Last year might be one of the worst year for all of us as coronavirus affected our life in every aspect, but cybercriminals made this year special for themselves as they made big numbers in their history. The year was all filled with cyberattacks either it was tourism industry or it was a cybersecurity company. There were huge leaks of databases by these criminals, there were privacy issues that come into notice, for some it was going absolutely wrong but still, for some it was going alright.
When the year was coming to end, we all were excited for the new year, we all were looking for a new and positive start but cybercriminals have another view in their minds. Cybercriminals always look to launch new and sophisticated cybercrime campaigns to mark the successful start of the year and this year, they also did the same.
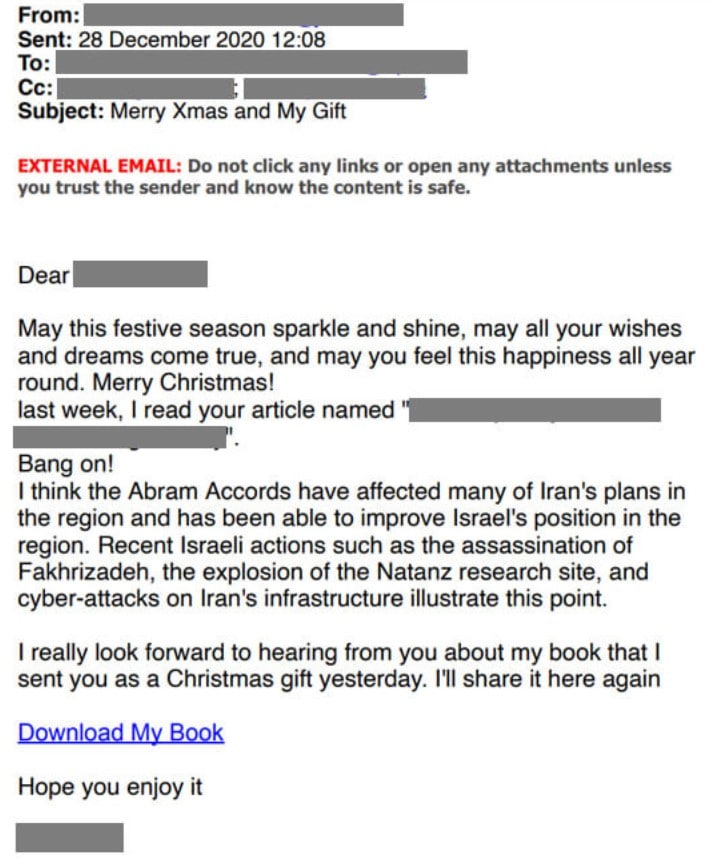
Iranian cybercriminals backed group Charming Kitten also known as APT35 and Phosphorus, were found launching a new and deadly phishing campaign by researchers from Certfa Lab that can even lock tech-savvies into their nets. They were found taking advantage of Christmas and New year’s eve as in this time, in almost every country, common as well as IT people celebrate these days and took a leave from their works to celebrate this occasion. As a result, very few people are available to look after and analyze these cyberattacks and launch preventive measures against them. These cybercriminals took advantage of this fact and launch a sophisticated phishing campaign.
GOOGLE.COM: A CONFUSION THAT WAS THE CAUSE BEHIND THEIR SUCCESS
As we all know Google, Microsoft, and other giants’ domain are some of those trusted domains which nowadays not only humans trust but machines are also made to also trust them as soon as they encounter any domain or subdomain associated with them. A similar thing that also helped these cybercriminals succeed in their idea.
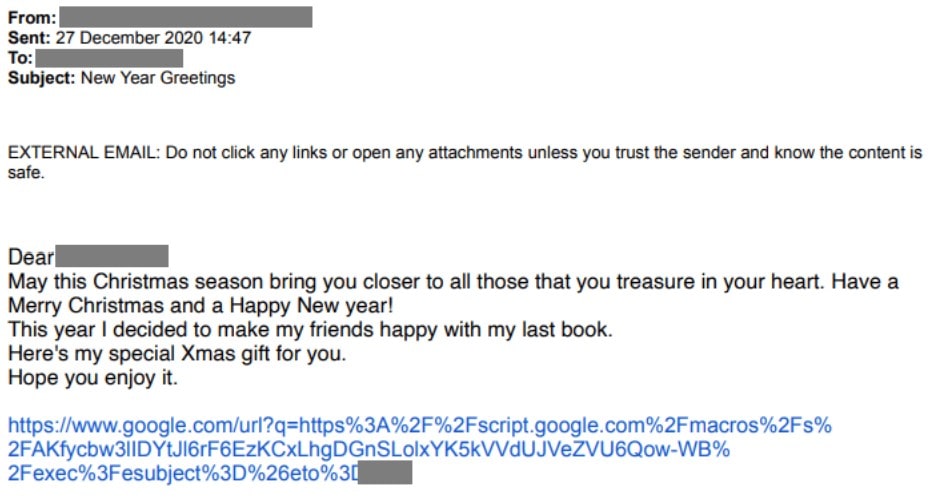
As usual, in the past cyberattacks, these phishing campaigns initiate by sending a text message or mail to the victim that obviously looks very similar to the original one. In the example below, the criminals disguise the original text message that a user receives after the recovery of his google account. As usual, the user is required to authenticate his identity by clicking on the link which has been sent to him.

