In our mailing system, we have a category of spam in which our client automatically filters a mail in which it finds the sender’s email address to be blacklisted by us or it is globally set as spam in its database. Tech giants like Google, Microsoft are really working for years to identify the spam messages . Many believe that scammers and spammers have the same meaning but in actual there is a difference as well as a similarity between them. People belonging to both groups will send scam emails that are unwanted for you but scammers will send you messages that are really harmful for you and can overtake your privacy.
For scammers, there are two primary sources from which they can hijack your privacy, phishing and vishing. These both techniques are based on social engineering attacks and recently we presented you some obfuscated phishing attacks that are successful in running malicious campaigns for users. From the last few years, cybersecurity companies are just deploying AI algorithms, Machine Learning to automatically detect and stop the phishing campaigns but one thing which is yet left unexplored is to how to stop these vishing attacks?
Similar to phishing, vishing attacks are the attacks in which an attacker uses his social engineering techniques to make the victim fall into his trap by calling him. Most of the vishing attacks run by the attackers are the automated robocalls. These scams are really unstoppable and growing day by day.
Some researchers from North Carolina State University took 11 months to analyze the attacks and developed strategies on how they can detect and stop these attacks. Let’s analyze their findings.
EXPERIMNETING THE CALLS
As a setup, they set a Telephony honeypot in which they configured 66,606 telephone lines and divided them into subsequent pools for different tests. They setup call recording hardware and automatic instructions for every call ,their telephone network received. Their network looks like this:
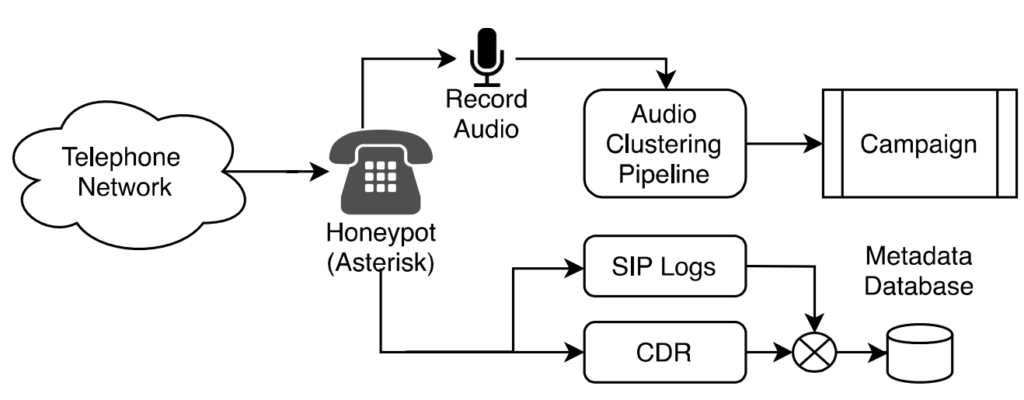
All these 66,606 telephony or inbound lines they had, contains 9,071 abuse numbers which means that these are some of the malicious or blacklisted numbers. They tested all the clean as well as abused numbers in a period of 11 months that is from March 2019 to January 2020.
The interesting part of this investigation is that these 66,606 numbers are asterisk numbers and are not exposed or known by anyone still these numbers received 1.5 million of total calls in this period with an average of unsolicited calls received every 8.42 days. It was an interesting finding that 77.83% of all unsolicited calls ,their honeypot received are from clean numbers which is a large portion of 57,535 numbers. Most of the unsolicited calls their networks received are in working hours or in week days and received minimum unsolicited calls on weekend i.e Saturday and Sunday. This clearly justifies the fact most scams occurs in banking or corporate hours.
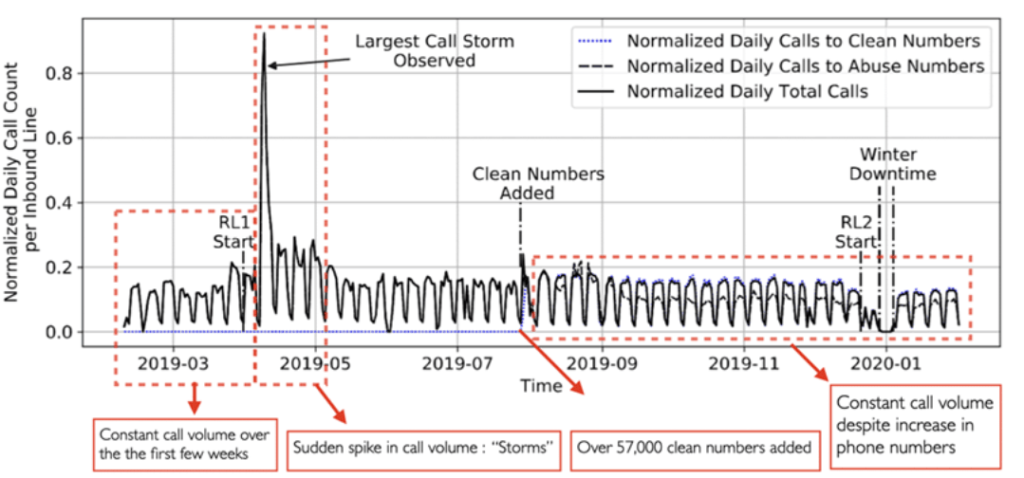
6.12% of all unsolicited calls that their honeypot received used Call spoofing attacks which used a technique of neighbor spoofing. In this attacker, caller or scammer changes their area code of calling and act as if they are calling from an area identical to you.
