We all know that WordPress is a place for website designers to automate their tasks. A guy who don’t have much knowledge about IT can easily launch website using this platform. Technically, WordPress is a Content Management System just like other websites like Drupal, Joomla available in the market but content developers love this due to it’s support and easy to use features like pick and drag.
For any website out on the internet, these three things make the websites the best :
- Easy to navigate pages of the website and user friendly.
- Searchable on the internet or SEO tasks.
- Security.
If any websites fails to get any of the above mentioned motive, it will not be able to get attention of the users.
Now, if we come to a Content Management System that means from only one dashboard you can manage front-end as well as back-end tasks for your website with no coding required. You can too manage the security for your website and perform SEO activities by installing plugins that will help you grow your website in a better way. But what if the plugin you are installing is affected?
One of the popular plugins that have more than 2 million installations, for performing SEO activities got affected with an XSS vulnerability that allows an attacker to execute malicious script on the victim’s browser. Let’s analyze what exactly is the vulnerability.
ANALYZING THE VULNERABILITY
If we see OWASP top 10 vulnerabilites, we will got one of the name as XSS attack also known as Cross Site scripting attack. This attack allows to run and inject scripts in a field on a web page which the attacker is not intended to. For example, if you visit a website that is asking you for login with parameters as you User ID and password, you generally enter your credentials and based on the authentication you are allowed to access your account on that website. But in the case if that website is having XSS vulnerability which is known to the attacker, he can run and inject some scripts into that fields which affects other users who visits that website. This is known as XSS stored attack. XSS is of three types
- XSS reflected
- XSS stored
- XSS DOM based
So in this All in Pack SEO plugin by Wordfence, every user with all level of privileges can give SEO title and SEO description to their post. Unfortunately, both these fields were not properly handled or sanitized to the inputs entered by the designers of that website, thus giving birth to an XSS stored vulnerability. Thus, any guy who is just an author of that website can inject malicious scripts that will be executed by the browser of other user on the same website whenever they will navigate to that particular section.
To become more user friendly, the developers of this plugin display meta data about SEO in All Posts area of the WordPress dashboard. This meta data includes SEO title and description.
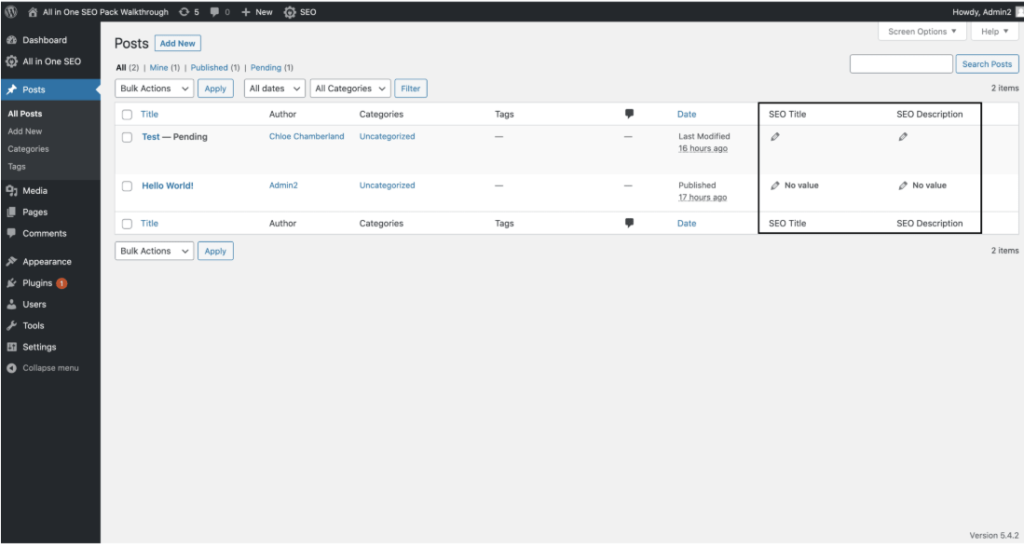
A user with least privileges like contributor can inject a Java script like <script>alert(‘1234’)</script> in any of the fields i.e SEO title or description and thus when the administrator of that website opens it to review, this script will be executed by the browser. A similar POC for the same is shared by the Wordfence team.
CONCLUSION
The users of this plugin need not to be tensed as this vulnerability is already patched by the team soon after they discovered it i.e. on 15 July. To avoid this similar kind of insider thread, it is suggested to give minimum privileges to other users on your website so that they can cause less harm to your system as well as your server.