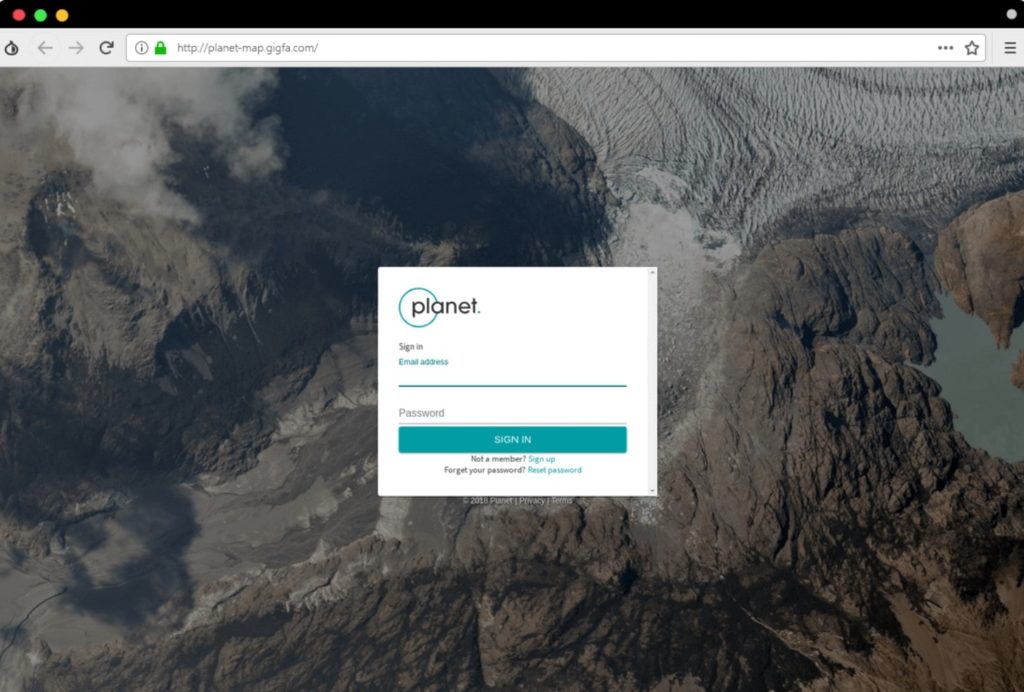
In the above screenshot as you can see, the link looks like a legitimate link as it is from the domain www.google.com. But there is a twist here! If you see the whole URL, it something looks like
https://www.google.com/url?q=xxxx.com
Here xxxx.com belongs to any third party domain which you will be redirected to after click you click this link.
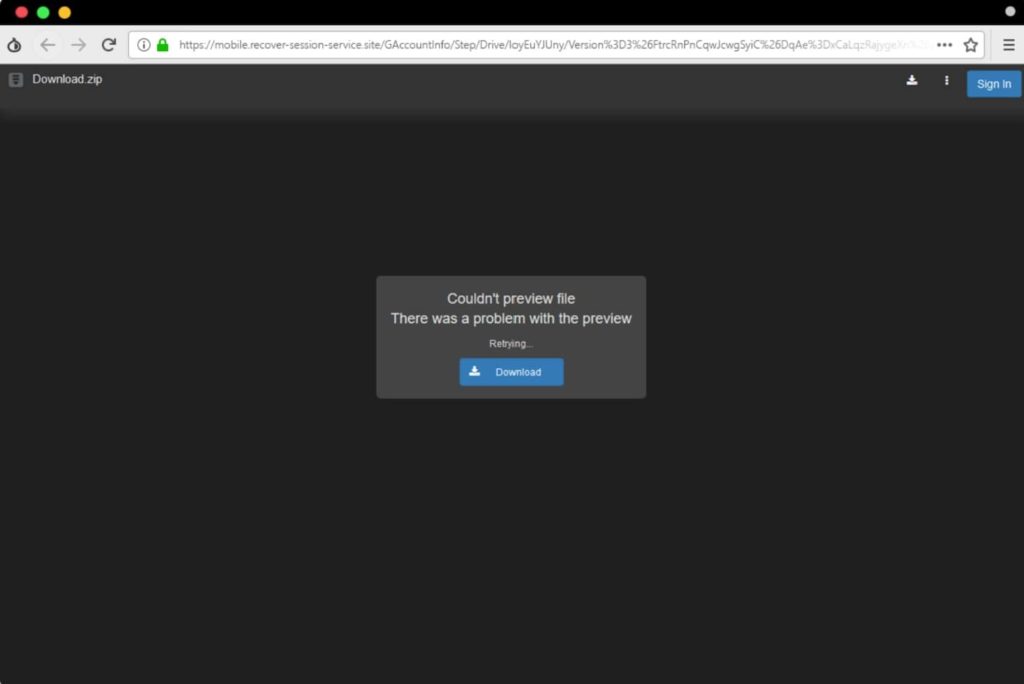
In the above example, as soon as the victim clicks on the link, he/she is redirected to a script that is hosted on script.google.com. It is a place to write scripts for automating the tasks of google services. Here the attackers have hosted a script to define the next path for the victim. Till now the whole process appears to be legal and Web application firewalls and security scanners will fail to prove them malicious.
