It is a new trend that has been adopted by many corporates and organization in this outbreak is the Work from home strategy. There is no doubt that this strategy has resulted in generating quite a lot of profit for the corporates as they don’t have to feed their employees by hiring a physical workspace,spending on their transport, electricity bills, etc. They just need to ask employees to work more.
It’s a tradition that every profit too has it’s own consequences. If a employer is working from home, all the work is done remotely. As the work is done remotely, security concerns takes place as now the organization’s intranet is being extended. While some popular applications like Zoom get popularized for remote video conferencing, bad actors do not leave any chance to disturb their functioning. There are many kinds of attacks explored against this application and thus many organization switch over to its other alternatives like Microsoft Teams, Google Meets, Cisco Webex, Citrix Workspace. They all are considered to be trusted but bad actors still not stop doing attacks against these application. They continue launching phishing campaigns and other types of attacks to these application, thus making working from home a threat more than an advantage.
In one of the above mentioned applications, recently researchers from Pentester Partners found out a vulnerability in Citrix Workspace that allows your device to be compromised remotely. What is that vulnerability, let’s explore it.
VULNERABILITY AND EXPLOITATION
Citrix workspace runs automatic update feature in the background to allow users to install update versions of the application installed in the system. In order to do this, it triggers a service under the SYSTEM context and sets up a named pipe called UpdaterServicePipe-800fad42-1d0f-4f66-8e18-8a0938cdc721 to allow the Citrix Workspace app to allow the client to establish a connection to www.citrix.com and check for any updates and if any update found it will install that update.
Now what an attacker can do is it simply establish an NTLM relay attack to send maliciously craft message and spoofing the client process ID over a named pipe communication and between the client and server and then trigger the client to do arbitrary code execution.
The named pipes is the Microsoft technology that can be used by windows processes to create a peer to peer connection between the client and server to ensure any checks like for security or update. In this demonstration showed by Pentester Partners, they just exposed the fact that by updating the Access Control Permission (ACL)list of the created pipe by the updateservice.exe to check updates on the host, it allows anyone to connect to it in the network, thus allowing anyone to impersonate server.
Thus an attacker by using NTLM relay attack, he will spoof the client process ID in those networks where there is not any SMB signing (which is required for authentication). Thus using this technique, the attacker spoof impersonates the end server to being a legitimate client.
Now the attacker does not need to verify it’s identity to the end servers for passwords during NTLM verification. The attacker will become server for the client and client for the end server. It can read and craft any message which is being transmitted between the two ends.
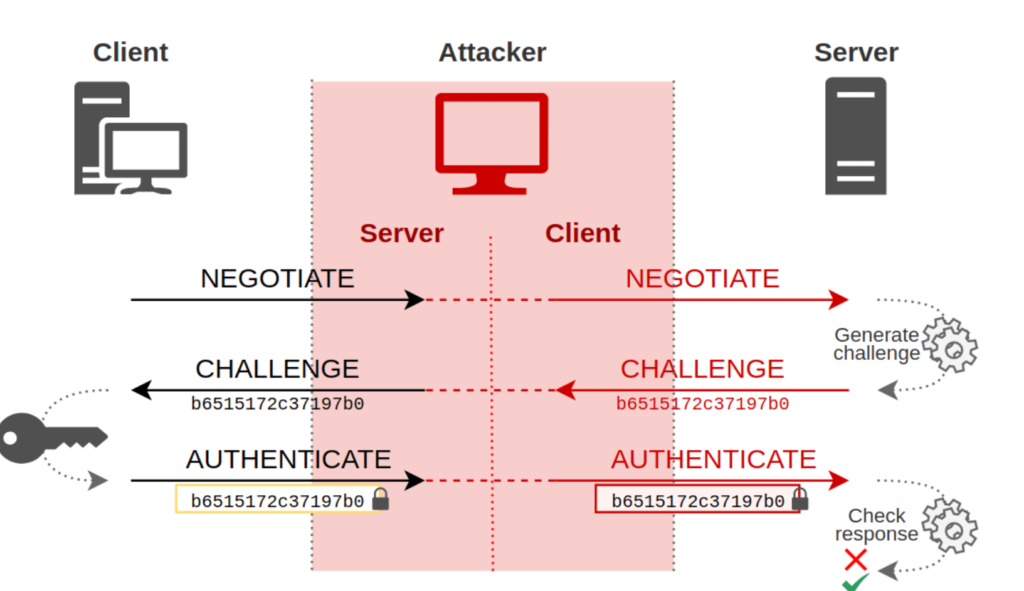
Thus can simply craft a legit packet to initiate the connection back to the target’s desired server location wherever he wants to and thus perform Remote Code execution on the end server. This video explains this exploitation well:
CONCLUSION
This vulnerability affects the Windows 1912 LSR and Windows 2002 version windows and can be tracked as CVE-2020-82207. The patch has been released by the company and it is recommended to download this patch as soon as possible to avoid any attacks related to this vulnerability.






