Nearly 6 months ago, tech giant Microsoft once again uncovered the techniques used by malicious CHIMBORAZO group to deliver info-stealer in the victim’s machine. On January 31, Microsoft tweeted that Dudear which is one of the biggest malware campaign is delivering info-stealing trojan Gracewire by attaching HTML redirectors in the email delivered to victims. These Evil Corps attached a downloadable Excel file attaching a malicious macro that drop the actual payload Gracewire trojan into the victim’s system. Following this group since January, in the 18 June, Microsoft again announced a new technique by this group delivering the same trojan into the victim’s system.
This Dudear campaign is being run by the TA505 group, who is behind the Locky Ransomware and Dridex banking trojan launched various malicious campaigns related to coronavirus in the recent times. This group has targeted many organizations, big firms in the past. This group has been active since 2014 and are continuously launching new variants of their ransomware. This group is one of the most financially motivated groups out there as seen from their activities from past few years. Let’s analyze the anatomy of their activity.
ANALYSIS OF THE ATTACK
This group has deployed a network of Necurs botnet which in history has already affected more than 9 nmillion computers globally. It is believed to be operated by criminals based in Russia and has also been used for a wide range of crimes including pump-and-dump stock scams, fake pharmaceutical spam email and “Russian dating” scams. So in order to send phishing emails to victims, the group uses this network of botnet will send you a malicious URL or an HTML document in in your email. If you receive an HTML document, it will contain a malicious URL in the iframe of sent document or if you receive a URL, you will be redirected to a site that is compromised by this team of hackers.
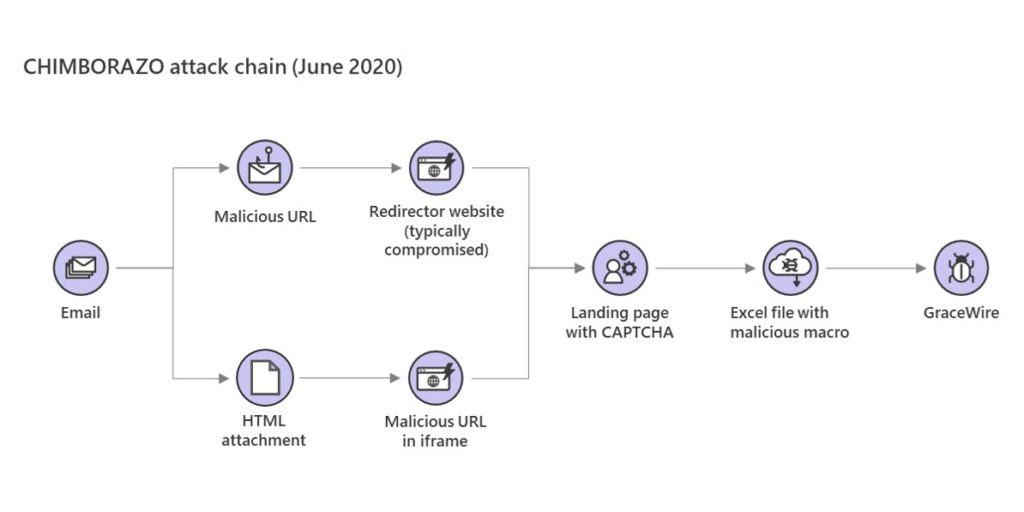
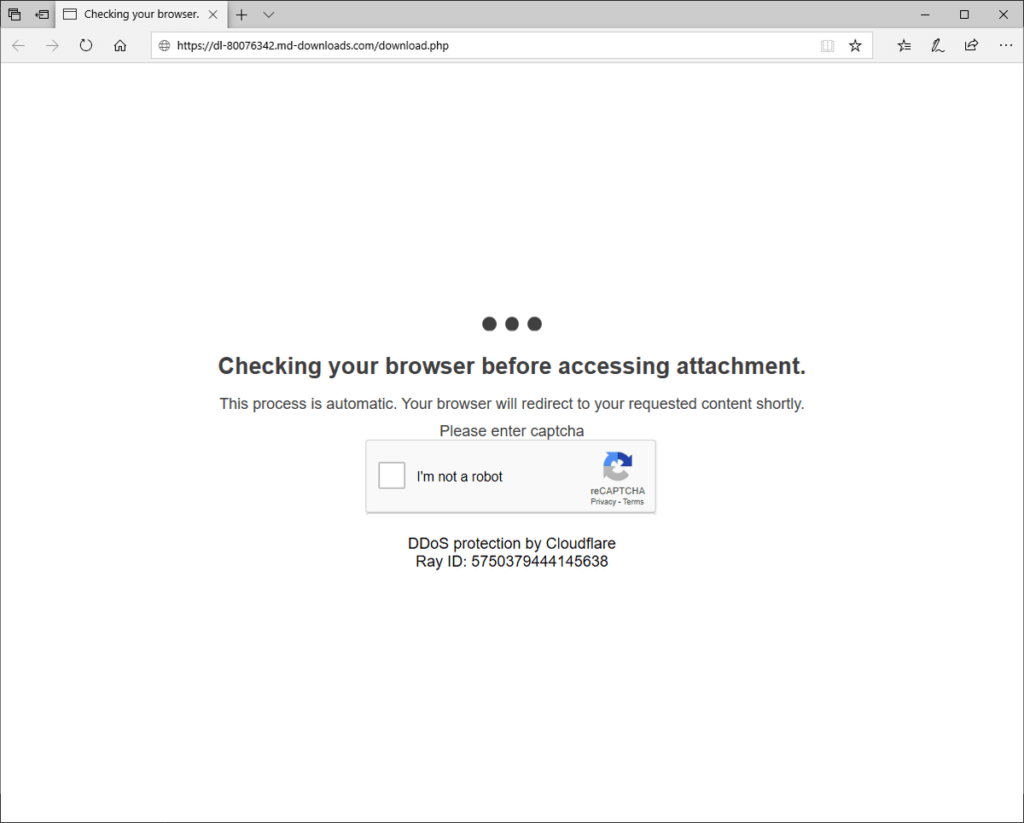
Their ultimate moto is to redirect to their malicious site either this way or the other way. Then as soon as you land on their website, you will asked to pass the test of captcha.