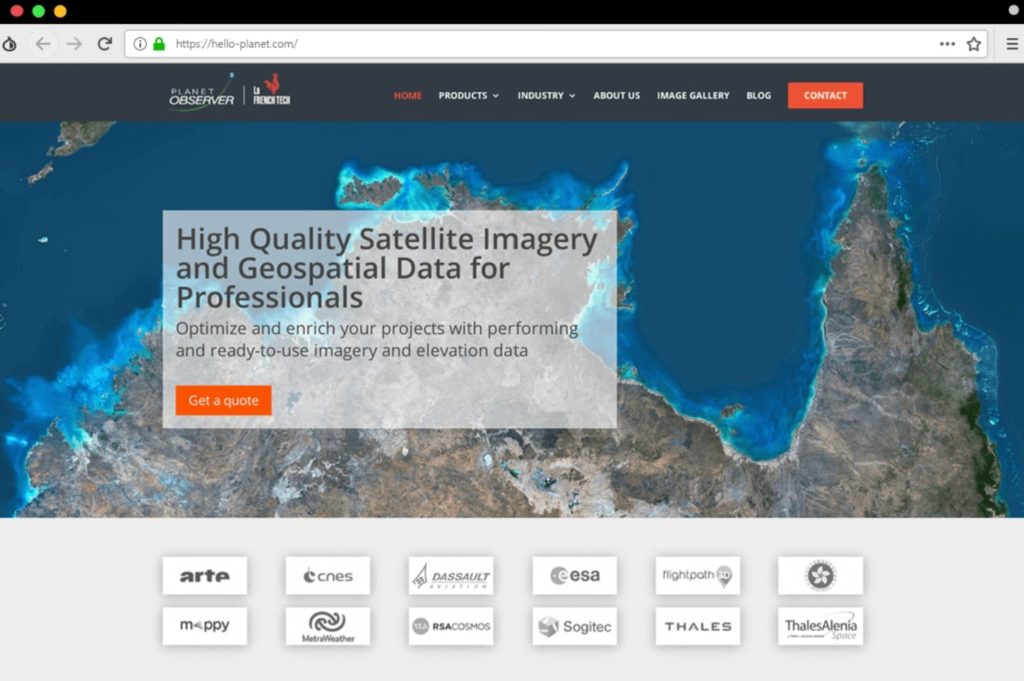
To further bypass the security scanners, the script temporarily redirects victim to a legitimate site that has no harm. Once the security scans have been finished and credibility of the link has been verified, the victims are redirected to the attackers’ malicious websites. Some of the examples of those websites are shown below
The interesting fact about this campaign is that there are several redirects involved in the victim’s browser but still, the end-user is absolutely transparent about the whole process as till 2-3 redirects, this process seems to be absolutely legitimate.
As shown above, these are some of the examples of the malicious websites that the victim will finally be redirected to and these all are either aim to steal account credentials or to download a trojan in the victim’s device. The group has some other email campaigns also that are found by the researchers which aim to attack people from different groups and uses the same technique for redirection to attack the victim.
CONCLUSION
The above-explained attack mechanism shows the intelligence of victims and the skills of the attackers. For a while, a tech-savvy or a professional can also get caught in this campaign. Therefore, we at Ethical Debuggers suggest our readers to take the following measures to enhance their online security.
- Use a secure network to communicate.
- Double check the link you are clicking on.
- Verify the credibility of the website on which you are entering your information.
- Use incognito mode or privacy mask to establish a secure session and removing the cookies for login.
- Terminate the session as soon as you encounter too many redirections.
Some great deals to check out for:
- Become zero to hero in cybersecurity using this The A-Z Cybersecurity Developer Bundle which contains more than 170 hours+ of instructions from reputed trainers at just $39.99. To buy or know more about this deal, click here. Original Price: $999
- Protect your online security with Nord VPN and Nord Pass Manager. Buy a 2-year subscription for this combo at just $99.99. To buy more or know more about this deal, click here. Original price: $406
- Protect your system with Heimdal™ Thor Vigilance: Next-Gen Antivirus at just $39.99 for 5 years. To buy it, click here. Original Price: $249
Disclaimer: The above-suggested deals are from third-party vendors and prices mentioned for the above deals may or may not change at the time you buy. We are not responsible for the change in price after 24 hours.