As technologies are getting more advanced, virtuality is becoming more friendly to human beings and when the word “virtual” comes, one word that comes into every tech geek’s mind is that of “Cloud Computing”. In today’s time , every second startup is dependent on cloud infrastructure instead of renting servers as:
- Cloud infrastructure helps an organization to grow more with less number of employees.
- It also helps to get advantage of more resources in less cost.
There are many other factors that overpower cloud computing to that of physical infrastructure but yes there are many IT companies out there who still uses their own physical infrastructure.
Great Deal for Cloud Architects: Buy the Cloud Computing Architect Certification Bundle which include certifications from all major cloud providers Google Cloud Platform, Microsoft Azure and Amazon Web Services at just $39 giving 97% off on actual price $1,476. To know more or buy, click here.
Another virtual environment that developers are getting addict or are addicted to is that of Containerization(Most people know it with the name of Docker). For those who don’t know about this concept, you can click here as we have explained it in detail in one of our previous article. The biggest reason for the growth of Containerization is that this technology provides on the go required resources to the end users regardless of physical infrastructure on their ends. It help developers to build and execute without taking care of libraries and system requirements and that’s what every developer cares about nowadays.
In past some researches on containerization, researchers have found a lot of vulnerabilities in this technology that had helped attackers to mine crypto from the victims’s system. Recent research by Palo Alto Networks has too exposed this fact and found a new cryptojacking worm “Cetus” that are infection vulnerable docker clients and mining the cryptocurrency from the system. Let’s see it through an eye of a security researcher.
INSPECTING THE CETUS
In order to find this new cryptoworm, researchers used honeypot to play with the mind of the attackers. They designed vulnerable looking docker systems to allow attackers enumerate that system in their search and attack it so that they can reach into its depth and find out its origin. After analyzing the honeypots for approximately one month, they come across various attacks originating with a unique cryptoworm that led to mine cryptocurrency, Monero from the victim’s system. They later named this cryptoworm as Cetus.
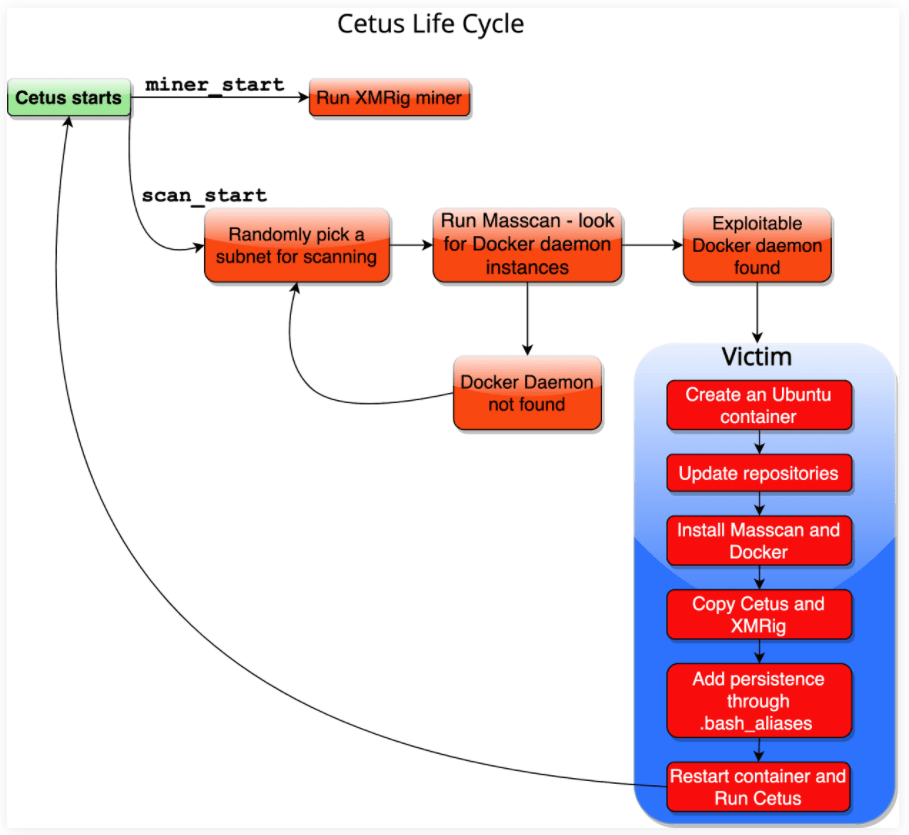
The attack chain starts from the first infected machine with this malicious cryptominer container installed on the vulnerable docker system. To make this malicious container look legit, the attackers disguise the malicious container in the name of legit containers like Portrainer, docker-cache.
According to the researchers, the installed malicious container image on the victim’s system has mainly two functions:
- miner_start
- scan_start
As the two names indicating themselves, the first function will initialize and start the cryptominer, XMrig(an open source cryptominer). The second function will scan and deploy this malicious container in other vulnerable docker systems.
First of all the miner_start will open /var/log/stmp.log that will contain the log for all activities that took place in victim’s system and send it to the attacker’s Command and Control server. Then, it starts the cryptominer XMRig which utilizes the victim’s system resources in order to mine the Monero.
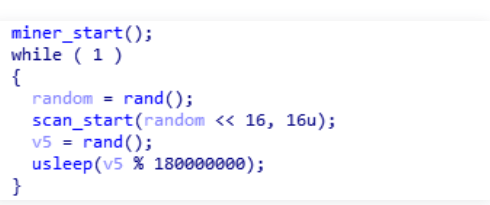
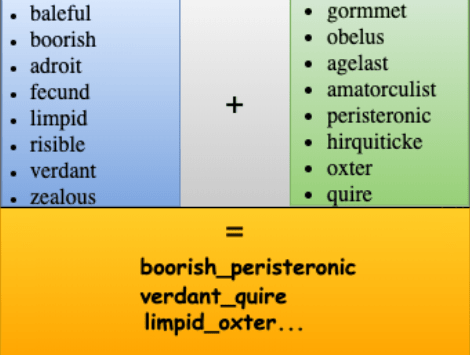
Then simultaneously scan_start will randomly chooses the 16-bit subnet in the victim’s network and using the Masscan utility it scans for the other vulnerable docker system on the victim’s network on port 2375. After successfully exploring the vulnerable docker system, it transfers the malicious container image with different names with the help of Docker’s CLI as shown in the list below.
The whole attack chain looks like this:
CONCLUSION
According to past major cyberattacks, we can say that attackers are more interested in mining crypto rather than extorting the victim’s privacy. Our recent article on major cyberattack took place this year clearly shows that it was fault on victim’s side that attackers took advantage of. So it is suggested to:
- Patch the vulnerabilities of softwares installed in your system and keep updated.
- Keep yourself updated with new social engineering attacks taking place in the cyberworld.
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.