The place where the 21 century humans as well as bot resides together is the Internet. Either it is social media or it is just any other application, with the advancement of Machine Learning and Artificial Intelligence, it becomes difficult to identify whether the counterpart on the other side is a human being or a programmed bot. As a result, humans exchange information with such bots that lead to privacy issues.
With the increase in traffic on the internet from last decade, tech giants Google, Facebook, Whatsapp are still regularly questioned on user’s privacy. There is no doubt on the fact that these giants have answered most of the questions but even today, we all search for an asset that preserves our privacy better than these giants. There are many people on the internet who just don’t care about their privacy and for some, privacy is as essential as taking breathe. Everybody knows about the fact that these giants tracks even your private life, but still some are least bothered about this because they think that they can’t stop these tech giants to track them. Although there are lots of articles on the internet by reputed researchers in which they have explained on how can you stop these giants to track your privacy. Every time you visit a website, you are asked to say “Yes to the cookie consent” which is as long as 1000 words in which the company has explained about part and amount of data they are using ethically and you full rights to manage the amount of data to give to that website. But 95% of the people don’t read about that consent and just click on the button, “Yes, I agree”. This allows developers to misuse the user’s trust and make false promises to the end user.
Great Deal: Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Following the current situation, researchers at Columbia University developed a tool named “CRYLOGGER” – an open source tool to inspect well populated applications against cryptography misconfigurations dynamically. The fact behind this research states that, in this digital world, cryptography is the only way through which we can verify, authenticate and protect our data. Nowadays, every second applications acclaims of a tight encryption to protect user’s data. How much this statement is true, let’s find out through research.
APPS CRYING FOR CRYPTOGRAPHY
To initiate their research, the team downloaded 2148 free Android apps from the Google Play Store. These cover the most popular free apps of 33 different categories. Out of which they discarded 368 applications as some of these don’t support crypto APIs and some of these keep crashing or they require libraries that cannot be installed in the emulator environment. At the end, they experiment on 1780 applications which are well populated and some have over millions of downloads.
As we all know the fact that Android is a derived version of Java, therefore researchers examine these all applications against a ideal Java Cryptographic Architecture that define classes for basic cryptography in these applications. These are:
- Message digest
- Symmetric encryption
- Asymmetric encryption
- Key derivation/generation
- Random number generation
- Key storage
- SSL/TLS and certificates.
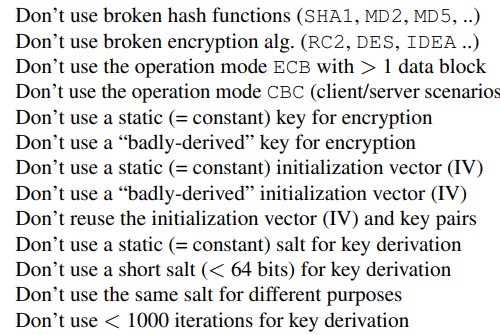
The classes defined inside the tool check the application against these 26 rules for cryptography measures:
After analyzing the 1780 against this 26 cryptographic rules, researchers found 306 applications rules violating the cryptographic rules, two of which are popular in almost every application:
- Broken hash algorithms
- Unsafe random generator
CONCLUSION
After disclosing the above vulnerabilities to the concerned authors of these applications, research got feedback only from 18 authors and they patched the vulnerabilities. Researchers also compared their result with the other well known tool, Cryptoguard, to detect cryptographic misconfiguration by statically reverse engineering applications and found out that, their results from Crylogger (which dynamically detects and logs the results are more accurate than that from Cryptoguard.
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.