Completing its benchmark of 1 billion sales across the globe, Apple devices are always among on top of the best devices that are known to provide the ultimate privacy and keep its users up to date about security-related issues. These devices are sometimes also called hack-proof because either they are very difficult to hack or they require extensive knowledge of hardware underlying its devices to explore the bug and exploit it.
From the last decade, be it any industry of entertainment across the globe, the scenario of hacking is shown as a hot cream (with 3-4 consoles running simultaneously and a person is hacking or taking the control of the device remotely). But, it is regretful to say that only the persons who actually know the target device can only understand the prerequisites to make it happen. Just like the size of all the fingers are not equal, each device has not the same vulnerability and if the same vulnerability does exist, it may have a different architecture or hardware designs.
Recently, a researcher from the GoogleProjectZero team named Ian Beer has found a vulnerability in one of the main Apple core functions that allow an attacker to take control of a particular device remotely but should be in the required vicinity. Let’s learn about vulnerability and its exploitation.
SOME BASICS
Nowadays, in this new era of 5G and optical fiber cables, everyone of us are aware about the value of data transmission rates and the lag time, therefore we all look for a reliable or more precisely Peer to Peer connection that takes very lesser time as compared to the Wifi technology. But when compared to some very old technologies like Bluetooth to transfer media files, wifis obviously offer very high data transmission rates and thus most people use Wifi Direct instead of Bluetooth to transfer files from one device to another in their home
Wifi Direct allows you to establish a direct connection or Peer to Peer connection to the target device without any intermediate or access point (in the case of your home network, the access point or gateway is the router or switch).
In case of Apple devices, AWDL is an Apple-proprietary mesh networking protocol designed to allow Apple devices like iPhones, iPads, Macs and Apple Watches to form ad-hoc peer-to-peer mesh networks. Funtions like Airdrop, stream music to your Homepod or Apple TV via Airplay using AWDL.
THE VULNERABILITY AND ITS EXPLOITATION
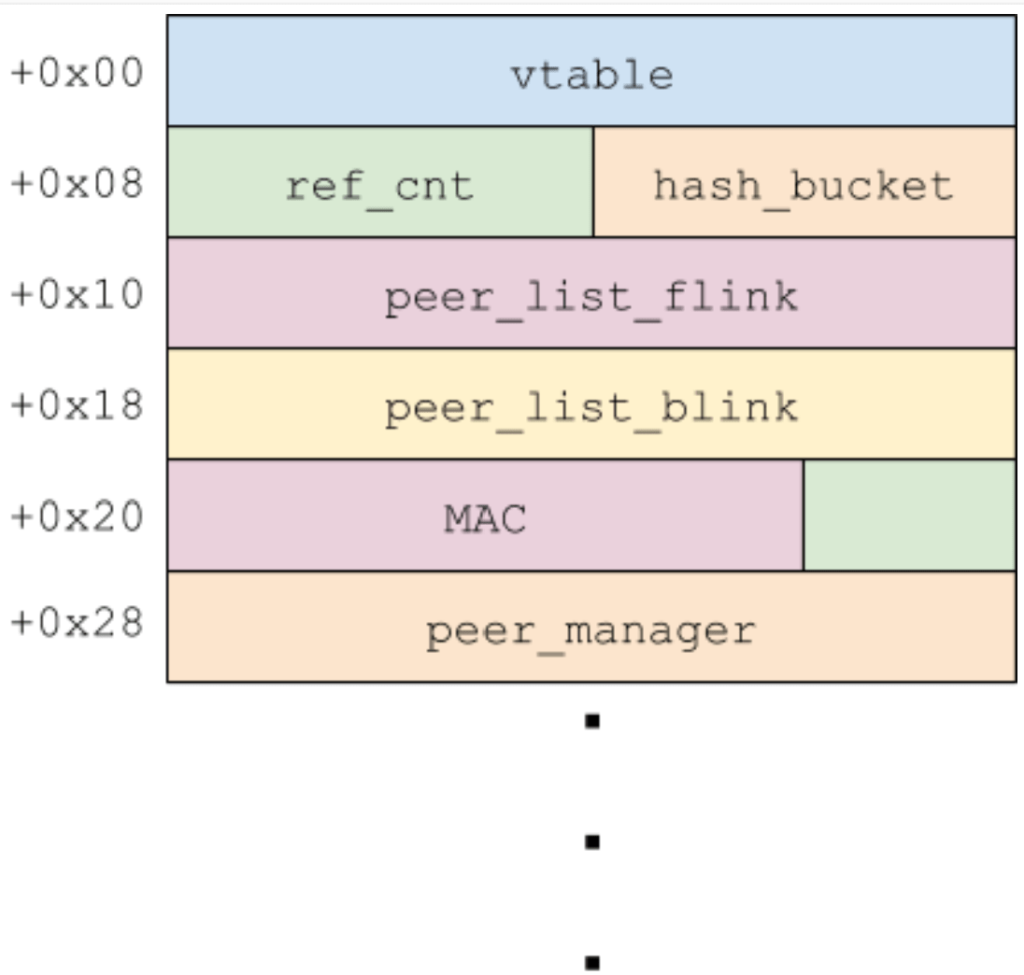
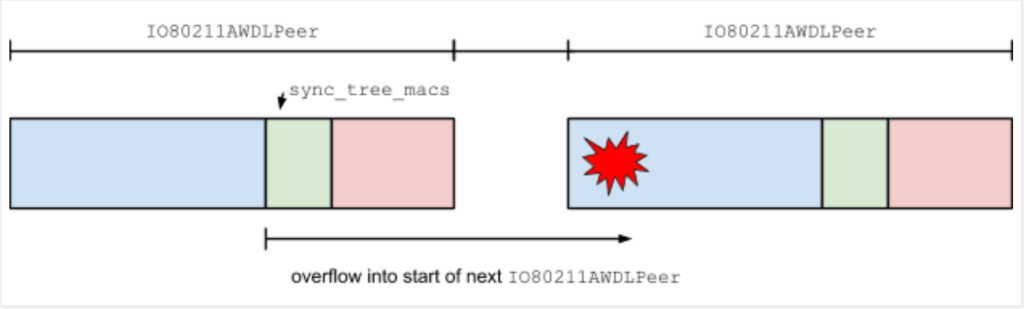
