Back in mid-2018, Trend Micro researchers revealed a campaign that was targeting Japanese and Korean Speaking users with a trojan or we can say infostealer named as Fakespy. This campaign impersonates the end user of being a legit banking app but ended up delivering trojan in the target user’s device.
Following this campaign, today some researchers from Cybereason unveiled this campaign which has revived with more capabilities of affecting its users. Now this campaign is not only targeting the Korean users, but it is affecting users all around the world, especially users in countries like China, Taiwan, France, Switzerland, Germany, United Kingdom, United States, and others.
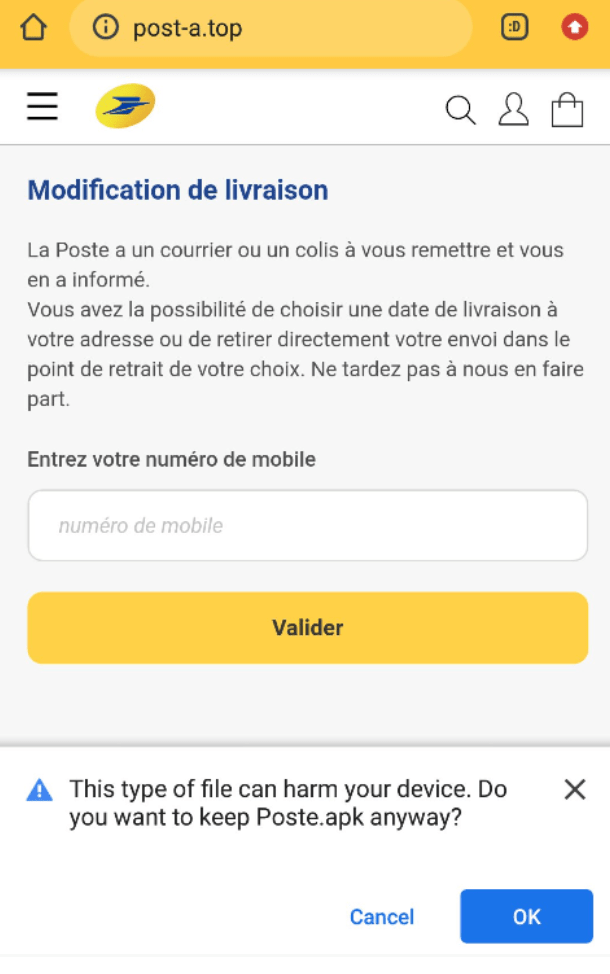
This campaign targets its users with a technique of smishing. Smishing comprises of two words SMS + Phishing which means that this campaign targets its user by sending a SMS which contains a phishing link that redirects it’s users to download a trojan named Fakespy. This SMS spoofs as legitimate postal service apps and transportation services in order to gain the users’ trust.
This time again the threat actors behind this campaign are found to be Chinese actors named Roman Mantis which has a past criminal record. Since the beginning of this worldwide outbreak, there has been several attacker’s group which emerged as of now. Due to remote working, it has become easy even for script kiddies to spy on you. Do these attacker use a similar strategy? Let’s move forward and analyse this attack.
ANATOMY OF THE ATTACK
As mentioned above the target of this campaign receives a SMS which contains a phishing link, following the technique of smishing. This SMS received by target usually contain details about postal services, in which they are found to be claiming their target that they had missed a parcel which was addressed to them and if they want to receive this parcel back they had to download this app from link given below in the SMS. Here is the message which was delivered to members of some European Countries and the app which attackers want their victims to install.
