Tor, a network which was born with a cause, to provide anonymity to some users who are not allowed to access the internet otherwise, in the last decade, has been turned into a great network for cyber criminals and through which you can access the dark net which is a part of deepweb. Generally, with the word “Deepweb” we have created a wrong image in our mind that it just provides the illegal services but it has its own advantages in the field like sensitive researches which cannot be distributed through surface internet.
The fundamental of the Tor browser is to provide anonymity and allow everyone to access the content either it is censored or not. It is the freedom which is given to everyone out on the Tor without knowing their race, caste and sex. But nowadays due to excess amount of cyber criminal activities being originating from the darknet, Cyber Police is even keeping an eye on the darknet to detect what kind of people are surfing these illegal services and how are they using. If you are found doing some obnoxious and you have not used all necessary defenders to completely hide your identity, chances are less that you will be released free.
If we keep the Cyber Police on one side, many corporate and ISPs don’t want their employers/users to surf the darknet because the darknet might deliver malware to their systems and can cause a great exploitation. For those who don’t know, the darknet is accessed with Tor browser. Any URL having TLD as .onion is linked to the deepweb and cannot be accessed with the normal browser like Chrome. The Tor browser connects you to the relay that let’s you access the deepweb network. To block your access, all your network administrator need to do is block access to Tor nodes which are publicly accessible. But due to random changing of these these Tor nodes, it becomes difficult to depend on a static list.,thus making it difficult to block access with traditional methods.
Following these problems, security researcher Dr. Neal Krawetz has researched about two zero days on the Tor network that let’s network administrators to dynamically block user from accessing Tor Network. Let’s see the details about it.
THE ZERO DAYS
To understand both these zero days, first of all we should know the fact that how one can connect to the Tor network. According to the researcher there are three ways:
- Direct method- Using Tor nodes which are publicly available
- Bridge using Meek- Using private Tor node which are not publicly available and encoding the network traffic using a protocol named Meek.
- Bridge using obs4- Using private Tor node which are not publicly available and obfuscating the network traffic using a protocol named Meek.
One uses the last two methods only after he has been denied the access with the Direct method. But here the researcher have even exposed the technique to block users from accessing with all the above methods
The first zero day he found is that of dynamically blocking the user from accessing the Tor network by blocking the TLS signature on the incoming traffic from the Tor server. In his research he analyzed the fact that after performing the TCP three way handshake, the server respond with a self-signed TLS certificate(created when the server was first started) which is very small as compared to the normal certificate issued by the CA on the surface net. Thus, it has very few common details that can be easily tracked. The Tor TLS certificate looks as follows:
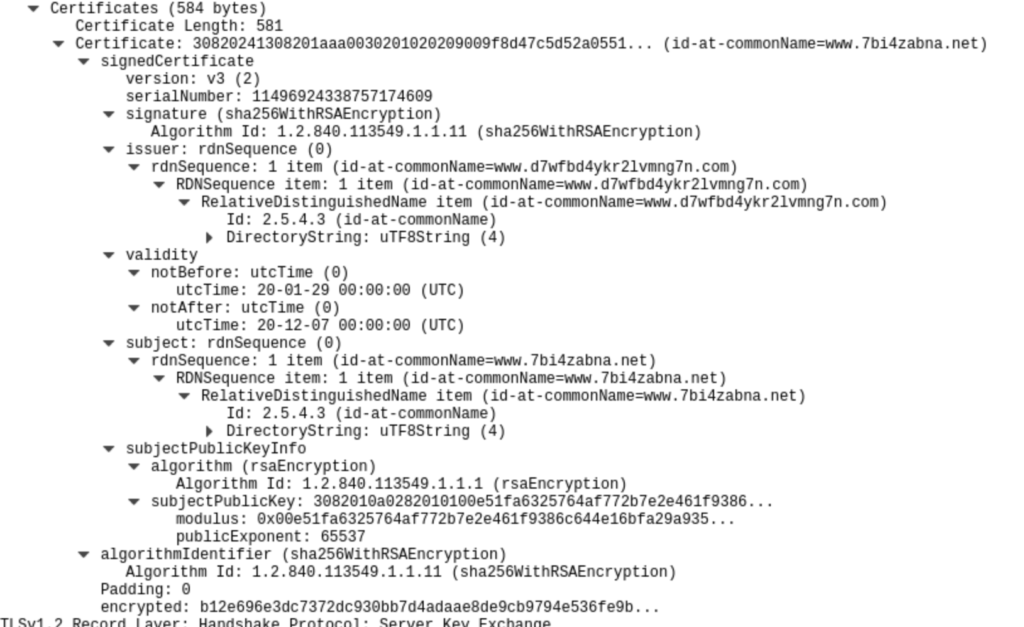
What all the administrator has to do is, enable a packet sniffer on its LAN. As soon as the packet sniffer encounters a TLS certificate from server side, it generates a signature. If that signature matches same pattern to that of same TLS certificate from Tor sever, it should immediately block the connection. This technique is similar to that of used by many of the AV companies to detect malware.
