In today’s time, the growing technology has automated all of our task. Remember the times, when the first computer was created, it was as big as size of a room. Now you can interact with that same technology in as small size as a watch in your wrist.
Obviously, if the complexity increases, the security becomes more difficult to handle . Every person has different point of view to view that technology and many loopholes can be generated in that technology .
So combining all the above points, today we will talk about attacks that are taking place in Containership Infrastructure.
WHAT IS CONTAINERIZATION?
We all know that by using virtual technology, we can make full use of the system resources, you can have as many guest operating systems as your number of resources in that system. We can do so with the help of Hypervisor which abstract required hardware from the Hardware Abstraction Layer and provide resources for other operating system to run as a guest on the host OS. Applications like Vmware, VirtualBox can also help you accomplish this.
Now imagine you don’t have much resources in your system and it gets difficult to allocate resources for your guest OS. What will you do then?
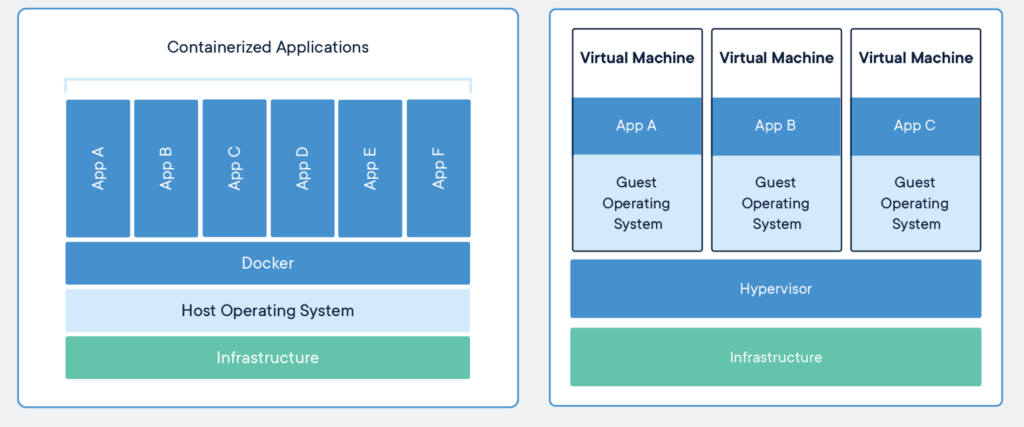
Here, the concept of containerization helps you out. Imagine a container in your home kitchen. Materials are packed inside it and they are not restricted to the material you keep inside it. You can put anything, it can be grocery, some stationery item or anything. Two identical containers have exactly same chemical and physical properties regardless of the fact where you keep it and they store and process the material inside them in the same manner.
Exactly how containerization technology works ! It lets you pack your essentials for application like its source code and all its related dependencies, libraries or anything that are required by the system, to build it in one package known as container. Thus any system having software to support containerization like Docker Engine can run many containers in any infrastructure either it is linux or windows, thus serving as an independent standalone application. Thus a system which can’t afford to run one virtual machine properly can run many containers using this virtualization technology.
HOW THE ATTACK TAKES PLACE
Researchers from Aquasec have researched about a recent attack on
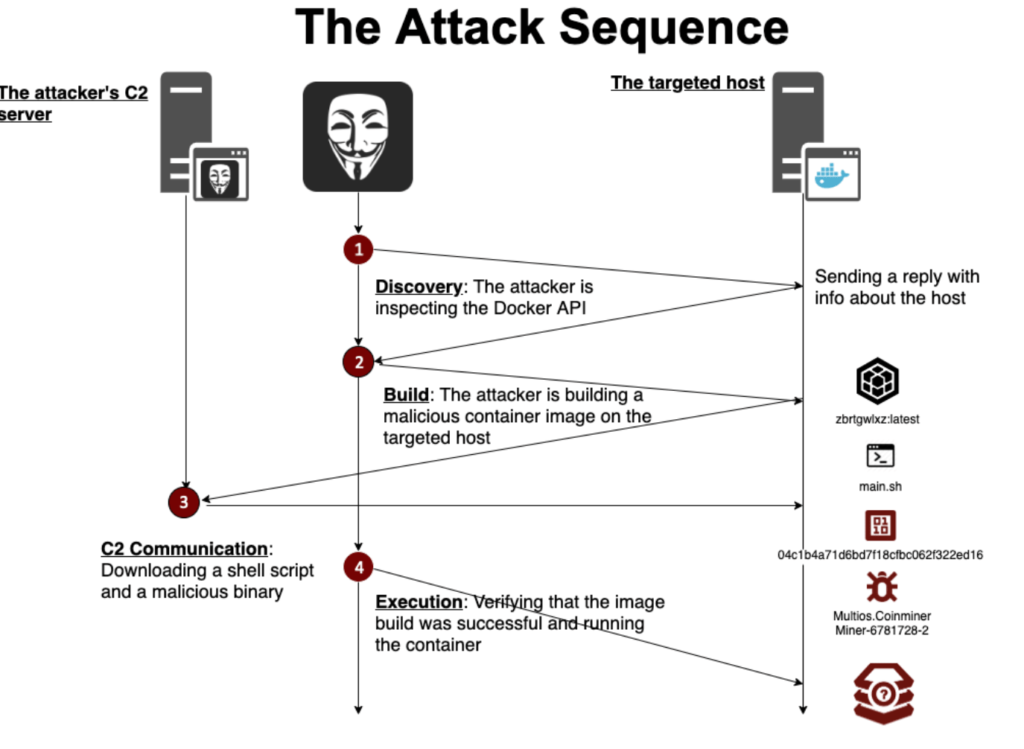
Docker API that is running on the server. The attacker enumerates and accordingly pings the exposed misconfigured or vulnerable API and use them to install container images into the host system. As told by the researchers, previously the attackers deliver malware by delivering it into the public registry i.e Docker hub that has collection of container images to install.
In this case the attacker first checks the API by sending a ping GET command to the end server. Then according to the reply received from the other end, the attacker acts accordingly. If the echo from the API running on the server found out to be vulnerable, then attackers sends a GET command to get information about all the running containers on the remote host.
Finally after getting all the information about the host, the attacker builds a malicious container image ,a Dockerfile into that host namely “zbrtgwlxz:latest”. This image contains the following information:
- Pulling a lightweight alpine image.
- A WGET command aimed to download the script main.sh from a remote source (http[:]//185[.]10[.]68[.]147/dock/main[.]sh).
Then the remote attackers runs the command /bin/sh -c ash /main.sh to initiate the container image. This wget command mentioned above is downloading the actual script that will further download the final open source crypto miner named XMrig from it’s Command and Control Server. The screenshot of the script which will be downloaded:

Finally the attacker runs further check commands to ensure that the cryptominer is running on the system. The below diagram explains well:
CONCLUSION
In the above demonstration, we see how an exposed misconfigured Docker API makes remote host cryptominer. Some might get confused with the fact that docker is a virtual concept and how it can mine cryptocurrency as it is isolated from the system. We absolutely agree but here the script which runs inside the container downloads the cryptominer into the victim’s system. Therefore, we suggest our users to properly configure their Docker APIs and make proper checks to ensure security in your infrastructure.






