At some point in our life, we all come across some leadership responsibilities. For a leader, the most important characteristics is to get himself updated with his user’s data in order to analyze and increase their efficiency. Thus, a leader has to maintain a proper database that has both integrity and authenticity. These two features of a database determine its strength and lifeline.
Popular for some past years, Microsoft’s Excel Spreadsheets are one of the most common utility used by many officials and staffers in every sector. From tourism to IT industry, every organization from different industries maintain several databases. In case of large and dynamic records, there is a need for server. But when you just have small number of records and just want to perform a small sort of calculations upon it, Excel spreadsheets is always the first option that comes to your mind.
Some researchers from NVISO Labs have found hackers abusing these spreadsheets docs to deliver malware into the victim’s system. In our some previous articles, we have described technique in which hackers abuse Microsoft documents by attaching a malicious macro with it. Though the method of delivering malware through these maldocs is also same but here the technique is different. Let’s explore this technique.
OPERATION EPIC MANCHEGO TECHNIQUE
Usually the traditional of delivering malware through documents is by attaching a macro code programmed in VBA using Microsoft Editor. According to the researchers, here the attackers do not use the traditional method rather they used a open source tool EPPlus to attach a macro code in the the document. The question here arises, why? The answer for this is:
- It creates documents in OOXML (Open Office XML) file format which is an Open Packaging Conventions (OPC) format: a ZIP container with mainly XML files, and possibly binary files (like pictures). It was first introduced by Microsoft with the release of Office 2007. OOXML spreadsheets use extension .xlsx and .xlsm (for spreadsheets with macros).
- When a VBA project is created with EPPlus, it does not contain compiled VBA code and office metadata rather it just contains the compressed VBA source code which is hard embedded into the EPPlus source code which makes antivirus slightly difficult to detect the malicious behavior.
- It can create spreadsheets containing a VBA project and that project can also be password protected and/or digitally signed making it difficult for users to analyze the code.
After the macro code has been successfully attached into spreadsheet document, using some social engineering techniques, hackers send this spreadsheet document to the victim. One of such examples of phishing mails captured by the researchers is shown below:
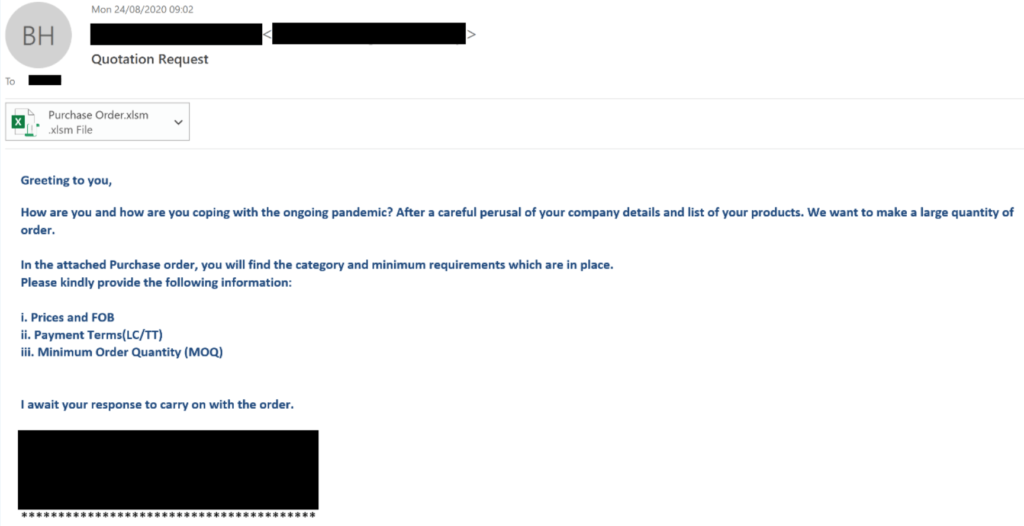
As you can see in the above example, a file with extension .xlsm is attached with the mail. As soon as victim the document, the victim will be asked to enable the macro. When the macro is enabled, now the malicious code will start its duty. It will download the second stage payload from the C&C server. According to researcher’s analysis, the hackers used a very old technique to hide the actual payload which is DLL inside is image, known as steganography. The payload data is obfuscated inside the image as shown below:
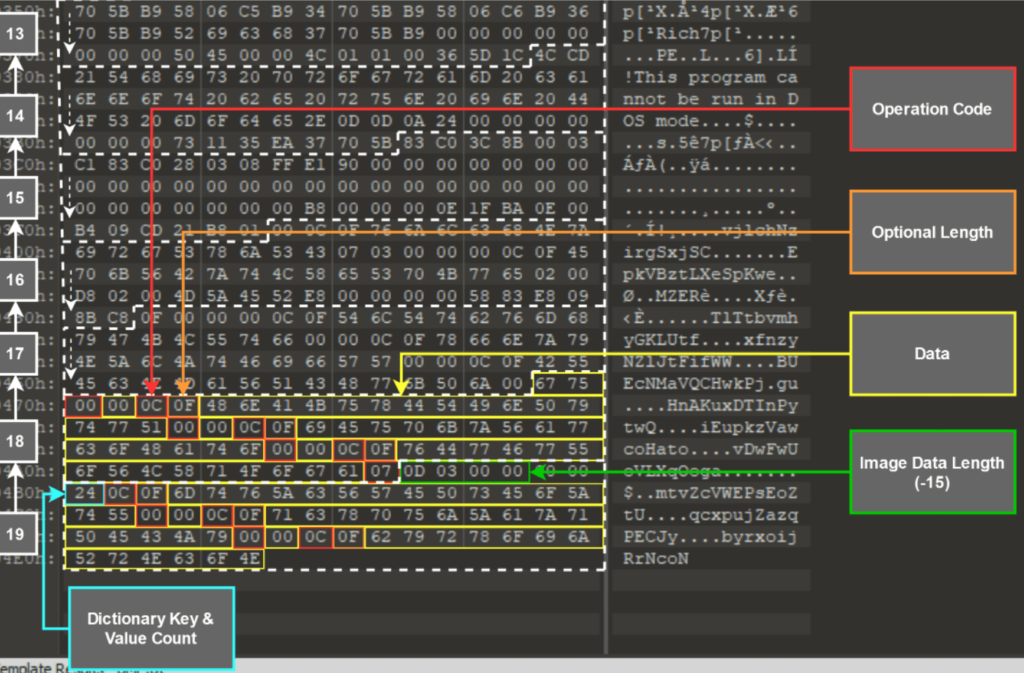
Then finally as soon as DLL loads and executes into the system, it will load the final executable which is an infostealer. The full action chain is shown below.

CONCLUSION
Researchers are analyzing the attackers’ group Operation Epic Manchego from the last two months. They have almost analyzed almost 200+ maldocs samples and have discovered variety of infostealers variants delivered by this groups. We at Ethical Debuggers suggest our readers to please stay alert with such type of phishing emails delivering maldocs as attackers are actively spreading the reign through this attack.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






