Owning a smartphones nowadays is not at all a point of consideration. As we are moving digital, smartphones have too become our necessity with air, water and food. A smartphone is the best combination of all the privileges. From child to parent, everyone in the house is privileged to access the internet with the help of this smartphone which was limited to some people before. But what about those who can’t afford a $300 mobile device? Nowadays, this has not been a problem as Chinese manufacturers are there to help. We all know that China is the largest manufacturer of electronic goods. Despite being the largest, Chinese manufacturers provide cheap…
-
-
THE TRANSPARENT BLOCKCHAIN: CATCHING CYBERCRIMINALS FROM THEIR ANONYMOUS WORLD
We all know that cryptocurrencies are the only way to do anonymous transaction. Either it is FBI or NIA, they find it impossible to track the record of transaction made through cryptocurrency. Every technology geek in today’s time have tried to understand the concept of cryptocurrency due to its growing popularity. In many countries, the cryptocurrency is banned but still it a trending currency in the cyber criminal underground world. But do you wonder what makes it trending in the underground? Well the answer for this question is straightforward. As said above, the cryptocurrency provides a way to cyber criminals to make their transactions absolutely anonymous. What this means is…
-
ONE RANSOMWARE, TWO FAMILIES
Every organization, corporate or company invest a large amount of their revenue in protecting network infrastructure from cyber attacks. Though cyber criminals sometimes have strategical target, they can unconditionally attack any organization . For the organizations which got attacked, it becomes very difficult to recover data and revenue which it lost while recovering from attacks. The most damaging tool for cyber criminal is to infect the victim’s computer with a ransomware. The simple reason behind this is the hard encryption which is almost impossible to decrypt. But some security experts with much experience and exceptional knowledge are able to do so. These ransomware operators generally encrypt the victim’s file using…
-
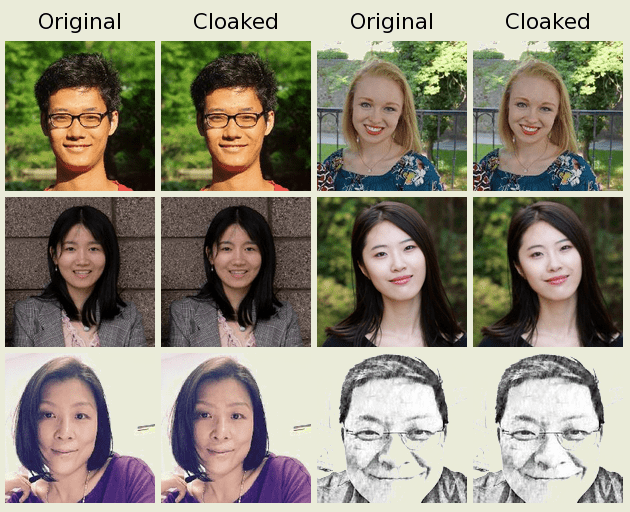
FAWKES: A TOOL WHICH USES ATTACKERS’ TECHNIQUE TO PROTECT YOUR PRIVACY
The most promising technology that people all around the world is working upon is the Artificial Intelligence. This word really misleads what human intelligence means and we as humans think that AI is more capable than us. In these modern day technologies we are making computers capable to identify the real humans, though we should not forget the fact that we humans are the one who are developing algorithms to make a dumb system to act as human. If we see our last decade, there is merely any industry left where automation in not being introduced, starting from tourism to IT and it is predicted that in the upcoming decade,…
-
LINKEDIN IS SPYING ON THE CLIPBOARD.
Over the last one week, there has been controversy in the market that Tiktok is spying on your clipboards. Some security researchers and organizations found out that some other apps are too doing the same which raises security concerns for the end user. This is just because of the new ios14 feature which exposed these apps. Privacy is a big concern to all of us in today’s time. We can spend a lot of money to keep our privacy intact but we just can’t let any company to secretly spy on our private data. The GDPR consent which users signs either he visits a website or signs up in an…