We all believe that startups and own businesses are the safest option towards a brighter future. There is no doubt on this fact that worldwide pandemic in the past few months has even prove this statement right. Due to decline in economy, many people have lost their jobs and some have lost their life also.
One thing that we all can see and learn is that big names like Google, Alibaba, Amazon, Facebook, Microsoft, and many more have launched a variety of schemes that helped many individuals in growing their startups more rapidly. Some of the schemes include launching free advertisements for new startups, providing free cloud hosting, and sometimes investing money also. But not everyone has used it ethically. In this article, we will drive you with some examples in which the threat actors have used these services in a wrong manner and commit cybercrimes by bypassing the AI security layers set by Google, Microsoft, and Facebook and launching large scale phishing campaigns as researched by some experts from ThreatNix.
THE FAILURE OF GIANTS
The threat actors made the use of Facebook Ads to launch their phishing campaigns in the community. We all know that Facebook has billions of users now including Whatsapp and Instagram. Using this idealogy of launching phishing campaigns in such a large community, they used Facebooks Ads to drive a large number of victims.
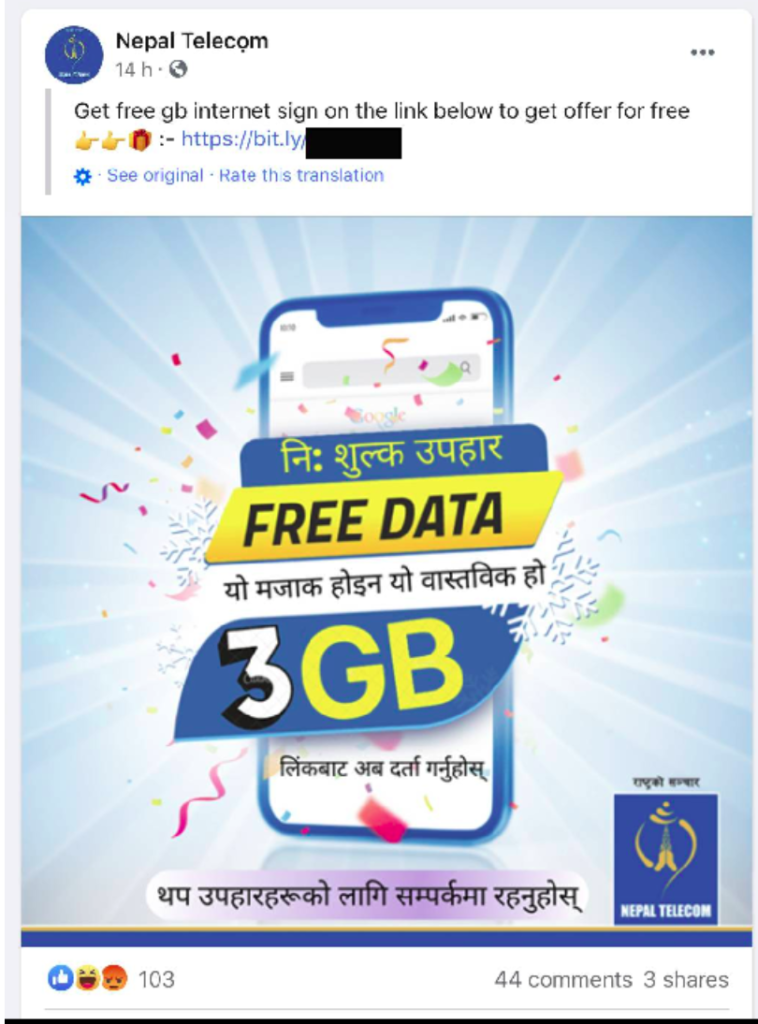
In the given advertisement, the criminals impersonated legitimate operators from Nepal Telecom and posted a link that looks like a legitimate Bitly link. Nowadays, even authenticated links are shortened using Bitly to give more rise to their brand value. Thus, it becomes very difficult for a normal user to identify the difference between legitimate and fraud links.
