During, this worldwide outbreak, the attackers have emerged with lots of phishing attacks, some of which can be easily detectable and some are even not detectable. There are some attackers who create wants to create a backdoor into your system and there are some who are just restricted to stealing your information between your communication to the server.
If we see our records of doing attacks, the top names are always Chinese and Russian. The actors from these communities are heavily engaged in launching attacking around the world for more than a decade. Some big tech giants obviously have some amount of system guards present there that makes it a little difficult to crack, but all known middle or lower companies, were being bullied and are still getting bullied by these attackers either they are people itself working in that organization or are customer from that organization.
Today, in this article we will talk about attackers from another community which is well known to various malicious campaigns in the past and now it has regain its presence with a new technique of attacking its victims and launch malware into their systems. The researchers who explored this attack are people from Kaspersky.
As founded by the researchers, these attackers attack their victim with four kinds of banking torjan Guildma, Javali, Melcoz and Grandoreiro and thus the total number of trojan they used is 4, they named it as the Tetrade. Let’s analyze the anatomy of their attack:
ANALYSIS OF THE ATTACK
As mentioned above these attackers use tetrade family to attack their victims, most of their campaigns contained a file that executes a script to download a payload(banking trojan) from the Command and Control server which will communicate with the attacker and creates a backdoor in the victim’s system. Though they are end motive is same but their methodologies differ from each other. Let’s learn about them one by one:
GUILDMA
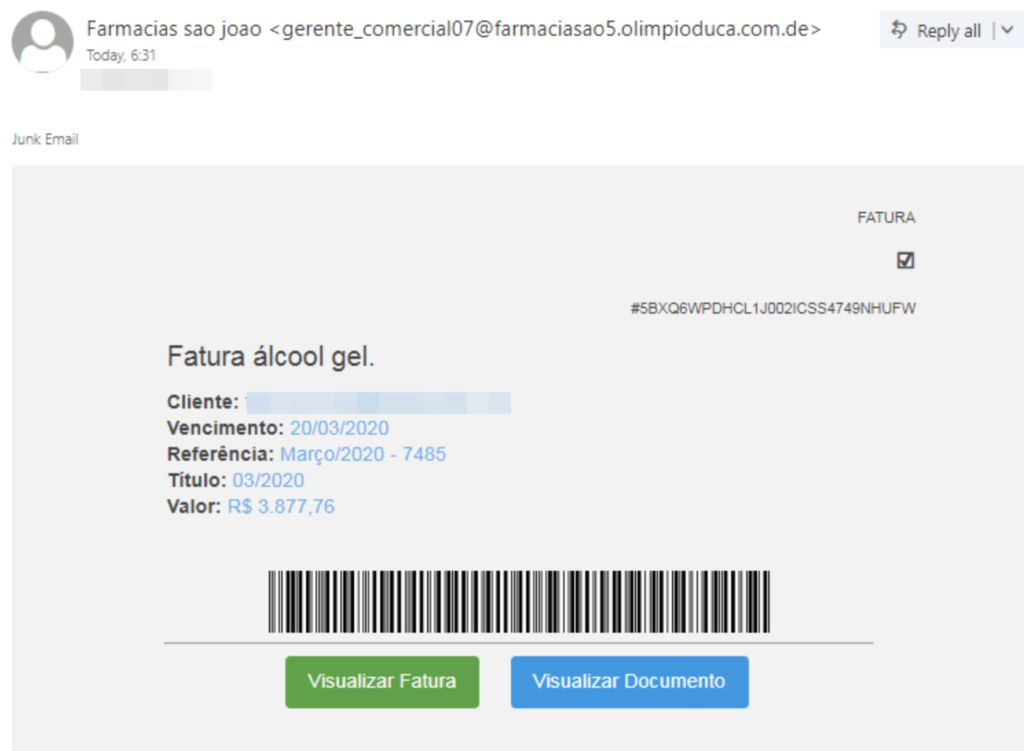
This operators behind this banking trojan will first send a phishing email which contains an attachment that will of the type ranging from Visual Basic Script to LNK which is a malicious payload that will download the malware from any of the links mentioned below:
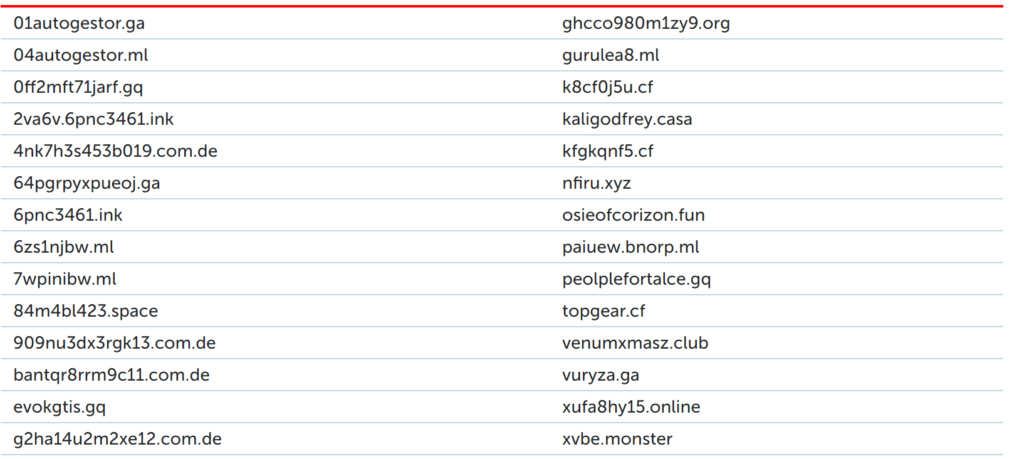
Then after installing into the victims system, it stores the malicious file in the system using Alternate Data Stream to remain undetectable in the system. Then it executes further in stages.
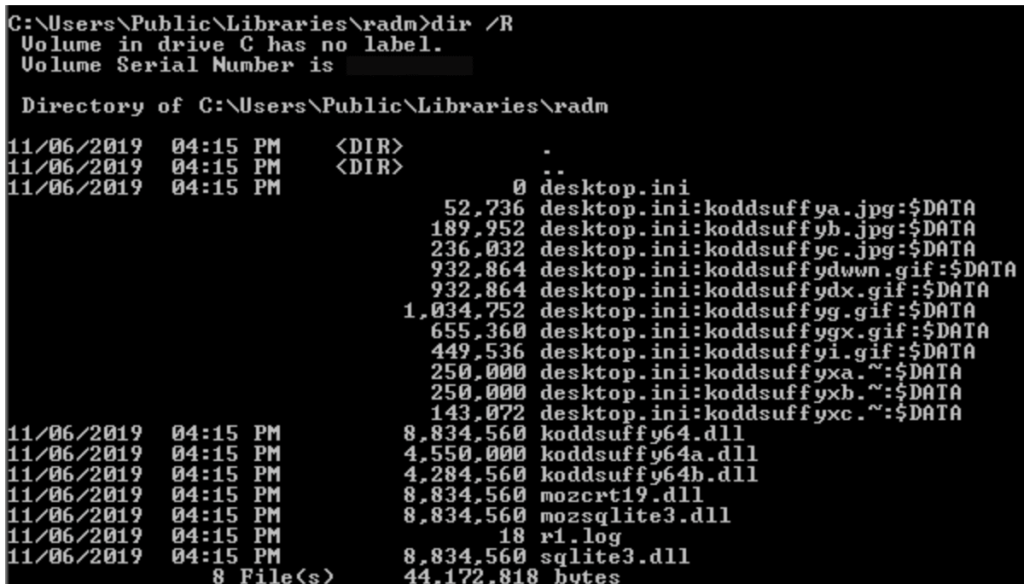
Then after loading some required DLLs and checking the environment, the malware then checks environment if it is under any restriction i.e either in a virtual environment or using any anti-detection tool. Then finally if everything goes fine, it executes the malware and creates a backdoor in the victim’s system.
