As Apple announced macOS 11 Big Sur at WWDC 2020, claiming that it will have major improvements as compared to macOS Catalina , a professional MAC and IOS developer reveals a Mac privacy bug .
When MacOs Mojave was introduced , Apple claimed that it would provide additional protection for the user’s private data. A privacy protections system (TCC : Transparency ,Consent, Control) was introduced in Mojave to protect the files on our Mac from access by unauthorised applications. A researcher found a way to hinder the private data of users that too with an unauthorised app , thus bypassing the privacy of the users . He claimed that this exists in Mojave,Catalina and Big Sur Beta as well.
When Apple introduced its Apple Security Bounty Program ,like many other researchers he too reported a zero day exploit that can give an unauthorised app access to some private files , without being given the authorisation . He claimed that the flaw remains unpatched for about 10 months and thus he opened about the flaw in public . He termed the MacOs Privacy protections as “Security Theater”. Let’s look into the report he sent to Apple Product Security.
THE ZERO DAY
The security researcher reverse engineered the Safari application which is used in macOS as a web browser. As claimed above, the researcher said that this zero day allow any unauthorized app to bypass the privacy protection provided by Apple, for which its products are well known . The researcher tested a sample of code and run it. He claims that his app will allow to access /Library/Safari/TopSites.plist and send the contents of that file to the domain which is owned by attacker himself through HTTP POST request.
The .plist files are the property list files which are used to define the property and configuration of particular applications or owners in that environment or system. To exploit this vulnerability, the researcher said that he chose safari to target because it runs Javascript in context of the main app rather than expected to run it in the sandboxed content of the Web help Controller. It means that when any application requires to run Javascript, the app should execute Javascript in reference to a main executor controller (here Web help Controller) rather than other controller decided by that application. Thus an application with same behaving reference will automatically execute that javascript. The researcher used this flaw and exploit it.
The researcher develop an app which makes a copy of the Safari Application in the other location rather than what is occupied by the original Safari in the disk location. Here also a big flaw by macOS is that it didn’t check every parameter of code signature of an app properly. Thus any unauthorized application with some parameters of its signature satisfying this Apple security check, can bypass this.
Finally as claimed by the researcher, his app make a copy of the Safari application and replace the “Safari.app/Contents/Resources/HTMLViewController.js” with the modified version. Here is the code snippet inside the application that reveals this change.
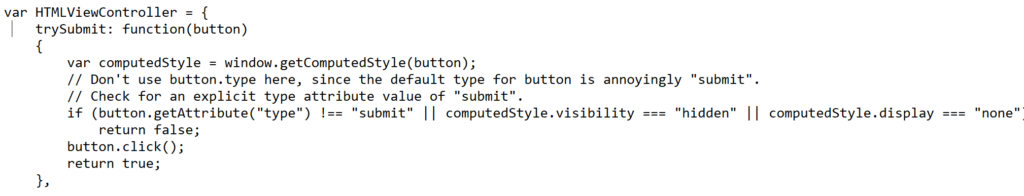
Now, the sample app contains a Safari extension which allows SafariServices API to open the extensions Pane in Safari Preferences. This extension is a Javascript file that we discussed above which will exploit this privacy. Now this javascript file only works with original safari. The researcher designed app will simply sets the NSQuitAlwaysKeepsWindows global preferences to make sure that windows open on quit reopen on next launch. After setting up the preferences, it opens the Extensions pane in the original Safari and terminates the original Safari which will lead modified Safari to automatically reopen that Extension pane which means that now the resources which are accessible to the main Safari app can be accessible by this modified version of the app i.e the modified app has access to all the files that are accessible by the original app. This is the reason why in starting it was declared that the app has access to the top sites surfed which now clearly shows that this is due to the flaw in Safari browser. Here is the snippet code of extension handler.
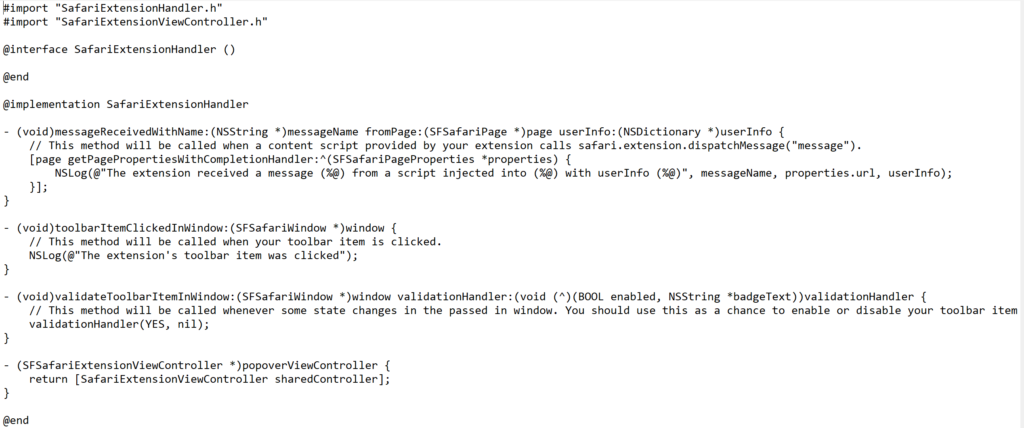
CONCLUSION
This is still a zero day and this flaw needs to be patched by the Apple . Until apple do not patch this vulnerability, we suggest our readers to install apps that are verified and trusted .