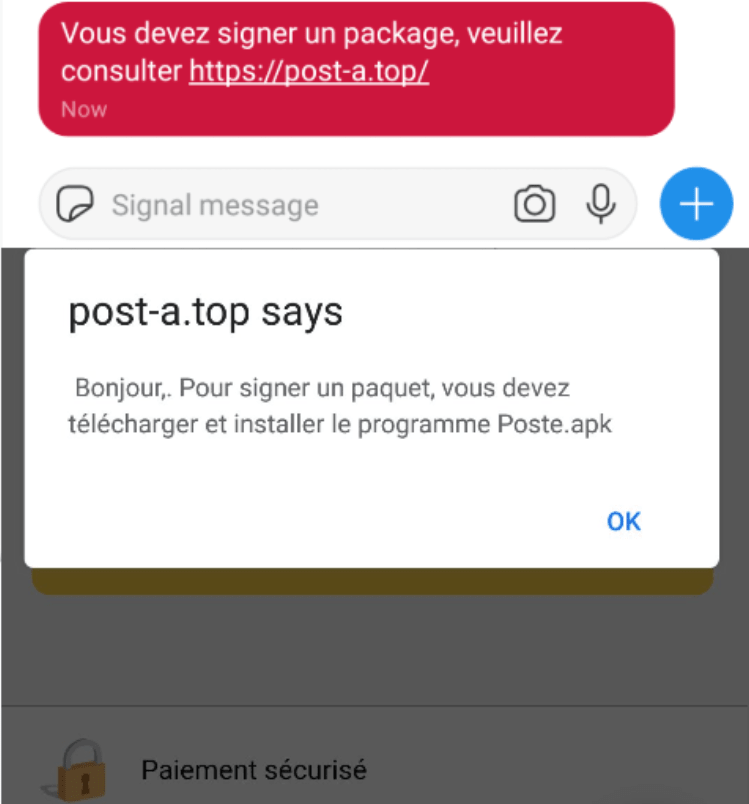
As soon as victim clicks on the above link, he is redirected to a new phishing website where he is convinced to download one of the following apps:
- United States Postal Service
- Royal Mail
- Deutsche Post
- La Poste
- Japan Post
- Yamato Transport
- Chunghwa Post
- Swiss Post
- Deutsche Post
These all above mentioned application, though have legitimate names and their User Interface, but after victim downloads the app it looks same as that of legitimate application, but there is a small twist in this.
The authors behind this phishing campaign has used a technique of Web view, which allows all these fake applications mentioned above to show an original web page of the application. But in the back end of the application, this trojan is running its own scripts and stealing information.

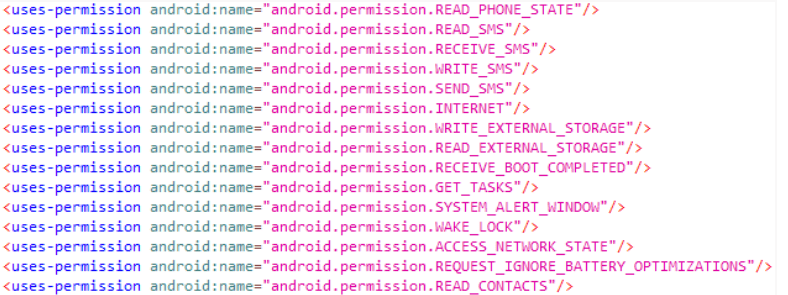
On the stage of installation, the victim is required to give the following permission to the appliations. We all know that legitimate apps require some access to the resources on your device to give you more functionality and automation and thus here these bad actors take the advantage of the same trust on the user’s end. The app requires the following permission from the user:
READ_PHONE_STATE
READ_SMS
RECEIVE_SMS
WRITE_SMS
SEND_SMS
INTERNET
WRITE_EXTERNAL_STORAGE
READ_EXTERNAL_STORAGE
RECEIVE_BOOT_COMPLETED
GET_TASKS
SYSTEM_ALERT_WINDOW
WAKE_LOCK
ACCESS_NETWORK_STATE
REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
READ_CONTACTS
Here is the code snippet inside the application which takes the all these permissions inside the app.
After the user has successfully granted all the above mentioned permissions, the malware(Fakespy) reads all the sensitive information from the victim’s device as you can see that all the above requested functions points to your personal data inside your device.
It then collects the information from your device and sends it to its Command and Control Server which has TLD as .club and its URL ending with /servlet /[C2 Command] which is registered by a Chinese organization.

The malware sends the following information to its C&C server.
Victim’s Mobile Number
Machine
OSversion
Bank
Internet Service Provider
NPKI (National Public Key Infrastructure- might contain authentication certificates related to financial transactions)
CONCLUSION
We all are well aware of the fact that though China is the largest manufacturer of the electronics of all times, but in recent times we all have seen that it is too producing products and techniques that are destroying the human’s privacy as well as their lives. The new origin of techniques of phishing are being manufactured by China. The best method we would suggest you to prevent phishing or any similar attack is:
- Use Virus Total if you find any suspicious thing in message received from any source.
- If you are not supposed to get mail from an organization do not reply it.
- Always check the link to which you will be redirected to and verify it through an updated Antivirus .