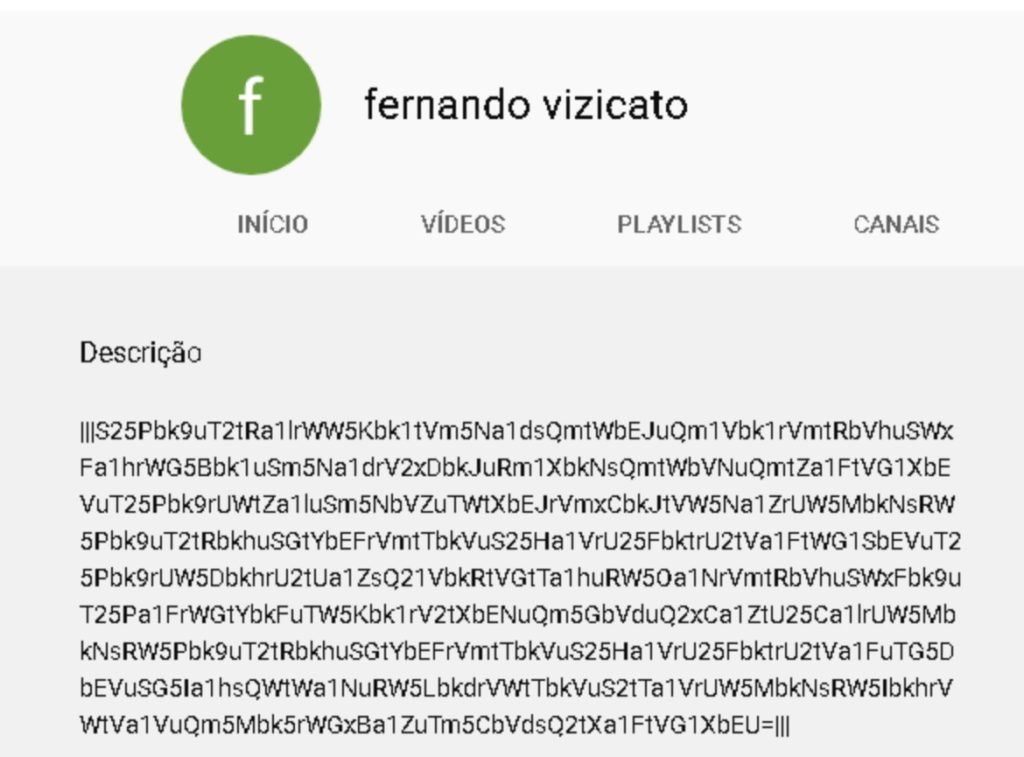
The interesting point here is that Command and Control server that this server uses are the basic Youtube and Facebook Pages that will contain information about the malware operator through which victim can easily control the victim’s system. The attacker can do following activities:
- full control over page navigation through the use of a VNC-like system.
- toggling screen overlay.
- requesting SMS tokens.
- QR code validation.
- requesting transaction.
JAVALI
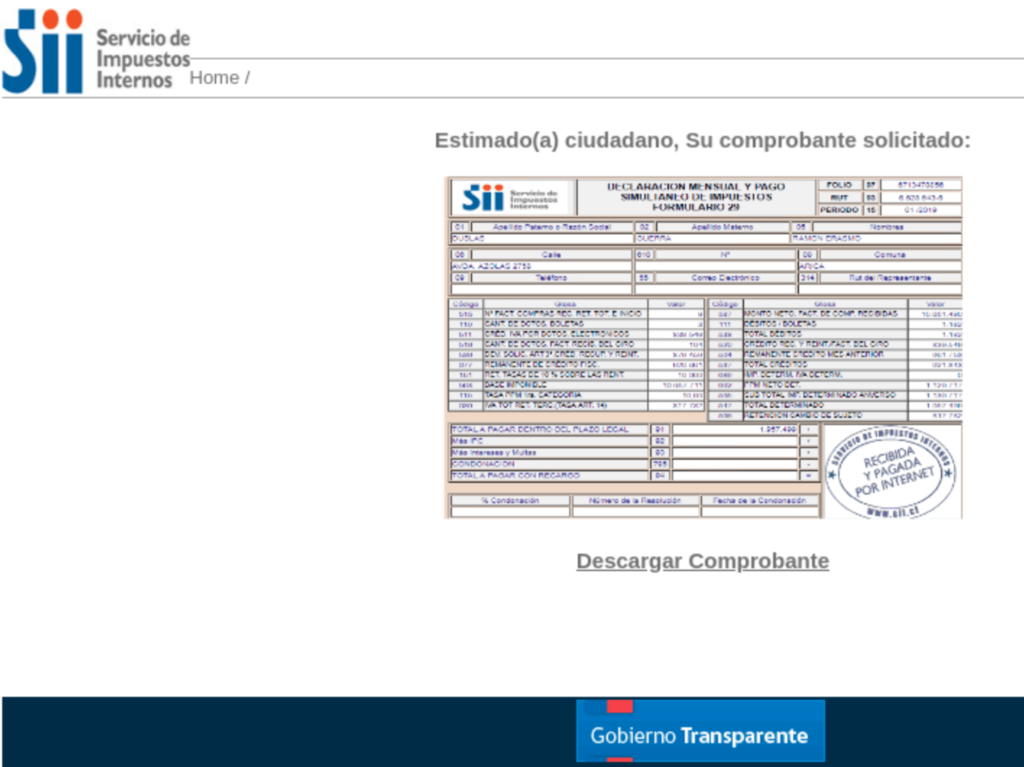
It is the malware that targets victims in Mexico and Brazil. They use the same phishing email campaign which contains a MSI (Microsoft Installer) file with an embedded Visual Basic Script. This script contains instructions to download the actual malware from it Command and Control Server. The malicious file then downloaded is with a .zip extension