It is a well known fact that Cisco is the most popular brand whenever there is demand of networking products in your organizations. In the past some years, Cisco has been serving well to its customers as well as maintaining its quality and servicing so that it’s customer can perform better. No doubt they are the best, but what if this name can let your organization in danger?
Yes, you heard it right. A similar kind of situation has bee analyzed by the researchers of F-secure labs. Still it is very difficult to believe on the fact that someone can compromise the security of organization under the name of Cisco. Across all the world, whether they are schools or they are big organizations, Cisco is always a first priority and we all are well aware of the fact that if the network infrastructure of an organization gets compromised, how much loss it can cost to the people who are in anway connected to that organization.
In this scenario, the researchers unveiled about an organization which accidently bought counterfeit product in the name of Cisco from a vendor. As the name Cisco itself is a very big brand and so its products are expensive than any other opponent. The simple reason behind this is that their products are highly engineered and are made to use to the end person after several testing. Some bad actors manufacture their products at low cost than their originals which have almost undetectable differences and thus the vendors and buyers both get confused between fake and the original. Thus, the network security gets in danger as happened with that organization.
FACTS THAT DEFINE DIFFERENCES
As mentioned above, the organization bought network switches that resulted to be counterfeited after a software upgrade when it failed functioning. The first difference that researchers saw between counterfeit and original product is external difference between the product which is a very slight. The colour difference between the physical ports.
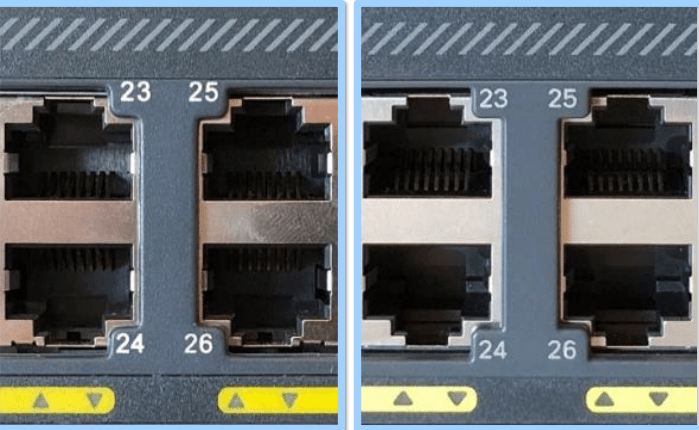
Absence of holographic sticker on the products:

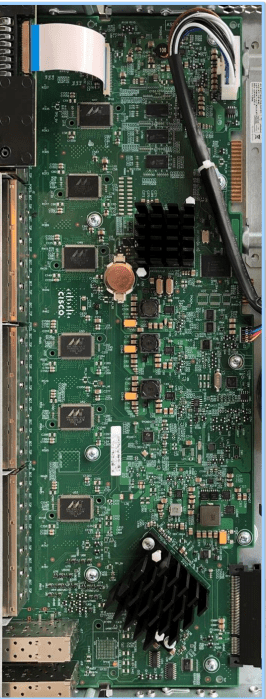
As we all know that Printed Circuit Board(PCB) is the essential component of any electronic component, there are minor differences in the designing of that boards.
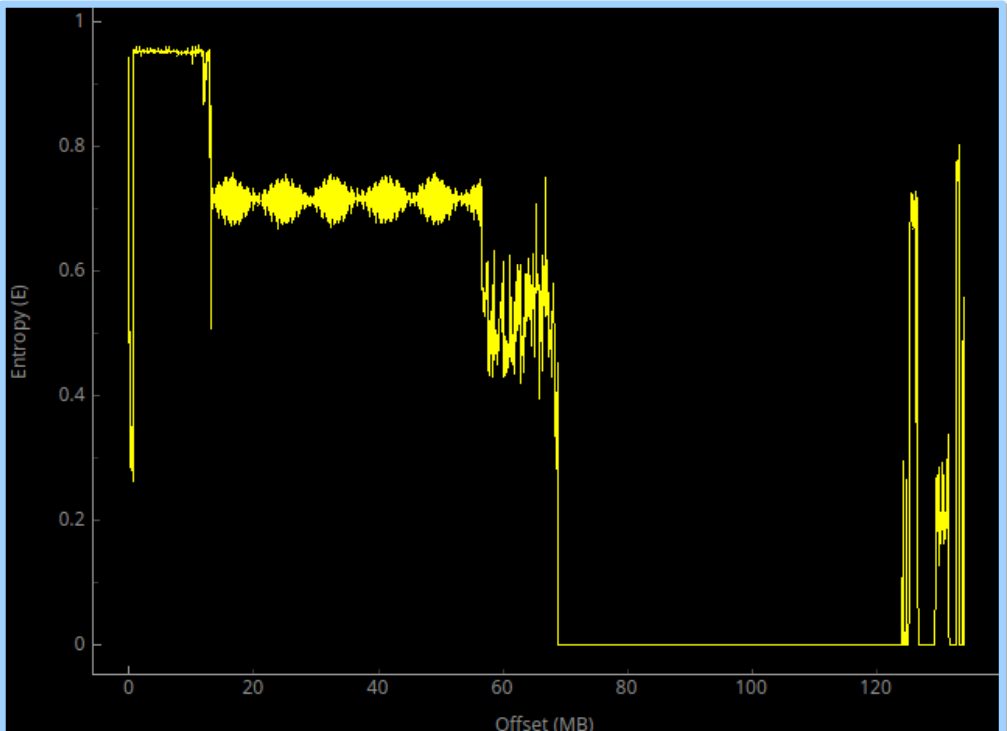
Analysis on how flash content is stored on both the device either it is counterfeit or original is being done by the researchers. The researchers done this using a tool named binwalk which is a linux tool to search a given binary image for any embedded code. They are able to conclude that they both use different firmwares.
CONCLUSION
We all know that how privacy matters a lot to us. We above see an example of organization who just bought counterfeit products instead of real one. Though, these don’t have any pre installed backdoors on them but the way they store and process data is exposing network infrastructures to attack. Therefore, it is suggested to only buy products from verified and partnered vendors of the company.