According to recent attacks on an enterprise we have explored till now, the study shows that the causes are the common vulnerabilities which administrators give least importance. There is no doubt on the fact that these common vulnerabilities are one of the creamy things that every hacker tries to find in a system but these vulnerabilities are not the only thing that can leave a system exposed.
In today’s time, every sector are somewhat dependent on third party softwares to expand their vision and functionalities. But with growing functionalities, the security of a system becomes more vulnerable as then the system has more vectors to attack. For example, every web administrator has heard about WordPress ( Content Management System). This platform allows an individual to expand more functionalities on its website with the help of plugins which are ultimately third party codes installed in your sites. Thus, if plugin code found out to be vulnerable, it becomes a source of attack on the whole. Ultimately, the more plugins you have, the more you need to concern about your security.
Great Deal: Learn to protect your wordpress site with WordPress Security Course by OSTraining at just $33 . To buy it, click here. Original Price: $37
Now, let’s come back to the article and talk about the its main focus i.e. Mobileiron. It’s a unknown term for normal individuals but corporate workers are familiar about this software and its alternatives. It is Mobile Device Management (MDM)Software which allows the corporate to control their corporate data on its employee’s personal device. These softwares are used where the policies like “Bring Your Own Device”, BYOD are used in an enterprise environment.
These softwares are based on client server model in which the end user needs to download the supported application and connect to the corporate’s server. According to Wikipedia, these softwares allows an organization to have the following control over the employee’s device:
- Policy Enforcing
- Personal Policy: According to corporate environment, highly customizable
- Device Platform specific: policies for advanced management of Android, iOS, Windows and Blackberry devices.
- Compliance Policies/Rules
- VPN configuration
- Application Catalogue
- Pre-defined Wi-Fi and Hotspot settings
- Jailbreak/Root detection
- Remote Wipe of corporate data
- Remote Wipe of entire device
- Device remote locking
- Remote messaging/buzz
- Disabling native apps on device
- Some Kiosk software features
Some researchers from security consulting firm DEVCORE have found potentially serious vulnerabilities in MobileIron products that allows an unauthenticated attacker to do Remote Code Execution on the affected server. Let’s study about the vulnerability.
VULNERABILITIES THAT DROWNED FACEBOOK ALONG WITH IT
For understanding the vulnerabilities in the software, let us first understand its architecture. The architecture can be well explained through this below diagram.
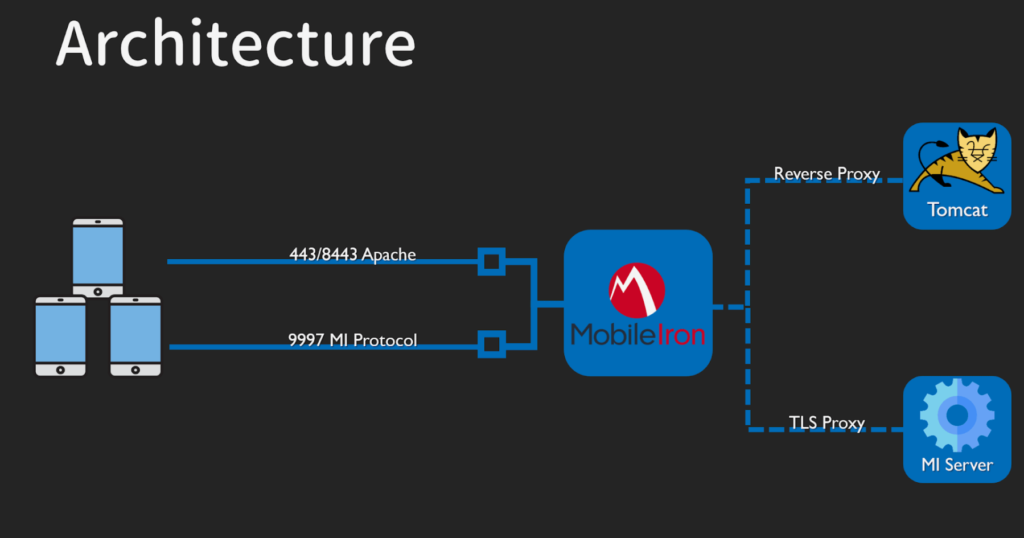
As you can see in the above diagram, it is cleared that Tomcat’s reverse proxy is used, it therefore controls the request by the user. The vulnerability that researchers used to hijack facebook’s server lies in this branch of the above architecture that fails to handle the user input, deserialization in Java APIs. By failing to handle the user input properly, it cannot be relatable with SQLi or XSS rather it is a JNDI injection which stands for Java Naming and Directory Interface injection.
To perform this attack, an attacker first need to find out vulnerable MobileIron server in which the attack can be performed. In this case the researchers find out the Facebook’s MobileIron equipped server which is exposed with Java deserialization vulnerability.

Through the above screenshot states that server’s index responses 403 Forbidden now but according to the researchers the Web Service is still accessible!
Therefore after their discovery of all the vulnerable points, they got a shell of one of the Facebook’s server and can be seen in the below video.
Researchers also disclosed 2 other vulnerabilities in the softwares that allows an attacker to perform the following functions:
- CVE-2020-15505 – Remote Code Execution (Same as we discussed above)
- CVE-2020-15506 – Authentication Bypass
- CVE-2020-15507 – Arbitrary File Reading
CONCLUSION
The following products are affected and there patches have already released by the company:
MobileIron Core (version 10.6 and earlier)
MobileIron Sentry
MobileIron Cloud
Enterprise Connector
Reporting Database.
A technology is created by human beings therefore such humans too exists that discover vulnerabilities in the same technology. No software or technology is permanently resistant to vulnerabilities. Therefore, it is the responsibility of the users of that software to timely update or patch the newly discovered vulnerabilities.
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.