We all believe that startups and own businesses are the safest option towards a brighter future. There is no doubt on this fact that worldwide pandemic in the past few months has even prove this statement right. Due to decline in economy, many people have lost their jobs and some have lost their life also. One thing that we all can see and learn is that big names like Google, Alibaba, Amazon, Facebook, Microsoft, and many more have launched a variety of schemes that helped many individuals in growing their startups more rapidly. Some of the schemes include launching free advertisements for new startups, providing free cloud hosting, and sometimes…
-
-
FLAWS IN MOBILEIRON’S MDM SOFTWARES ALLOW RESEARCHERS TO HIJACK FACEBOOK’S SERVER
According to recent attacks on an enterprise we have explored till now, the study shows that the causes are the common vulnerabilities which administrators give least importance. There is no doubt on the fact that these common vulnerabilities are one of the creamy things that every hacker tries to find in a system but these vulnerabilities are not the only thing that can leave a system exposed. In today’s time, every sector are somewhat dependent on third party softwares to expand their vision and functionalities. But with growing functionalities, the security of a system becomes more vulnerable as then the system has more vectors to attack. For example, every web…
-
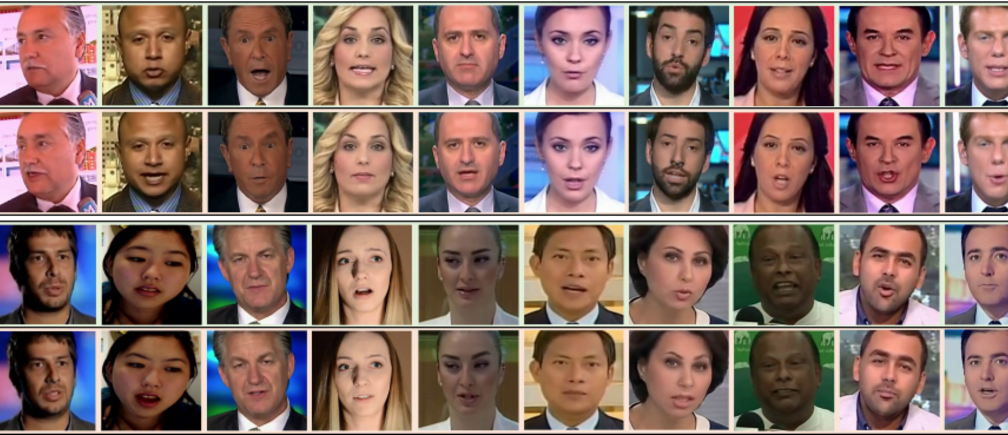
RESEARCHERS FOUND OUT AN ALGORITHM THAT DISRUPTS DEEPFAKES
In this worldwide lockdown, virtuality has over powered the reality . The ultimate drawback of this virtuality is that a person does not need to be present physically to mark his presence his picture or even his signature are enough to mark his presence. But the main point here is that Is virtual identity is enough to authenticate one’s identity? It’s a big NO. For instance, in many movies nowadays this technology is so common. To perform complex stunts, sometimes actors are not capable or for some reason they are not able to perform a particular scene in a movie, then using a technology known as Deepfake, it is possible…
-
FACEBOOK, AMD, NVIDIA AND ACCENTURE WILL NOW FOCUS ON CONFIDENTIALITY OF THEIR CUSTOMER’S DATA
Recently, there were many controversies on Facebook, Whatsapp, Google related to data security in the market. These all big giants even claimed that they follow end to end encryption policy which basically runs under an algorithm of asymmetric cryptography. To prove that they are committed to our security, some of them signed the Confidential Computing Consortium. Last year, Google along with Microsoft including 8 other companies(Intel, Microsoft, IBM, Intel, Alibaba, ARM, Red Hat, Swisscom and Tencent) signed this consortium. We believe that while data is transmit across the internet, CIA rule- Confidentiality, Integration and Authentication is being followed . To maintain all these factors, companies need to invest millions of…