After a normal user clicks on the given link, the user is redirected to a static web page hosted on Github (Microsoft undertaking) which asks the user to enter the login credentials to log in. As a practice, users have such a habit to give credentials to third-party apps to avail the benefits. Moreover, for such a normal user, it becomes even more difficult to detect a difference between a static or a dynamic page. An example of such a Github hosted page is given below:
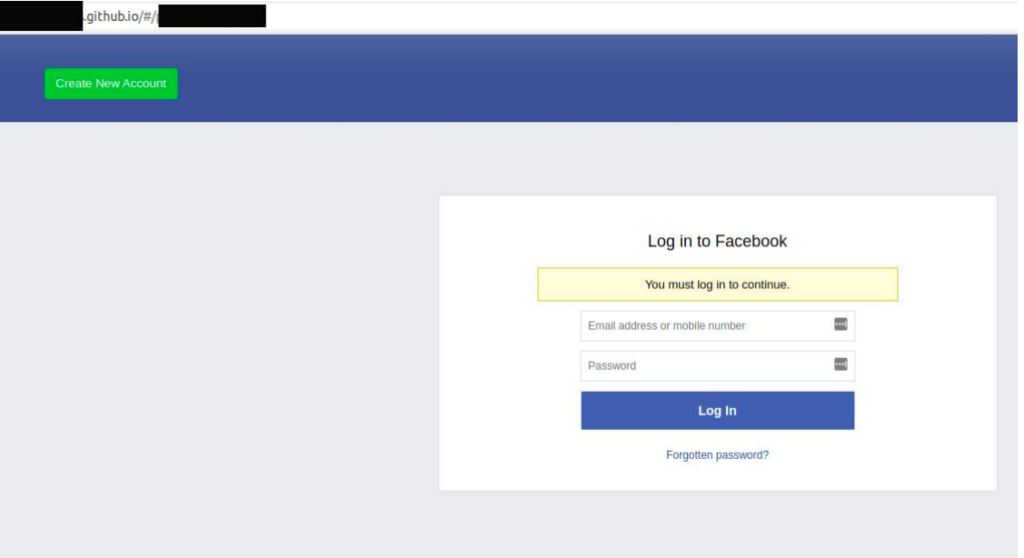
As soon as the end-user enters the credentials on the above page, the credentials are forwarded to the criminals Command and Control Server which is hosted on GoDaddy. It has been come into notice by the ThreatNix researchers that the login credential page also forwards to the Firebase storage account which is a Google subsidiary.
Researchers have also identified some Github repositories behind these phishing campaigns. Though Github has already disabled some of those illegal pages some recent accounts were seen committing this crime!

They were also able to dig into the C&C server and were successful in digging out some fruitful informations i.e. a list of 615,000 entries which is increasing rapidly.

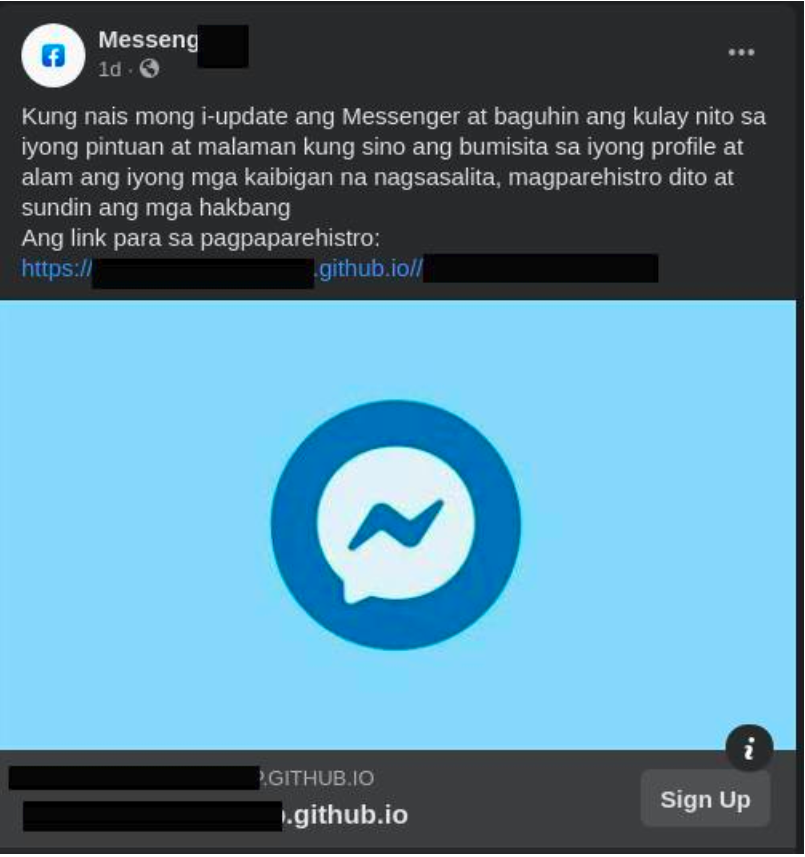
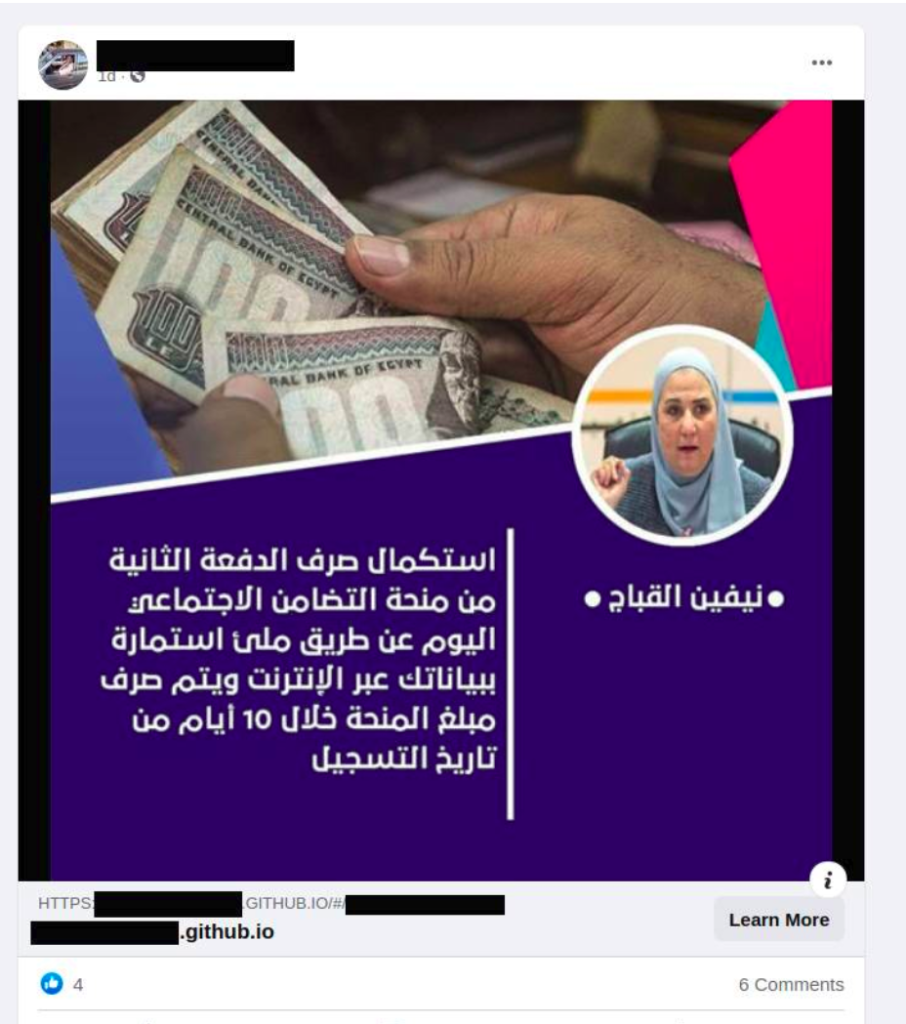
Some other ad examples are shown below:
CONCLUSION
According to the researchers, this phishing campaign has affected users from countries in Asia as well as some European countries. They have also informed the concerned authorities for further action
We at Ethical Debuggers suggest our readers to take following actions in order to prevent such kind of attacks:
- Avoid giving access to third-party apps. If necessary, only give access to authenticated and reputed apps.
- Do not use a common account or password for all your online activities
- Your password should be strong enough so that it does not appear in the attacker’s brute force list. Check our tools section to generate a strong password.
- Never click on links that look suspicious. Always check the legitimacy and authenticity of the links you are surfing before entering any information.
- Do not enter your credentials on an unknown device.
- Make sure you are connected to a secured network. If you doubt it, use a VPN for a more secure environment.
Some great deals to check out for:
- Become zero to hero in cybersecurity using this The A-Z Cybersecurity Developer Bundle which contains more than 170 hours+ of instructions from reputed trainers at just $39.99. To buy or know more about this deal, click here. Original Price: $999
- Protect your online security with Nord VPN and Nord Pass Manager. Buy a 2-year subscription for this combo at just $99.99. To buy more or know more about this deal, click here. Original price: $406
- Protect your system with Heimdal™ Thor Vigilance: Next-Gen Antivirus at just $39.99 for 5 years. To buy it, click here. Original Price: $249
Disclaimer: The above-suggested deals are from third-party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






