The phishing attacks are the most widely spread attacks all over the world today. But we all must take precautionary steps in order to escape from phishing attacks. Some preventive measures include:
- Not clicking on links from untrusted sources
- Surfing the internet from a secure network
- Not telling our credentials to anyone
But what if all the above mentioned precautions got compromised? This has been caught by researchers from Chekpoint. In the recent times, checkpoint researched a malicious campaign in which the bad actor uses the name and fame of Samsung,Oxford,Adobe to exploit the trust of the end user. In this phishing campaign the bad actor uses a redirected link under the domain name of Samsung with TLD from Canada which is hosted on Adobe server and then they redirect the victim to their compromised website which is behaving as an official Office 365 page. The backbone of this attack is the domain name they used as the redirected link in their phishing emails. These open redirects are by big giants like Google and Adobe ,is being used for bad purposes rather than for their actual purpose i.e. launching advertisements campaigns ,as the end user is unaware of the fact that on which official website he/she will land to. For example, Google has a well known open redirect at the URL https://www.google.com/url?q=[url]. The Google branding on the domain name will make you trust on this URL and you will land into a page that may or may not be a trusted web page. This similar technique is being used by some bad actors.
Let’s anlayse this attack.
ANATOMY OF THE ATTACK
This is a phishing attack and it starts when the attacker sends a phishing email to the victim. This phishing emails comes from an Oxford SMTP server which is compromised by the hackers. The attackers send a phishing e-mail from NordVPN with IP address 194.35.233.10 by relaying it through an Oxford server to the victim. The phishing email imitates an official Office 365 E-mail which contains a clickable button that redirects the victim to the target website.
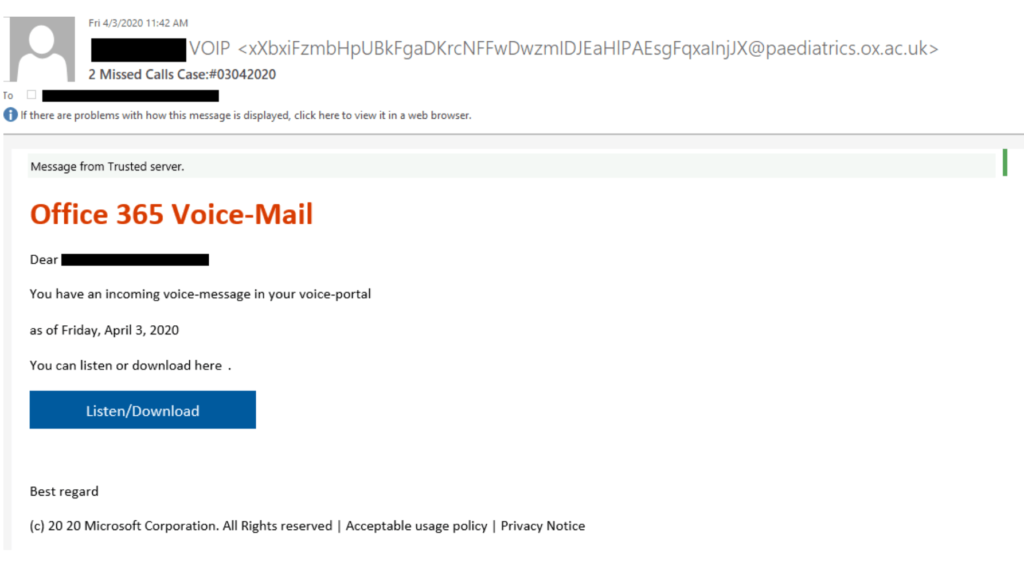
As soon as the attacker clicks on the button, the whole attack initiates. The further attack process in two stages:
- Firstly, the victim will be redirected to a website to a subdomain of Samsung Canada- t.email1.samsung.ca which is hosted on Adobe Servers. This domain was used by the Samsung during its 2018 Cyber Monday themed email campaign. The full redirection link is as follows http://t.email1.samsung.ca/r/?id=hf1b346f,303d531,303d53e&p1=8107023398&p2=8107023398&p3=DM15290&p4=http://www.samsung.com/ca/?mkm_rid=8107023398&mkm_mid=DM15290&cid=ca_email_newsletter_holidaycybermonday_20181126_fr-x-x-viewproducts-x-x. This is the method used by Adobe to campaign Samsung during its promotion and because this campaign server is left public by the company, bad actors uses this for their own purpose.
- Secondly, after being redirected to the Samsung’s site, the victim is again redirected to another website which is compromised by the hackers.
How simple is the attack, right? Just using a brand name compromises with transparency between original and fake.
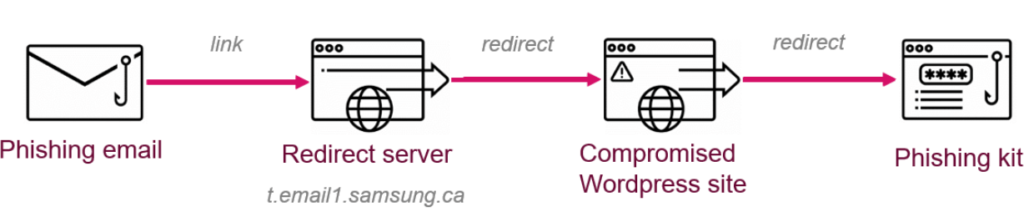
As soon as these two processes get finished, the victim now finally lands to the compromised site. This compromised site is has a phishing kit running at its back end that makes a phishing login page exactly as that of Microsoft 365.
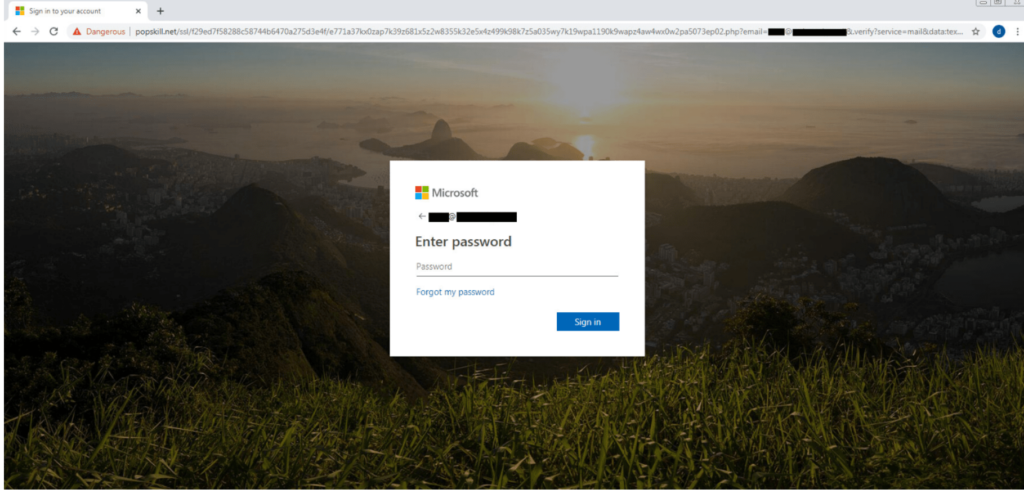
As soon as the victim enter his credentials , all the credentials will get compromised by the attackers.
CONCLUSION
We saw in the above example that how attackers use famous brand domain names which makes the victim unaware of the reality . This technique uses obfuscation which makes it difficult for the end user to identify the authenticity of the web page.
What should we do to prevent us from this attack? Search Engine Google has already blocked this domain.
There are some precautionary steps you can still take to prevent this attack:
- As you can see in the above screenshot of the mail received to the victim, the format of the official email send by the Microsoft is different as indicated from “Message from trusted source”. This is the big indication. Don’t open any links which have even slightly different format.
- If you have doubts about clicking on the link in the received email , check the URL on VirusTotal.
- Use private relay like Firefox relay to not release your official email on any website you visit.
- Always check the URL of the end page in which you are entering your credentials.






