In this article, we will talk about a campaign which is being run by Chinese Cyber criminals and this time they don’t want to watch what we are doing, rather they want some resources from our system to mine cryptocurrency.
Some researchers from Barracuda have researched about a new variant of Golang(a high level language) malware that is making victim’s machine a cryptominer.This malware does not affect our local machines, rather it targets the back end servers which are either running on Linux or windows. They directly attack on the backbone of a web application framework and exploit some vulnerabilities in the server. After getting settled inside the machine, they start to mine Monero Cryptocurrency. Unlike other cryptocurrencies, Monero is an open-source cryptocurrency created in April 2014 that focuses on privacy and decentralization. Monero uses an obfuscated public ledger which means that anybody can broadcast or send transactions but sender and receiver always remain unknown about their origin. This open source cryptocurrency is used for illegal purposes and generally the evil actors use this cryptocurrency to accept payments anonymously from their victims. Let’s see the anatomy of the attack.
ANATOMY OF THE ATTACK
After getting installed in the server, this malware start downloading some files from its C&C server. The first file it downloads is an init script. This init script sets an environment for the cryptominer to run the actual cryptominer on the target server. Based on the attacking architecture, this malware install init.sh or init.ps1 based on the architecture of device, init.sh for Linux and init.ps1 for Windows. The researchers behind this malware also said that this init script for linux is even capable of removing competing miners and malwares, blocking ports, adding backdoor keys, and disabling SELINUX. The next script the malware downloads is the update script (same as .sh or .ps1 for Linux and Windows respectively), that run as a scheduled task in the server.
After these scrips get installed in the victim’s server, the malware download the actual cryptominer sysupdate in the victim’s server which is actually a XMRig Miner to mine the Monero cryptocurrency. This XMRig Miner is a legitimate cryptocurrency mining program that is used to mine for cryptocurrency using a computer’s CPU. This miner is a open source miner and is generally used by malware or trojan developers to extract cryptocurrency from the system.
After miner get started on the victim’s system, the malware calls a watchdog from its command and control server to monitor all the processes. This watchdog monitors all the processes, and check that the miner is working properly and all the components are updated . If the connection gets lost, this watchdog re initiates the connection to the server. This watchdog gets installed as a sysguard or sysguard.exe based on the architecture of the victim’s device .
In the next step, the malware installs a clean.bat file that works as a backdoor in the victim’s system. After that a scanner is installed as networkservice or networkservice.exe based on the architecture. This file will search for vulnerable machines inside the network of the server machine and installs this malware in the neighbouring machines if found vulnerable and report the machine status to the command and control server of the malware which is hxxp://185.181.10.234/E5DB0E07C3D7BE80V520.
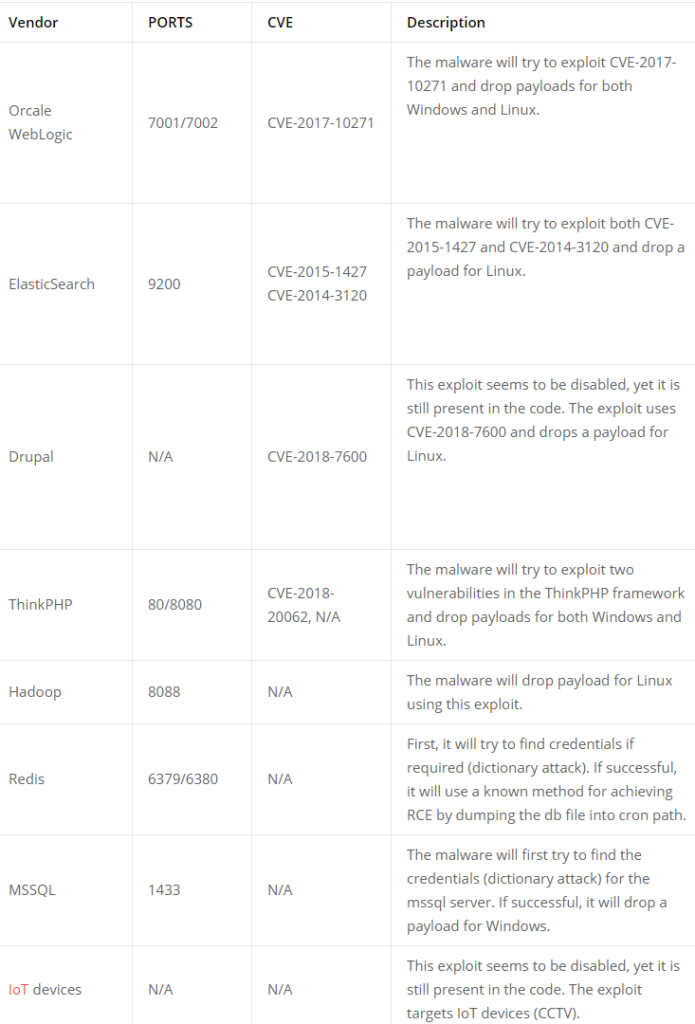
Additionally, this malware tries to exploit vulnerabilities of the server and the server which is targeted mostly is that running Think PHP framework as it is the most popular in china. Here is the list of some vulnerabilities which this malware tries to install in the target server:
CONCLUSION
This is a Chinese malware based attack as researchers have analysed the source IP address from China. Now , amidst this pandemic we come across Cyber attacks originating from China nearly everday . Researchers at Ethical Debuggers suggests you to take some steps in order to prevent yourself from these attacks:






