In last 6 months, COVID-19 has make all of us to believe on the fact that no surface is absolutely safe to touch. As a result, people had to adopt new normal in order to survive and earn living. Welcoming this new normal, we all have learnt to abide on two most important rules which are:
- Social distancing.
- Conduct contactless meetings as much as possible.
Therefore, anyone who has still not adopted the new normal is considered to be of no use by the society.
If we talk about new normal in context to payments and transactions, obviously cashless or plastic payments have become the priority over cash payments. From last decade, many people have already move forward and some are learning to make payments online or by paying through their debit/credit card on POS machine. As technology is getting more advanced dayby day, there is a need for more sophisticated transaction model which requires less time. Then, researchers further worked and developed a new system of making payments through contactless smart debit/credit cards using EMV protocol which stands for Europay, Mastercard and Visa card. This protocol is also a standard for non-smart debit/credit cards which use a traditional method of swiping the card on POS machine to make the transaction. Nowadays, this contactless POS terminals can be seen widely in modern merchant stores and ApplePay, GooglePay and other reputed merchants also implement it. Let’s overview the technology.
KNOWING THE TECHNOLOGY
This method of contactless payment is a widely used method in United States, UK and many other European countries. This method allows the user to make transactions using the Near Field communication or Radio Frequency Identification which means that the card has to be placed atmost distance of 4 cm near the POS machine in order to make this method function and the transaction takes place without any PIN or verification method. But there is a limit on the amount upto which you can transact after that you need to provide a PIN to transact a bigger amount.
Many questions were raised about the security mechanism about this technology that it transacts a limited amount without any verification which were later answered by experts that it is done using unique cryptographic tokens involved in each transaction that are generated randomly and are specific to the session. But what about the PIN verification in bigger transactions?
The answer to that is very simple yes. To be honest, we won’t go deep into cryptography which is taking place behind the scenes because that is absolutely out of scope for this article but we assure you will acquire knowledge to understand the vulnerability in the technology.
In a contactless payment model, there are three parties participating in the transaction.
- Card
- Terminal or POS machine
- Bank
In case of online transactions, the terminal authenticates user via PIN verification method either One Time or ATM PIN whichever configured whereas in offline contactless transaction wherever authentication is needed, the user needs to follow the same steps i.e to undergo a online PIN verification to authenticate the transaction. Therefore, the card needs to instruct the terminal or POS machine that it needs to contact the respective bank for user authentication.
If we want to understand the above statement in terms of communication, then the terminal will send the GET PROCESSING OPTIONS in which card has to reply a 2-byte data field which are Card Transaction Qualifiers that instructs the terminal to perform a particular type of authentication test for the user. Remember, till now this is an offline transaction using Near Field Communication technology and further upon receiving the behavior of response in the Card Transaction Qualifiers, it may become an online transaction as it needs to contact the bank for verificaton. The below diagram will best explains you the whole EMV transaction involving cryptographic tokens.
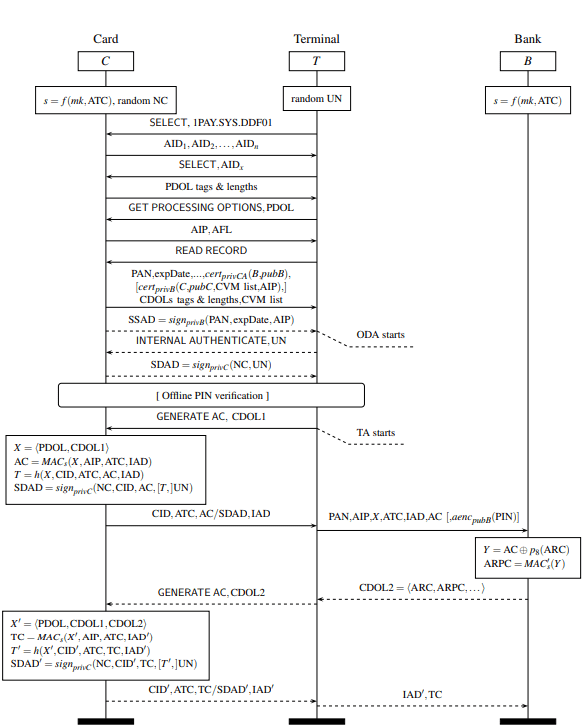
As you can see in the step 12 of the above diagram, after exchanging some prerequisite information on cryptography, terminal sends a command GET AC (GET Application Cryptogram), a Card Transaction Qualifier which instructs the terminal to perform further actions.