It was an interesting fact that all unsolicited calls which were received to the honeypot are not only robots. There were real people behind it as well. Researchers analyzed clusters of recording received to them and they developed an algorithm that have similar voice or a piece of recording in the whole sample.
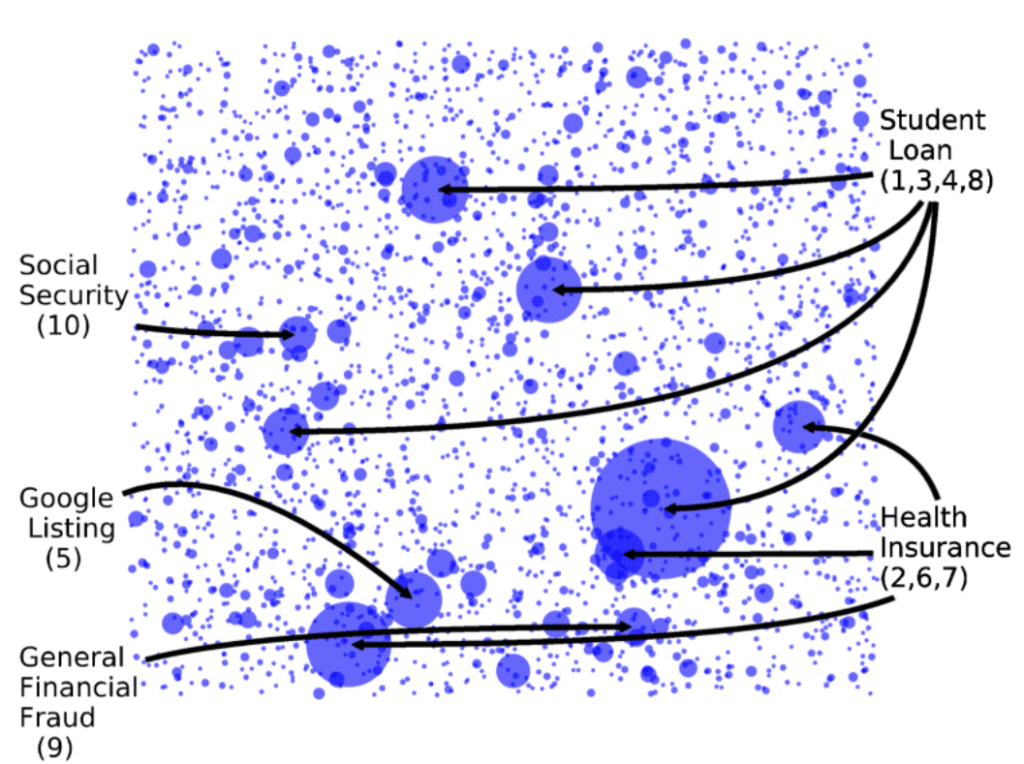
They recorded approximately 10% (about 150,000) of the received robocalls, which were then analyzed to determine their source and content. This uncovered 2,687 unique auto-dialing campaigns, the largest of which advertised student loans, health insurance, Google search engine promotion and social security scams .
CONCLUSION
The researchers discovered 2,687 unique robocalling campaigns out of which two large scale robocalling campaigns that selectively target the Mandarin speaking Chinese population in North America and two fraudulent robocalling campaigns which impersonated the Social Security Administration (SSA) office were there.
In the end, researchers conclude that answering or ignoring these calls don’t affect there increase in volume. Furthermore, they suggest telecom service providers to operate their own honeypots and use a pattern call recording technique to identify and block subsequent malicious or fraudulent campaigns.
We at Ethical Debuggers, suggest you to:
- Don’t give your credentials or OTPs to anyone on the call.
- Don’t reply to automated robocalls.
- Don’t give your phone numbers to promotional websites or companies.
- Don’t reply to suspicious voicemail messages.






