RATKing is an animal which consists of a collection of rats with entwined tails . Some researchers found a new group that attacks the victims with a variety of trojans and thus named as RATKing .This group was in consideration by the researchers from late may . Let’s analyse the anatomy of this attack.
ANATOMY OF THE ATTACK
The attacker uses a simple phenomena of phishing to attack its victim. The attacker first sends an email to it’s victim that convinces them to download a file that is pertaining to be a PDF file but it is a VBScript that is used as a first process in the generation of payload in to the victim’s system.VBS is a scripting language that is used on Visual basic which is used by developers for programming windows applications.
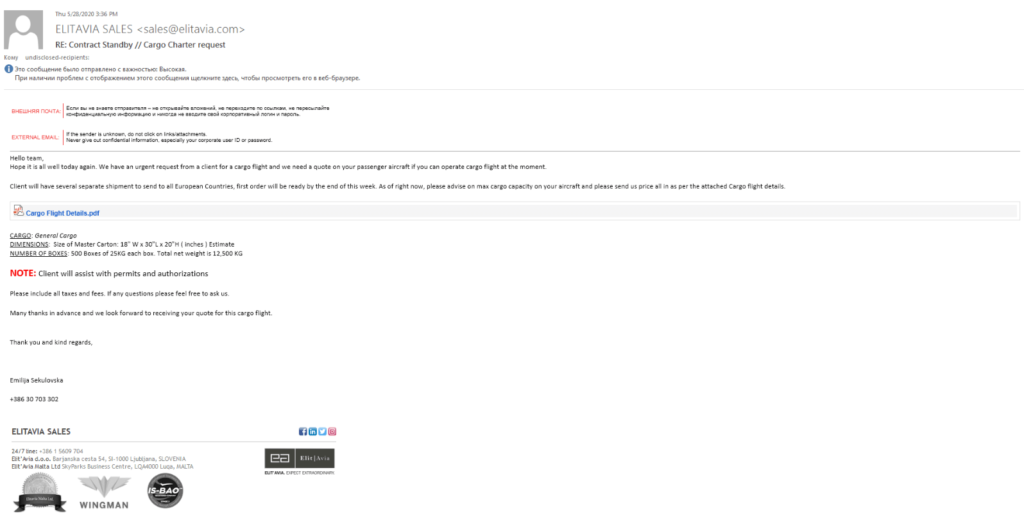
As soon as victim loads the VBSscript into its system, the game starts . This VBSscript contains a malicious DLL which on operating with the power shell, generate a payload into the victim’s system. The installed VBScript is obfuscated to confuse the developers in order to analyze the malicious activities but in this attack the attacker uses a simple obfuscation algorithm that can be reversed using a simple function declared in python.
Now this VBScript will execute further and declare a new key in the windows registry in which it will declare all the values of DLL and executable scripts.
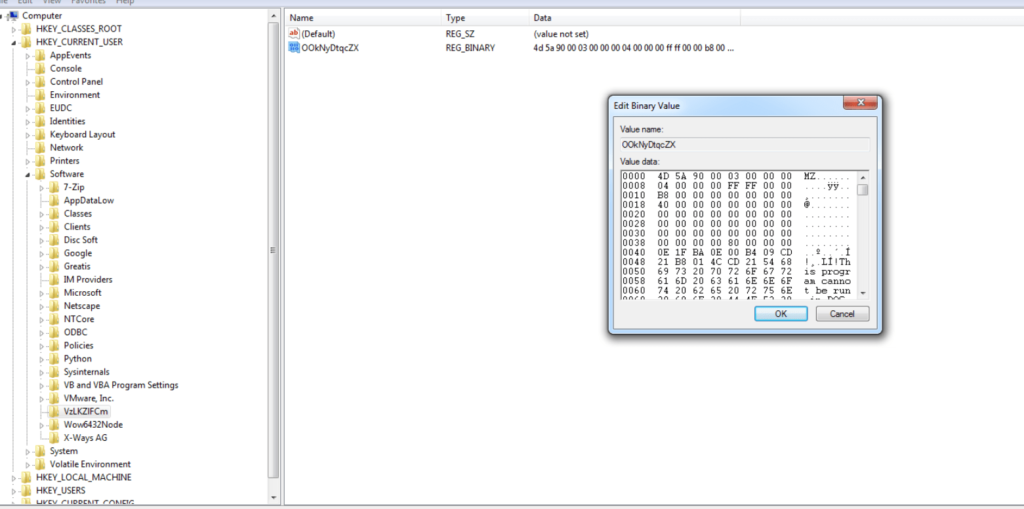
Now the DLL will load the main payload into the system. DLL is dynamic link library file that is used by the windows applications to perform their task . VBScript complete its working with the help of windows registry which uses WMI technology (Windows Management Instrumentation) ,which is used in an enterprise environment to access applications.
The DLL will process and it executes with the power shell and creates a payload svchost.exe. Technically, this svchost.exe file is a safe windows host file that is used by DLL. But here the writer of the malware has used the same name of the file to confuse the end user that if by chance the end user check its running tasks, the victim find all legitimate task in the system. svchost.exe contains one of the malware from this list of malware given here .
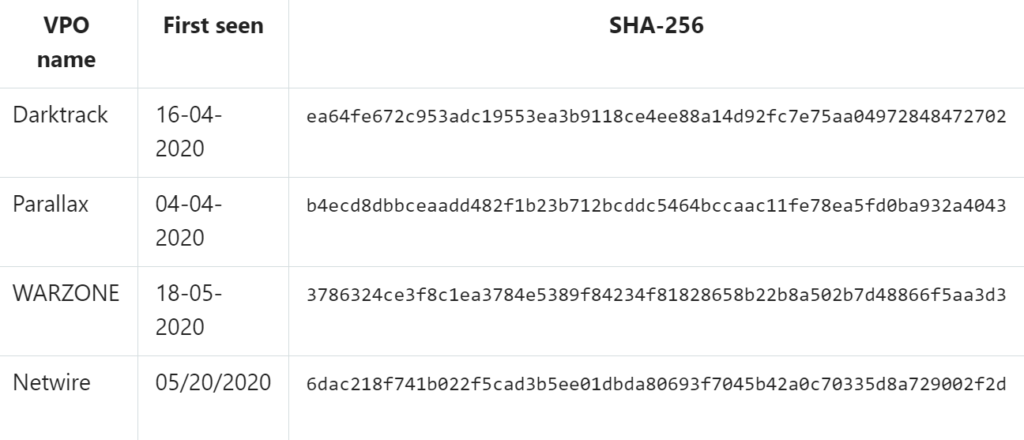
After injecting a payload in the victim’s system, this malware creates a file into the %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\<name>.url, where <name>are the first 4 characters of the parameter VBScript Name. This URL file is thus added to list of files for auto run when the user logged in because if the malware got deleted from the victim’s system, then this script will again call it.
Thus in the end this svchost.exe which contains malware will provide the backdoor to the victim’s system, thus establishing a connection with Command and control server of the malware.
CONCLUSION
This is a malicious campaign which is being launched by a group of cyber criminals which have no criminal records in the past. This malware is currently targeting the European countries and cargo firms. We at Ethical Debuggers suggest you to take care of these points :
- Please reply to authenticated mails only.
- Do not install any file from emails unless you are absolutely convinced. For confirmation, check the file on VirusTotal.
- Keep your system and applications up to date and scan them regularly.






