators posted on the Exploit.In (a famous hacking forum) about this concept with the contact information as smaug-ransomware@protonmail.com.
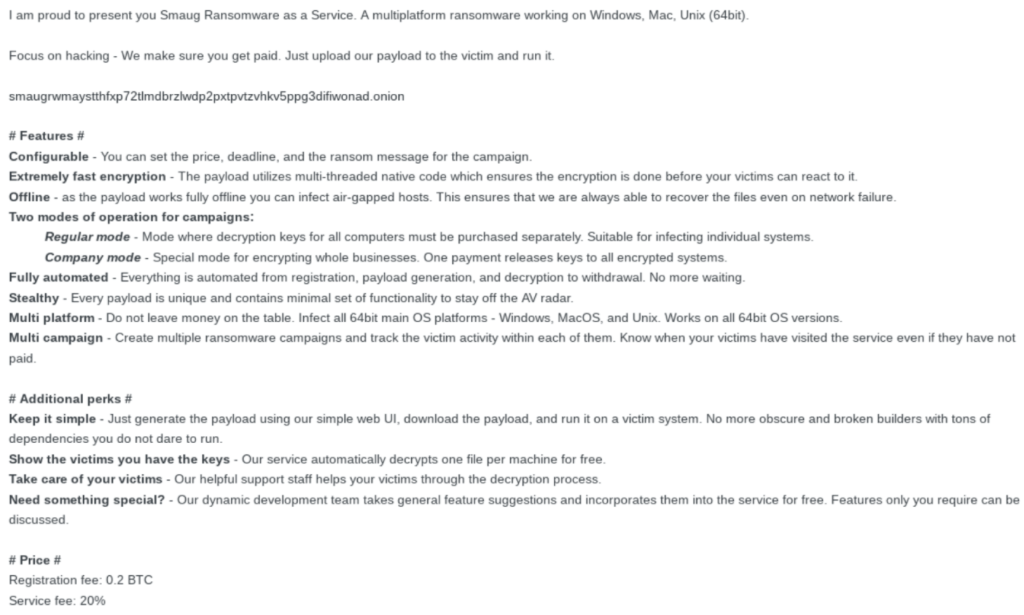
FACTS ABOUT CONCEPT AND THE RANSOMWARE
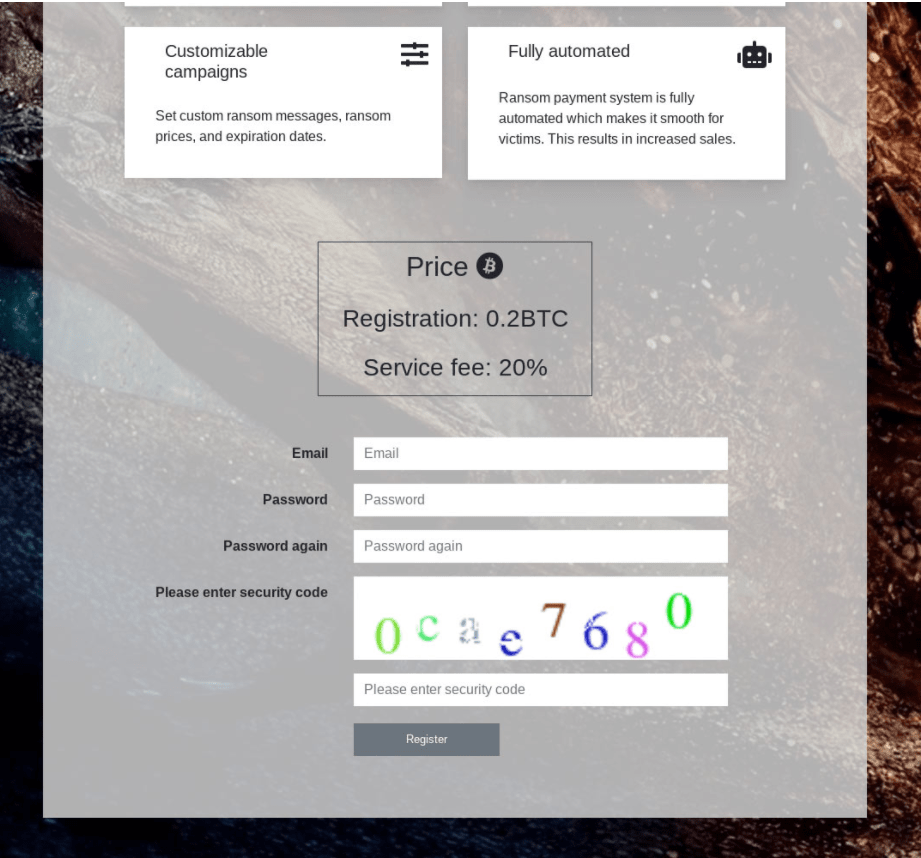
Finally, when the user decides to setup its own ransomware business, he/she is redirected to a site where the individual is required to sign up an account to avail the services with a registration fees of 0.2 BTC.