Another zero day which is discovered to block users from accessing Tor network by using the last two methods is as follows. As mentioned above ,bridges are the private Tor nodes which are not publicly available but they can be used to access Tor. To use these bridges, the bridge should be configured with Pluggable Transport(PT) Protocol. This PT protocol is responsible for encoding the Tor network traffic so that it looks different from it. The PT protocols which are used for encoding are:
- Obfs4- It is the PT protocol that encrypts the network traffic and is described as ”look-like-nothing protocol”. It is also known as trojan protocol. It uses well known ports 22 and 443 to communicate with the corresponding bridge. But the fun fact about this protocol is, despite of using popular encrypted ports, it can be easily detected by one who is analyzing the traffic as the headers corresponding to ports and protocols are absent. Thus it is a big indication for anyone to inspect that it is a Tor traffic.
- Meek- It is the another PT protocol which encodes the network traffic and uses domain fronting technique to obfuscate TLS connection. It’s only limitation is that it requires popular hosting platform like Microsoft azure to work. China restricts direct connection to the Tor server. That is why, users from China uses this method to access Tor .
As soon as a user selects a bridge that contains information about the PT protocol information, PT server address, to which the network traffic will be forwarded, he/she is able to access the Tor network.
According to the findings by Dr. Neal Krawetz, connections that are established using bridge with obsf4 can be easily restricted by analyzing the packets as it shows the protocol used to encrypt the traffic. The obfs4 uses an IAT(Inter Arrival Timing) mode to state the network configuration.
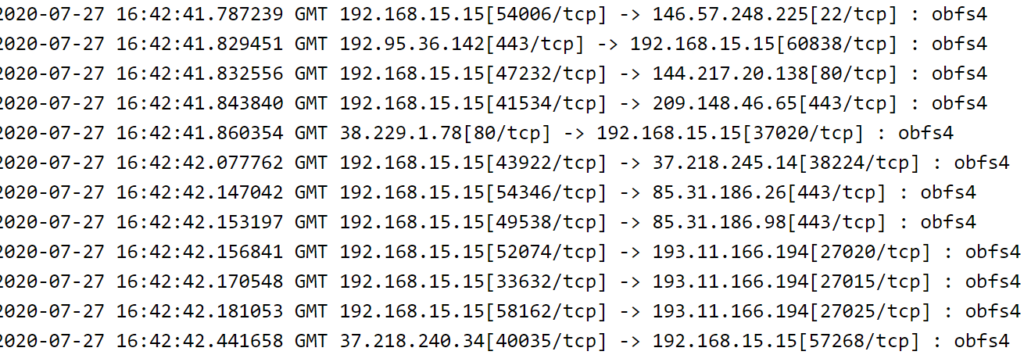
Connections that are established using bridge with meek can be easily exploited by the fact that it uses domain fronting technique. For identifying meek, an observer only needs to track the TCP packets between the client and the meek server (ajax.aspnetcdn.com) that have over 1000 bytes in the TCP payload. The delay over 2 seconds between the request and response specifies the existence of meek protocol and ultimately defines Tor traffic.
CONCLUSION
We saw how anyone who is analyzing your traffic ,either be it your network administrator in your corporate or your ISP can easily block your access to Tor. On reporting these two zero days to the Tor project, they have still not patched this vulnerability and it is still open for anyone to use it.






