The word that frighten us the most in this cyber world is Ransomware! All big enterprises try to protect themselves from this but bad actors are always a step ahead which give end results as data breach to the organization. There are lots of Ransomware groups which run affiliates in the underground. Some names for popular group out there are the Sodinokibi aka Revil, Avadddon, Maze, Thanos and more. These all ransomware operators are run by the professional experts behind them but due to their deeds they are being regarded as unethical or bad actors. So discussing about the groups, researchers from Carbon Black Threat Analysis Unit (TAU) (a unit…
-
-
GAMING WEBSITE CAUGHT DELIVERING TROJANS
Have you ever been to a site which shows an advertisement stating that “This domain is up for sale.”? Answer must be Yes, everyone as visited such websites but by chance! Most probably, when you see such a website, you just exit from that URL and surf to another website. But some have other type of mind setup. We all know that how domain name plays an important role in SEO for your website. Infact, good domain name make the visitors come back to your website or sometime a domain name of yours might inspire someone. So, if you by chance reached a site which states that this domain is up…
-
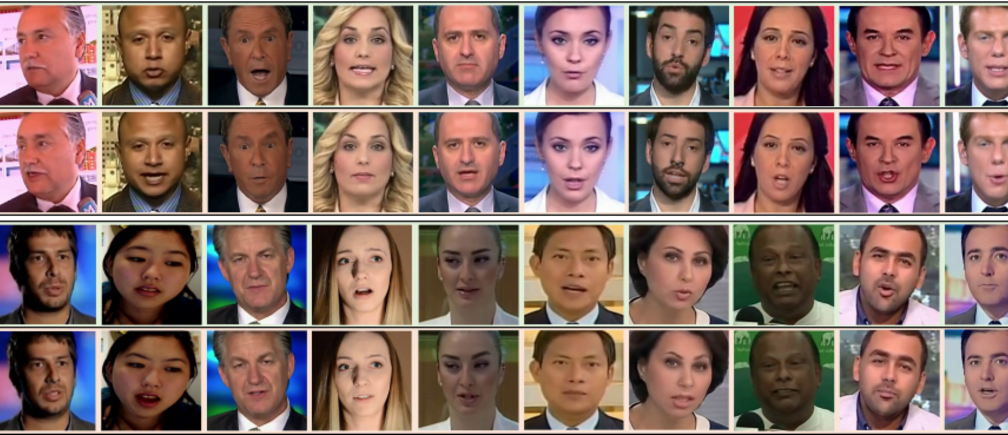
RESEARCHERS FOUND OUT AN ALGORITHM THAT DISRUPTS DEEPFAKES
In this worldwide lockdown, virtuality has over powered the reality . The ultimate drawback of this virtuality is that a person does not need to be present physically to mark his presence his picture or even his signature are enough to mark his presence. But the main point here is that Is virtual identity is enough to authenticate one’s identity? It’s a big NO. For instance, in many movies nowadays this technology is so common. To perform complex stunts, sometimes actors are not capable or for some reason they are not able to perform a particular scene in a movie, then using a technology known as Deepfake, it is possible…
-
SON OF STUXNET HAS BEEN BORN AS STAXNET
Who can forgot the Stuxnet. This is the cyberattack which actually got the inspiration for new generation of cybercriminals. This cyberattack was first discovered in 2010 by Sergey Ulasen. This virus was one of the targeted virus which takes almost 5 years to get developed. The Stuxnet is a virus whose history has been associated with one of the known cyberattack in Iranian in the nuclear program of Iran which is an another theory to be said that it is developed jointly by United States and Israel. It is a virus that directly targets programmable logic controllers (PLCs), which allow the automation of electromechanical processes such as those used to…
-
BYPASS OTP AND SMASH THIS LAYER OF SECURITY
It is easy to say that the best way to enhance your security is by adding an another layer of security to your resources but have you thought if that another layer got bypassed? Today many applications and banks worldwide deploy OTP(One Time Password) as one of the security layer to make it more harder for attackers to take the control of another user’s account. The OTP has another significance that it allows you to verify the identity of the user. The concept of OTP is simple. It is one time password that can be either alphanumeric or PIN numbers that is delivered to the verified user to authenticate it.…