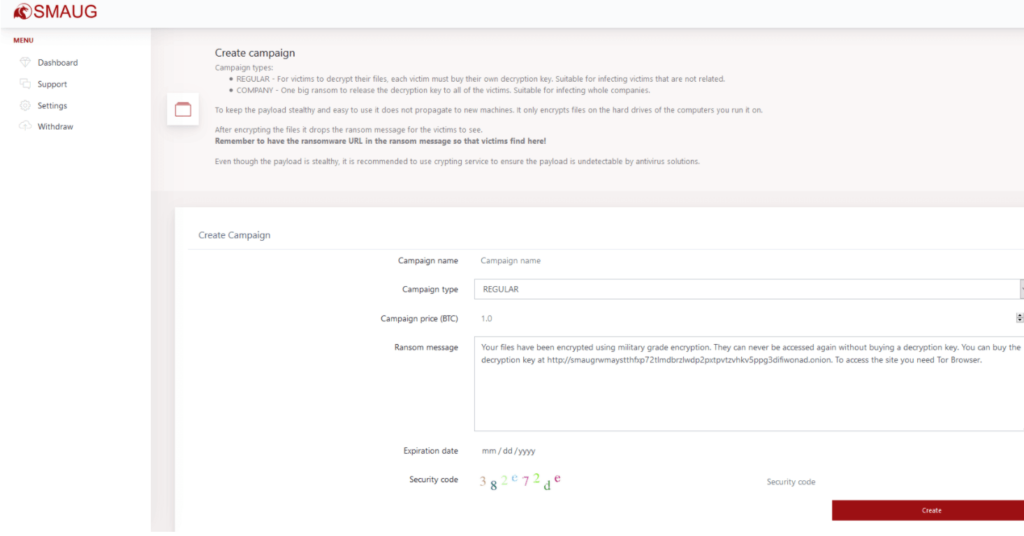
After the user has successfully sign in to his account, the individual will be given privileged access area where he/she can create campaigns (design phishing methods to deliver ransomware into the victim’s server), manage withdrawals (ransom collected by the victims), manage dashboard (to view overall activity of the account) and support from the operators.
The special fact about this ransomware is that it is written in Golang language which makes it really efficient to make a powerful ransomware in just 300 lines of code.
The ransomware uses the repeated encryption and makes use of both symmetric(AES) and asymmetric(RSA) algorithms to encrypt the system files. The malware which infects the system, generates a unique AES key for its new victim which is then further encrypted by hard coded RSA public key of the attacker.
After the malware is into its action, it uses a pair of “goroutines“ for each disk partition for the encryption of files. The first goroutine compare the files which will be encrypted from the programmed list of extensions in the malware.
*.3fr*.accdb *.aes *.ai*.ARC *.arw *.asc *.asf *.asm *.asp *.avi *.backup *.bak *.bat *.bay *.bmp *.brd *.c *.cdr *.cer*.cgm *.class *.cmd *.cpp *.cr2 *.crt *.crw *.csr *.CSV *.dbf *.dch *.dcr *.der *.dif *.dip *.djv *.djvu *.dng *.doc *.DOC*.docb *.docm *.docx *.dot *.DOT *.dotm *.dotx *.dwg *.dxf *.dxg *.eps *.erf *.fla *.flv *.frm *.gif *.go *.gpg *.gz *.h*.docb *.docm *.docx *.dot *.DOT *.dotm *.dotx *.dwg *.dxf *.dxg *.eps *.erf *.fla *.flv *.frm *.gif *.go *.gpg *.gz *.h*.html *.hwp *.ibd *.indd *.jar *.java *.jpe *.jpeg *.jpegm *.jpg *.kdc *.key *.lay *.lay6 *.ldf *.max *.mdb *.mdf *.mef*.mid *.mkv *.mml *.mov *.mpeg *.mpg *.mrw *.ms11 *.MYD *.MYI *.nef *.NEF *.nrw *.odb *.odg *.odm *.odp *.ods *.odt *.orf*.otg *.otp *.ots *.ott *.p12 *.p7b *.p7c *.PAQ *.pas *.pdd *.pdf *.pef *.pem *.pfx *.php *.png *.pot *.potm *.potx *.ppam*.pps *.ppsm *.ppsx *.ppt *.PPT *.pptm *.pptx *.psd *.pst *.ptx *.py *.qcow2 *.r3d *.raf *.rar *.raw *.rb *.rtf *.RTF*.pps *.ppsm *.ppsx *.ppt *.PPT *.pptm *.pptx *.psd *.pst *.ptx *.py *.qcow2 *.r3d *.raf *.rar *.raw *.rb *.rtf *.RTF*.rw2 *.rwl *.sch *(Security copy) *.sldm *.sldx *.slk *.sql *.sqlite3 *.SQLITE3 *.sqlitedb *.SQLITEDB *.srf *.srw *.stc*.std *.sti *.stw *.svg *.swf *.sxc *.sxd *.sxi *.sxm *.sxw *.tar *.tar.bz2 *.tbk *.tgz *.tif *.tiff *.txt *.uop *.uot*.vbs *.vdi *.vmdk *.vmx *.vob *.wav *.wb2 *.wks *.wma *.wmv *.wpd *.wps *.xlc *.xlk *.xlm *.xls *.XLS *.xlsb *.xlsm*.xlsx *.xlt *.xltm *.xltx *.xlw *.xml *.zip
After the required files have been scanned they will be encrypted in AES CBC mode in which block ciphers are used to make it harder to decrypt. The files are encrypted 4k bytes at a time and if the file is found to be smaller, the malware adds padding to the end of the file to make the total bytes a multiple of 16 bytes as required by AES.
At the end when the encryption of file gets completed, a ransomware note, HACKED.txt is left with the encrypted files guiding the victims on how they can decrypt their files.
“Your files have been encrypted using military grade encryption. They can never be accessed again without buying a decryption key. You can buy the decryption key at http://smaugrwmaystthfxp72t1mdbrzlwdp2pxtpvtzvhkv5ppg3difiwonad.onion.To access the site you need Tor Browser.”
CONCLUSION
The above activity states that cyber criminals are actively searching for individuals to spread their reign of terror. Due to the pandemic, insecurity of jobs and lack of opportunities available to the individuals, this situation is helping cyber criminals to actively spread their arms to influence the victims.