The most powerful, efficient and sophisticated language which every developer is addicted to is the Python. Whether they are scientist, programmers, hackers or script kiddies, everyone is just making innovative methods with this language. There are many people who have their first programming experience with this language. They learn to automate complex tasks with this language. As a computer langugae demands, you need to download some modules, libraries that can understand your actual source code. Therefore, python has for and by the developers open source community to support its users. This community is known as PyPi. In the Pypi, we can find thousand of developers contributing to different projects, modules…
-
-
CAN MACROS STILL COMPRISE THE APPLE’S SECURITY SILENTLY? IS IT STILL A ZERO DAY?
In today’s time programmers are so much addicted to automation that they find new ways to automate tasks. The simple reason behind this is whether we are a programmer or a normal human, we find it lame and time consuming to do the same task again and again. Even scripting languages like Python, Javascript made it easier to do complex tasks with a couple of lines of codes. As we are moving forward, the efficiency of writing the code is getting optimized day by day with new languages getting introduced to us. Logic remain same, programmers just need to adapt the syntax. The automation is not just restricted to program…
-
TARGET OF A CRYPTO SCAM? SEE HOW THESE VICTIMS LAUNCHED THEIR OWN SCAM TO COVER LOSSES
Due to this pandemic, non-contact meetings has become an essential rule all across the world to prevent the spread of COVID-19. Many big corporates and officials are establishing or have established a new normal- work from home to lower their losses and maximize their profit. In the view of this, obviously all paper works are being avoided as much as it can be and are being done digitally. So what about money? Obviously, during these days, digitally money has is a major boost to the economy as it has many advantages and so scams related to this money have also increased. From digital money, many are thinking about debit cards,…
-
TOR ZERO DAYS LET YOUR ISP OR NETWORK ADMINISTRATOR TO BLOCK YOUR ACCESS
Tor, a network which was born with a cause, to provide anonymity to some users who are not allowed to access the internet otherwise, in the last decade, has been turned into a great network for cyber criminals and through which you can access the dark net which is a part of deepweb. Generally, with the word “Deepweb” we have created a wrong image in our mind that it just provides the illegal services but it has its own advantages in the field like sensitive researches which cannot be distributed through surface internet. The fundamental of the Tor browser is to provide anonymity and allow everyone to access the content…
-
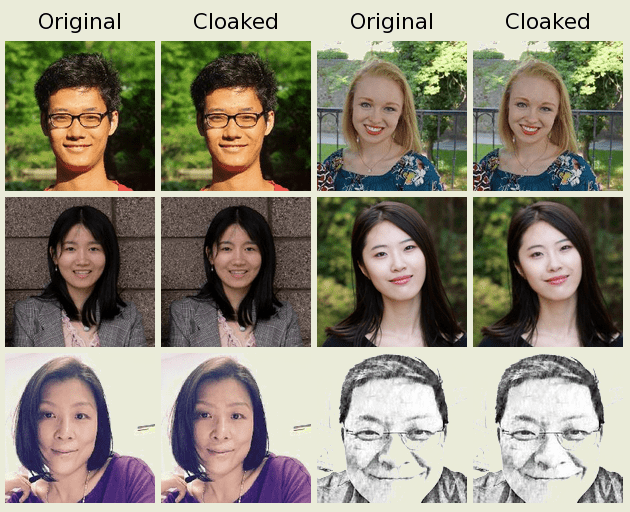
FAWKES: A TOOL WHICH USES ATTACKERS’ TECHNIQUE TO PROTECT YOUR PRIVACY
The most promising technology that people all around the world is working upon is the Artificial Intelligence. This word really misleads what human intelligence means and we as humans think that AI is more capable than us. In these modern day technologies we are making computers capable to identify the real humans, though we should not forget the fact that we humans are the one who are developing algorithms to make a dumb system to act as human. If we see our last decade, there is merely any industry left where automation in not being introduced, starting from tourism to IT and it is predicted that in the upcoming decade,…