that contains a obfuscated 602 MB of DLL. The actual DLL inside this is just of the size 600 kb. The larger size is to avoid detection.

Then after finally the malware is settled into the system, it will read instructions from a shared Google Document that will make the infected system to communicate with their Command and Control Server.
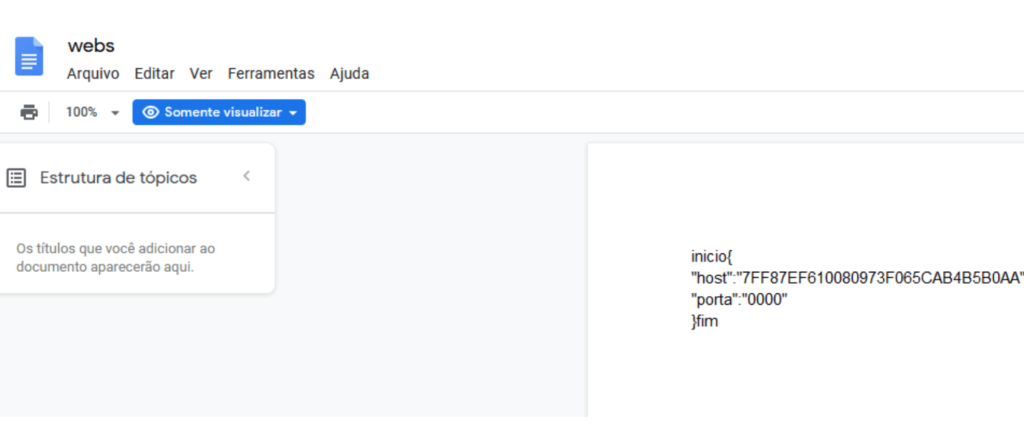
The melcoz uses exactly the same methodology to attack its victims. It uses a technique of DLL hijacking and AutoIt loader script to load malicious DLL and execute scripts.
GRANDOREIRO
This banking trojan uses ad campaigns and hacked websites to deliver malware into the victim’s system. From a hacked website, it will urge user to download a malicious installer that will either contain a malicious DLL or a VBS script that will have instructions to download the final malicious payload into the victim’s system.