According to researchers, David Basin, Ralf Sasse and Jorge Toro-Pozo, Department of Computer Science, ETH Zurich there exists a flaw in this design for Visa contactless card payments. Let’s see the flaw.
FLAW IN VISA CONTACTLESS TRANSACTIONS
According to their analysis, researchers said that in Visa cardless transaction, the card does not authenticate the Application Cryptogram (AC) to the terminal. What it means that terminal does not get the AC in reply to GET PROCESSING OPTIONS and therefore bank does not know about what is happening between the two parties, the attacker can easily launch a Man-In-The-Middle Attack modifying the information transmitted from the card to terminal saying that “Hey terminal, online PIN verification is not required. Consumer Device Verification was already performed, you can consider it as a verified transaction.”
In terms of communication, the attacker needs to modify the following:
- Clear the 8th bit in first byte of the Card Transaction Qualifier.
- Modify the 8th bit in second byte of the Card Transaction Qualifier.
As a proof-of-concept, the researchers demonstrated this attack by developing an application that will exploit this flaw in visa cardless transactions.
This attack requires the following components:
- Two Android smartphones,
- A dedicated Android application (the specialists developed it themselves), and
- A contactless Visa card.
One smartphone will be running the POS emulator of that application and is placed in the vicinity of the victim’s card and the other smartphone will be running the Card emulator and placed near the terminal. The demonstration of the attack can be seen below:
The screenshots of both smartphones while executing the attack is shown below:
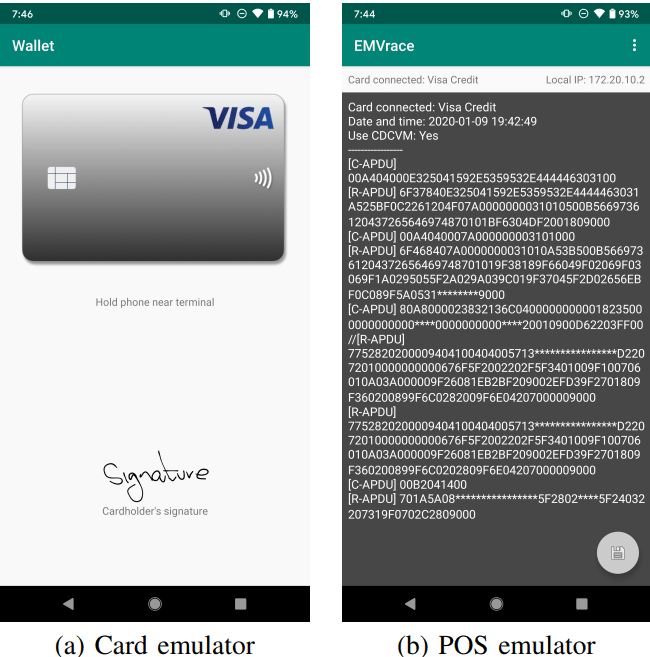
As you can see on the POS emulator, the attack has successful set CDCVM parameter to Yes which verifies the whole transaction, given that bank cannot verify its correctness in that session due to offline mode. Later, after the session ends, when the verification does not match with the bank, it could not deny the transaction as terminal has accepted and verified the transaction with the cardholder.
CONCLUSION
Thus, due to this vulnerability in the Visa contactless transactions model, the ideal diagram for EMV transaction can be replaced with the diagram as shown below:
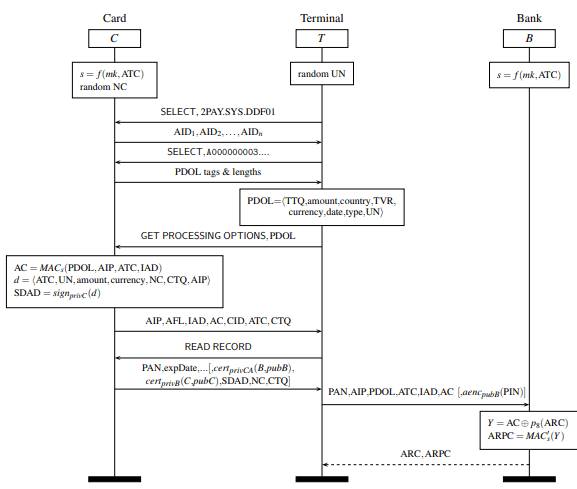
Thus it is suggested that contactless Visa contactless smart cards are not safe to use till further implementation on its security design. We recommend our readers to rely more on other online mode for safe transactions.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






