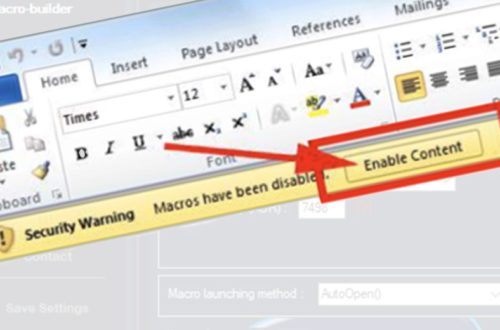
The word that frighten us the most in this cyber world is Ransomware! All big enterprises try to protect themselves from this but bad actors are always a step ahead which give end results as data breach to the organization.
There are lots of Ransomware groups which run affiliates in the underground. Some names for popular group out there are the Sodinokibi aka Revil, Avadddon, Maze, Thanos and more. These all ransomware operators are run by the professional experts behind them but due to their deeds they are being regarded as unethical or bad actors.
So discussing about the groups, researchers from Carbon Black Threat Analysis Unit (TAU) (a unit from Vmware) have recently come across a group named Conti Ransomware operators that really have out of the box thinking.
The most powerful feature behind this ransomware is that it creates 32 threads to encrypt files. In a simple language, it utilizes more computing resources such that at a particular time you have 32 different hands working on the same task. You can think it to be same as that of 32 workers together building a large wall. The concept behind using 32 threads simultaneously is just to make the process of encryption faster as at the end the ultimate game of the ransomware is just to quickly encrypt all the data so that it can demand ransom from the victims.
This ransomware operators uses the most powerful AES-256 encryption that makes it more difficult to decrypt files. So let’s see the whole process from getting it into your system to encrypting your files.
THE PROCESS
After this ransomware gets delivered to your device through phishing, Bad USB, or any campaign, the obfuscated code inside this ransomware targets your local network and will skip the encryption for your local computer functioning files but will encrypt the local hard drive files. As soon as this ransomware enters in your computer, it will attack your SMB (Server Message Block) to take control of your local network. To do it successfully, it executes commands from CLI like “—encrypt_mode.” “—encrypt_mode local,”, “—encrypt_mode network” to encrypt the local hard drives and all the network shares ( adapter, networks cards) and thus it no more needs any additional campaigns as SMB will act as an adversary that is sufficient to spread the ransomware, acting as a silent killer.
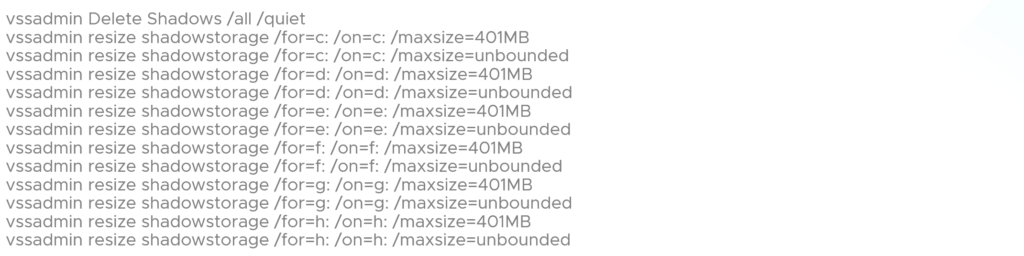
After that the ransomware stops all the windows services running in the background or that are essential for windows to function properly and make the system go in recovery mode using vssadmin to ensure their deletion. Some additional commands are also run by the ransomware to stop other services.
After that ,this ransomware move on to it’s next step and it will start searching for some file extensions like exe, dll, lnk, and sys. and strings that it does not want to encrypt and thus skip their encryption in its methodology. Here’s the list of files that it will ignore:

While all this methods kept running on one side, on the other hand it uses Windows Restart Manager simultaneously. The use of this utility has a logic behind it.
You know that when you request to restart your system, your OS alerts you to save the data on which you are currently working and if you have locked some of your files, they will get unlocked while restarting as the lock keys with which you have locked your files are saved in the memory but while restarting it, the current memory gets flushed and thus unless and until your lock keys are enabled in the startup program, they get unlocked. So this ransomware operators take the advantage of this logic and start encrypting your each file individually using this logic .
It encrypts your files with AES-256 encryption via a hard-coded public key and calls its 32 threads via CreateIoCompletionPort() call to make the encryption process faster. Then, it attacks on the local ARP cache of the machine and enumerates the whole network and spreads malware into vulnerable machine.
At the end, it retrieves the ransomware note for its victim to specify the details about the number of files they have encrypted and how the victim can decrypt it.
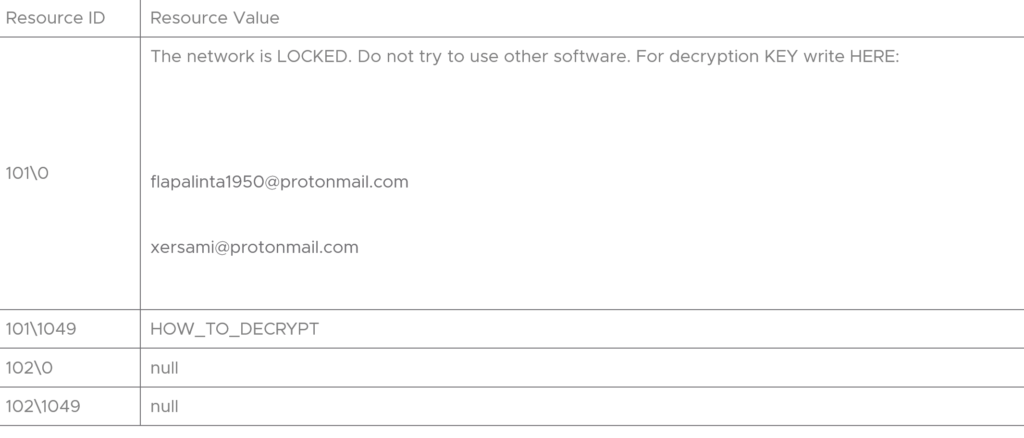
CONCLUSION
The new generation of ransomware are attacking their victims even more badly, making fun of their victim’s privacy. The best way to avoid ransomware attack to an extent is to keep your local network isolated from external attacking. This can be achieved by:
- Putting strict firewall and imposing hard rules
- Using encrypted channel for communications.
- Using strong passwords for all the systems.
- Keeping an active Intrusion Detection System.