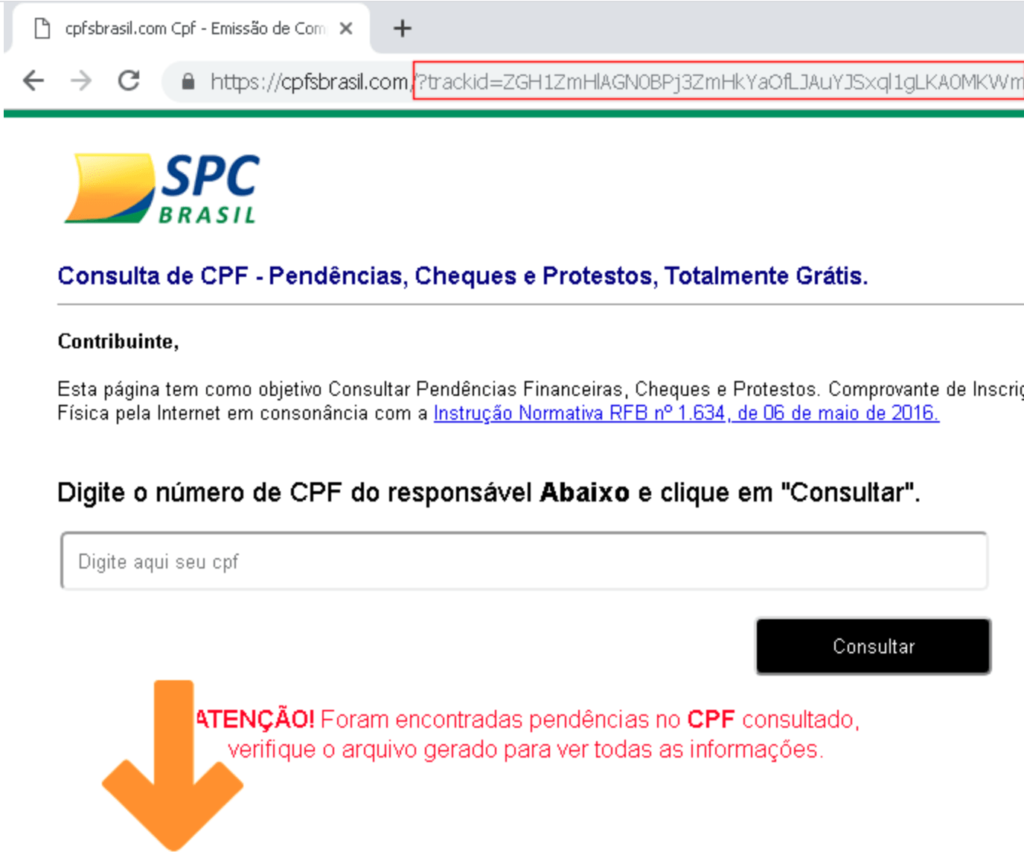
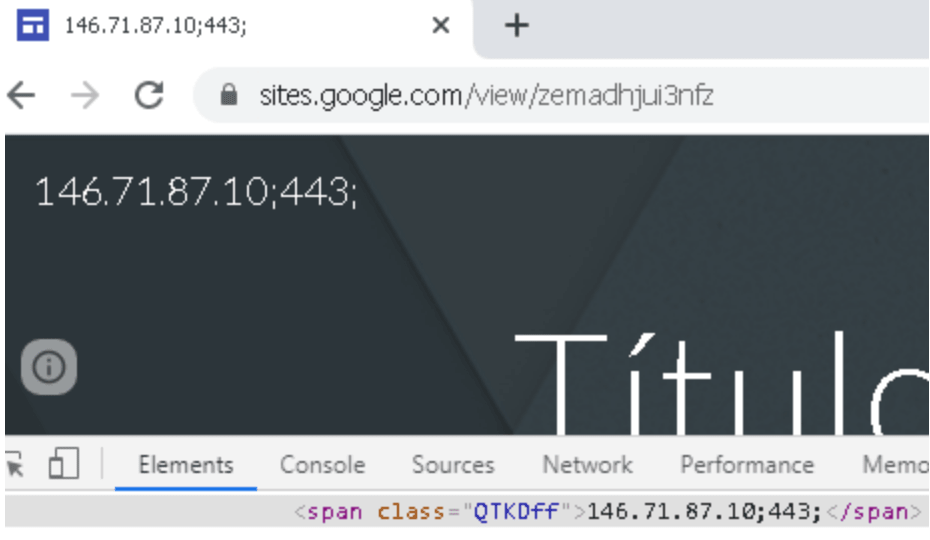
The automate code inside the malware will execute and evaluate google site path which have the instruction to contact the command and control server from where the attacker can easily control the victim’s system.
CONCLUSION
This tetrade family of trojans targets its victims ranging Brazil, Chile, Mexico ranging from other European and Eastern Countries worldwide. To get isolated from these attacks:
- Do not engage with any of the unauthenticated emails you doubt.
- Check URL of the site on VirusTotal before entering any important information.
- Disable Javascript in your browser for the websites you don’t trust.