We know that if we want to hack the systems we need to follow the following steps: Information Gathering Scanning Exploiting Getting the access Maintaining that access It is believed that if one follows all the steps mentioned above, there are very less chances that an attacker is not able to attack his victim. But, do you know what do you need in order to carry out all the steps mentioned above? In this article, we will take you from the roots to fruits of hacking . We will use Nmap (Port Scanning tool) to gather information and scan ports on our target and Metasploit Framework (a framework that contain…
-
-
SET UP YOUR OWN LAB
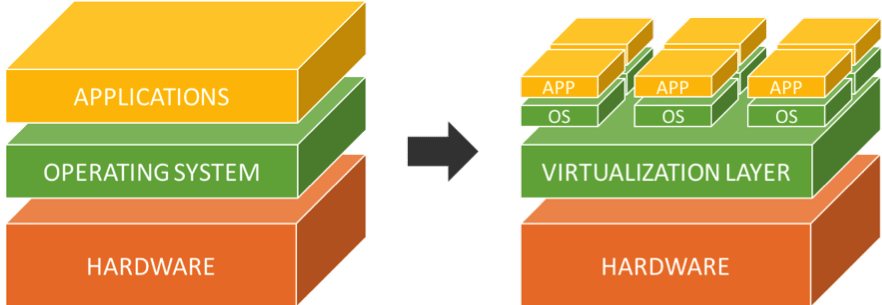
For those who are new to hacking, it is really important to dirty your hands on several types of operating systems but do we need to have different devices in order to run several OS? The answer is NO. You can easily manage more than one operating in a single device based on your configurations like RAM, Storage, Network, etc with the help of virtualization software such as VirtualBox, Vmware, Parallels (MAC) etc.. Virtualization is the process of running a virtual instance of a computer system in a layer abstracted from the actual hardware. In simple words,it refers to running multiple OS on a single device simultaneously. Virtualization allows you…
-
INTRODUCTION TO HACKING
Many beginners get fascinated by the word HACKING ,but do we know what is behind this “Mysterious” word? The first image formed on thinking about this “Mysterious” word is of “A man with a black hood, typing commands with an evil smile.” Have you ever wondered why this “Mysterious” word is interpreted like this? The simple reason behind this is that Movies have picturized this “Mysterious” word in this manner. Beginners believe HACKERS are MAGICIANS . But this is not the reality. HACKING is a field just like any other field. Like a company needs Cost Accountants, Lawyers, Software Engineers etc.,in the same way it needs security researchers or in…