When a peer or other device wants to connect to the Apple Device using AWDL protocol, it has 2 C++ classes, IO80211AWDLPeer and IO80211AWDLPeerManager to read and manage connections. Out of the two, IO80211AWDLPeer object is for each AWDL peer from which a device has recently received a frame from and IO80211AWDLPeerManager is responsible for orchestrating interactions between this device and other peers.
According to the researcher Ian Beer, after receiving the action frames from the peer device, the protocol has different methods defined to parse the different parameters associate with that frame. It first updates some timestamps then reads various fields from Type-Length- Values or TLVs in the frame using the IO80211AWDLPeerManager::getTlvPtrForType method to extract them directly from the buffer. The source code for which looks like this:
int
IO80211AWDLPeer::parseAwdlSyncTreeTLV(awdl_tlv* tlv)
{
u64 new_sync_tree_size;
u32 old_sync_tree_size = this->n_sync_tree_macs + 1;
if (old_sync_tree_size >= 10 ) {
old_sync_tree_size = 10;
}
if (old_sync_tree_size == tlv->len/6 ) {
new_sync_tree_size = old_sync_tree_size;
} else {
new_sync_tree_size = tlv->len/6;
this->n_sync_tree_macs = new_sync_tree_size;
}
memcpy(this->sync_tree_macs, &tlv->val[0], 6 * new_sync_tree_size)
Each TLV is passed to IO80211AWDLPeer::tlvCheckBounds. This method has a hardcoded list of specific minimum and maximum TLV lengths for some of the supported TLV types. If the types are not explicitly listed, it enforces a maximum value of length 1024 bytes. The TLV parser will round that value down to the nearest multiple of 6 and copy that number of bytes into the sync_tree_macs array. This will simply result in the linear heap buffer overflow in 6-byte chunks that can corrupt all the fields in the IO80211AWDLPeer object.
Therefore, by crafting your own frames with the knowledge of exploit development, an attacker can place the shellcode at the relevant memory location and execute the arbitrary code which the attacker wants to run. Below is the video by the researcher demonstrating the fact that how one can broadcasts Denial of Service using ADWL.
CONCLUSION
The researcher took 6 months to found and generate POC for this vulnerability. He has also said that this vulnerability has not been exploited in the wild. Apple Inc. has already patched this issue in its IOS 13.5 release. We advise our readers to update their device soon to avoid exploitation of this vulnerability and misuse.