There are two reasons for this
- First they don’t want automated analysis to be done on their website by researchers.
- Second is they want to win the trust of the user as recaptcha is trusted and is used to authenticate that if the end user is bot or not.
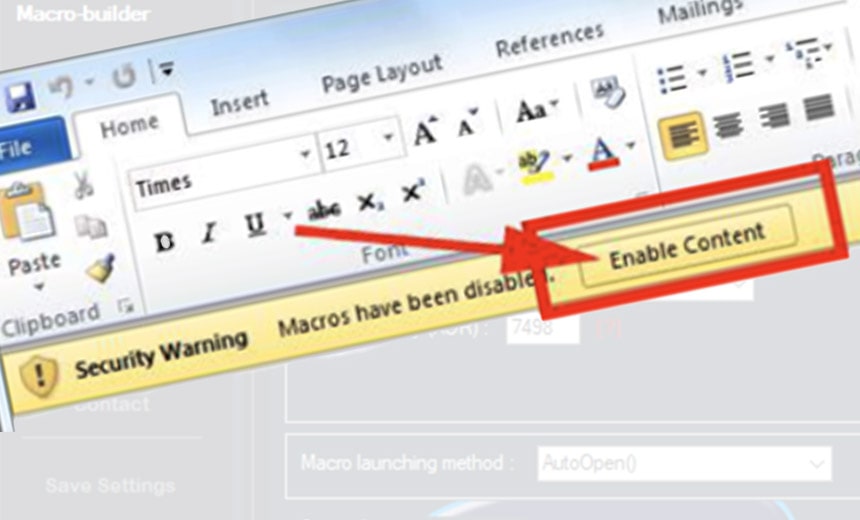
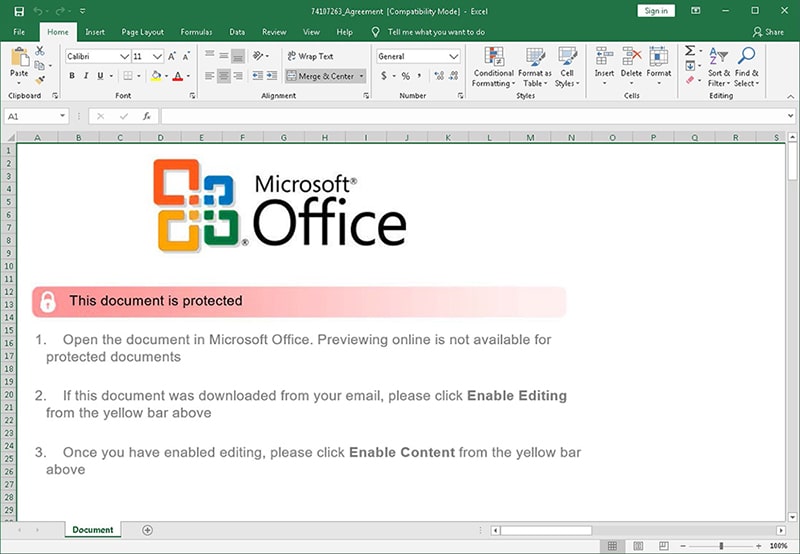
As soon as the user pass the test of recaptcha, website will asked to download an Excel File with malicious macro. A macro is used in Excel to automate the keyboard and mouse input actions. After the Excel file has been installed by the user, it will ask to enable that malicious macro.
As soon as the user enables that malicious macro, it will start downloading the the main trojan Gracewire also known as the FlawedGrace payload. This Gracewire payload. This malware is one of the most dangerous malware as it is capable of:
- Command Execution- This trojan can run arbitrary scripts that allows the attacker to do some task that can be with or without privileged rights.
- Information Gathering- It can easily gather information about important data from your system and send it to the attacker on remote system.
- System Manipulation- This trojan allows an attacker to play with your system.
Deliver another malware- This malware can installed other malwares like keylogger into your system.
CONCLUSION
Microsoft intelligence team is taking proper actions to detect this malware. Windows Defender has already been updated with this about this antivirus and as soon as it detect this malware, it removes it. The team at microsoft have also released the hash for the Excel file and the payload so that you can check the hash for the malicious file and verify them. The hashes are: For Excel file:- c78cd6f7c29bb50d9a5cb2c4fd1be693ca988197ba5add87fb1b49ef7e91b04f
For malware that will be downloaded:- 955dbc7e39627002a5a9ef1199257a980697ceabb14c24ad46a4067c6252439e
Algorithm used: SHA-256
Additionally the team at Ethicaldebuggers suggest you to follow these steps:
- If you doubt to have receive the email message from unauthenticated source, do not even open it.
- Check all the URLs you receive via social media or any source with VirusTotal and check it’s report.
- Always test the unauthenticated media in a virtual evironment or sandbox.
- Keep your all privacy settings off in your windows.
- Make sure you regularly scan your system for viruses and you are using an updatd version of windows.