DDOS attacks are emerging day by day. We know that DDOS attack is simply sending lots of packets to the remote server that server is not able to handle, thus making it unresponsive . In short, we test the limits of the remote server . But this group changed the definition .
Coming back to 2018, Trend Micro Researchers unveiled a new group named Outlaw Botnet. In 2018, this group targeted Japanese art institution as well as a Bangladeshi government site over a vulnerability on Dovecot mail server. They have been involved in these cyber criminal activities for past couple of years. This time again they regain their presence and marked 20,000 Linux servers with their attack in China, as founded by researchers of Tencent Security, which has affected thousands of businesses in China. But why we said this group give a new definition to DDOS attack? What’s unique in their attack?
You must have heard that they deliver shell bot to their victims. In 2018 , they exploit the Shell Shock Vulnerability in the Remote Server. This vulnerability allows an attack to do remote code execution on the remote server. But they changed their trend and now they are delivering this Shell bot by attacking the remote server with SSH brute force. It means that they exploit the File Transfer Protocol which is used by web administrator or even a remote user to do tasks like modify,append or delete on the remote machine.
The term shell bot here is used instead of bot just to mark the significance of the fact that this bot is delivered by exploiting the Shell Shock vulnerability. This group is directly targeting on server and making them:
- To launch DDOS attack on other machines
- Install a trojan in their server to monitor their activities.
- Making their servers a cryptominer
That’s why we said they give a new definition to DDOS attack. Let’s see the anatomy of their attack.
ANATOMY OF THE ATTACK
After they have successfully comprised their target server, this group first downloads TAR compressed package file dota3.tar.gz which consists of Perl shell scripts, miners and trojans. Then after this TAR has been decompressed, then using rsync command, attackers stores the initialization script in the root directory of the server in which all the libraries related to bot are initialized. Shell bot backdoor in B directory which is absolutely obfuscated and it establishes a connection with its Command and Control Server – 45.9.148.99:443. This backdoor can provide remote shell to the attacker and he can do a lot more fun with the server.
It also stores mining trojan in the A directory and finally SSH brute forces instruction to attack on the other machines in the C directory of the server.
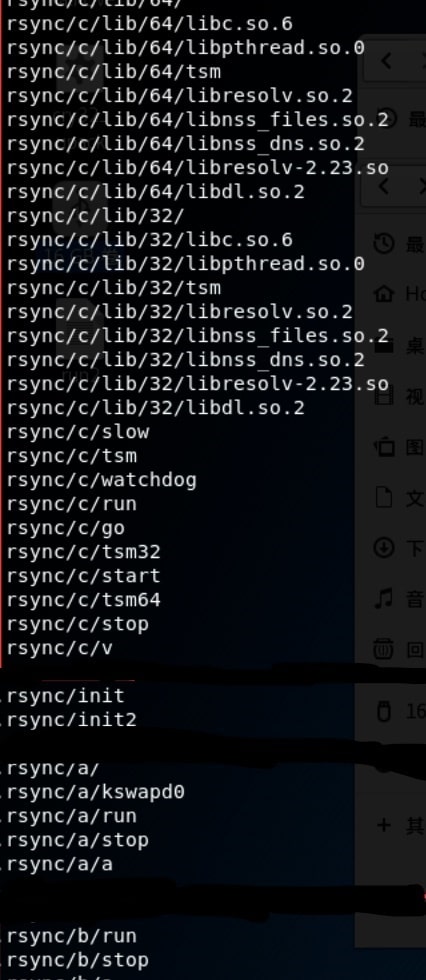
In the initialization phase, the malware creates a /.configrc directory in the current user directory, copy the a and b folders to the root directory and then writes the cron.d (cron jobs) which are installation scheduled task for persistence.

The kspwapd0 in the above screenshot is the name of the crypto mining trojan which mines Monero Cryptocurrency which is nothing but an open source XMRig crypto miner. Also the instruction which were stored to attack on the other machines in the C directory are the binary files which are stored in the name of tsm32 and tsm64.
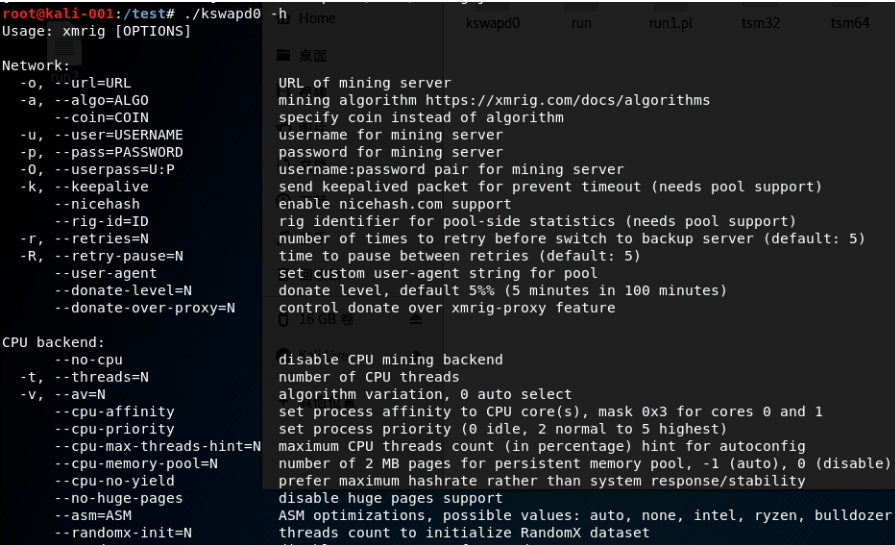
In the end, the malware is downloaded which modifies the public key of the remote server to make wider access to the compromised system by typing the command
AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1 + 5O73fcBOx8NVbUT0bUanUV9tJ2 / vD0EpZ3Tz 9p7 + / + 0kX34uAx1RV / 75GVOmNx 9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5 + + + rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww BgTFB i6rBLAsPKgAySVKPRK + + + u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6 ORW ==
CONCLUSION
During this lock down we have seen that there is large number of increase in DDOS attacks as many cheap tools are available in the market. We suggest our readers to keep a firewall and regularly scan their systems to avoid these attacks.






